-
OBP
- ABAC_Object_Properties_Reference
- ABAC_Parameters_Summary
- ABAC_Simple_Guide
- ABAC_Testing_Examples
- API
- API Collection
- API Tag
- API-Explorer-II-Help
- API.Access Control
- API.Interfaces
- API.Timeouts
- API.correlation_id
- ATM.atm_type
- ATM.attribute_id
- ATM.balance_inquiry_fee
- ATM.branch_identification
- ATM.cash_withdrawal_international_fee
- ATM.cash_withdrawal_national_fee
- ATM.has_deposit_capability
- ATM.is_accessible
- ATM.located_at
- ATM.location_categories
- ATM.minimum_withdrawal
- ATM.name
- ATM.notes
- ATM.services
- ATM.site_identification
- ATM.site_name
- Account
- Account Access
- Account.account_id
- Account.account_routing_address
- Account.account_routing_scheme
- Account.iban
- Account.owner
- Account.queryTagsExample
- Adapter.Akka.Intro
- Adapter.Stored_Procedure.Intro
- Adapter.authInfo
- Adapter.brand
- Adapter.card_attribute_id
- Adapter.card_attribute_name
- Adapter.card_attribute_value
- Adapter.card_id
- Adapter.card_number
- Adapter.card_type
- Adapter.cbsToken
- Adapter.cvv
- Adapter.expiry_month
- Adapter.expiry_year
- Adapter.issue_number
- Adapter.key
- Adapter.limit
- Adapter.name_on_card
- Adapter.offset
- Adapter.provider_id
- Adapter.serial_number
- Adapter.value
- Adaptive authentication
- Age
- Agent.agent_id
- Agent.agent_number
- ApiCollection.apiCollectionId
- ApiCollection.apiCollectionName
- ApiCollectionEndpoint.apiCollectionEndpointId
- ApiCollectionEndpoint.operationId
- Attribute.name
- Attribute.type
- Attribute.value
- Authentication
- Authentication Device (AD)
- Authentication.provider
- Authorization
- Available FAPI profiles
- Bank
- Bank.bank_id
- Bank.bank_id
- Bank.bank_routing_address
- Bank.bank_routing_scheme
- Branch
- Branch.branch_id
- Branch.branch_routing_address
- Branch.branch_routing_scheme
- CIBA
- CRL
- ChallengeAnswer.challengeId
- ChallengeAnswer.hashOfSuppliedAnswer
- ChallengeAnswer.suppliedAnswerExample
- Cheat Sheet
- Connector
- Connector Method
- ConnectorMethod.connectorMethodId
- Consent
- Consent_Account_Onboarding
- Consent_OBP_Flow_Example
- Consumer
- Consumer, Consent, Transport and Payload Security
- Consumer.consumer_key (Consumer Key)
- Consumption Device (CD)
- Counterparties
- Counterparty-Limits
- Counterparty.counterpartyId
- Counterparty.counterpartyName
- Counterparty.isBeneficiary
- Cross-Device Authorization
- Customer
- Customer.Credit.rating
- Customer.Credit.source
- Customer.attributeAlias
- Customer.attributeId
- Customer.attributeId
- Customer.attributeName
- Customer.attributeType
- Customer.attributeValue
- Customer.consumerId
- Customer.customerAccountLinkId
- Customer.customerAttributeId
- Customer.customerAttributeName
- Customer.customerAttributeType
- Customer.customerAttributeValue
- Customer.customerId
- Customer.customerNumber
- Customer.customer_id
- Customer.dependants
- Customer.dependents
- Customer.employmentStatus
- Customer.highestEducationAttained
- Customer.key
- Customer.kycStatus
- Customer.legalName
- Customer.mobileNumber
- Customer.nameSuffix
- Customer.relationshipStatus
- Customer.relationshipType
- Customer.secret
- Customer.title
- Customer.url
- DAuth
- Data Model Overview
- Direct Login
- Dummy Customer Logins
- Dynamic Endpoint Manage
- Dynamic Message Doc
- Dynamic Resource Doc
- Dynamic linking (PSD2 context)
- Dynamic-Entities
- Dynamic-Entity-Intro
- DynamicConnectorMethod.lang
- DynamicConnectorMethod.methodBody.Java
- DynamicConnectorMethod.methodBody.Js
- DynamicConnectorMethod.methodBody.scala
- DynamicMessageDoc.dynamicMessageDocId
- DynamicMessageDoc.inboundAvroSchema
- DynamicMessageDoc.outboundAvroSchema
- DynamicResourceDoc.description
- DynamicResourceDoc.dynamicResourceDocId
- DynamicResourceDoc.errorResponseBodies
- DynamicResourceDoc.exampleRequestBody
- DynamicResourceDoc.implementedInApiVersion
- DynamicResourceDoc.isFeatured
- DynamicResourceDoc.methodBody
- DynamicResourceDoc.partialFunction
- DynamicResourceDoc.partialFunctionName
- DynamicResourceDoc.partialFunctionName
- DynamicResourceDoc.requestUrl
- DynamicResourceDoc.requestVerb
- DynamicResourceDoc.specialInstructions
- DynamicResourceDoc.specifiedUrl
- DynamicResourceDoc.successResponseBody
- DynamicResourceDoc.summary
- Echo Request Headers
- Endpoint
- Endpoint Mapping
- EndpointTag.endpointTagId
- EndpointTag.tagName
- FAPI
- FAPI 1.0
- FAPI 2.0
- FX-Rates
- Gateway Login
- Hola App log trace
- How OpenID Connect Works
- JSON Schema Validation
- Just In Time Entitlements
- KYC (Know Your Customer)
- Keycloak Onboarding
- License.id
- License.name
- Message Doc
- Method Routing
- Multi-factor authentication (MFA)
- My-Dynamic-Entities
- OAuth 1.0a
- OAuth 2
- OAuth 2.0
- OAuth 2.0 Client Credentials Flow Manual
- OCSP
- OIDC
- OpenID Connect with Google
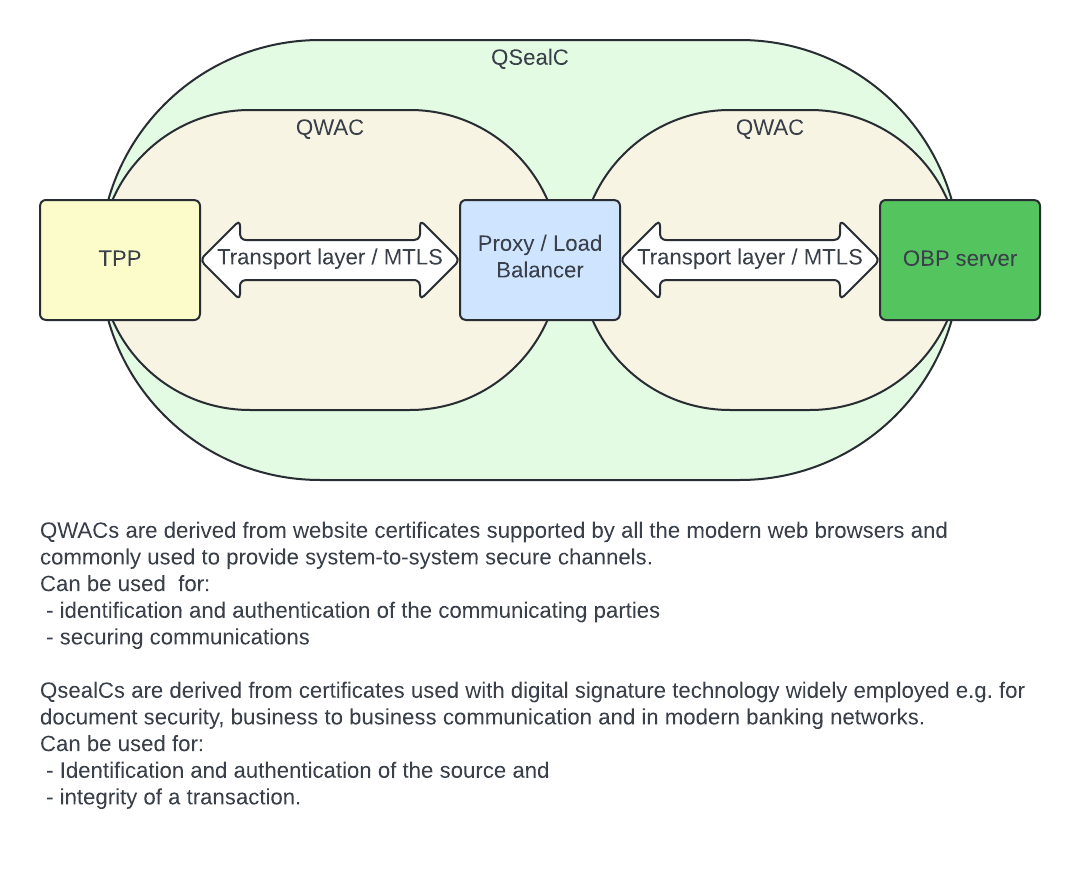
- QSealC
- QWAC
- Qualified Certificate Profiles (PSD2 context)
- Rate Limiting
- Regulated-Entities
- RegulatedEntity.attribute_id
- RegulatedEntity.attribute_name
- RegulatedEntity.attribute_type
- RegulatedEntity.attribute_value
- Risk-based authentication
- Roles of Open Bank Project
- Run via IntelliJ IDEA
- SCA (Strong Customer Authentication)
- Sandbox Introduction
- Scenario 1: Onboarding a User
- Scenario 2: Create a Public Account
- Scenario 3: Create counterparty and make payment
- Scenario 4: Grant account access to another User
- Scenario 5: Onboarding a User using Auth Context
- Scenario 6: Update credit score based on transaction and device data.
- Scenario 7: Onboarding a User with multiple User Auth Context records
- Space
- Static Endpoint
- TPP
- TPP Certificate Verification
- Template.attributeName
- Template.attributeType
- Transaction
- Transaction Requests
- Transaction Requests.Transaction Request Refund Reason Code
- Transaction Requests.Transaction Request Type
- Transaction Requests.attributeId
- Transaction Requests.attributeName
- Transaction Requests.attributeType
- Transaction Requests.attributeValue
- Transaction Requests.id
- Transaction request challenge threshold
- Transaction-Request-Introduction
- Transaction.attributeId
- Transaction.attributeName
- Transaction.attributeType
- Transaction.attributeValue
- Transaction.charge_policy
- Transaction.otherAccountProvider
- Transaction.transactionDescription
- Transaction.transactionId
- Transaction.transactionType
- User
- User Customer Links
- User.attributeName
- User.attributeType
- User.attributeValue
- User.isPersonal
- User.password
- User.provider
- User.provider_id
- User.userId
- User.userNameExample
- User.user_id
- User.username
- accessibility_features
- accessiblefeatures
- account
- account_application_id
- account_applications
- account_attribute_id
- account_attributes
- account_otp
- account_routing
- account_routings
- account_rules
- account_webhook_id
- accounts
- active
- actual_date
- adapter_implementation
- address
- addresses
- age
- akka
- alias
- allowed_actions
- allowed_attempts
- allows
- answer
- api_version
- app_name
- app_type
- atm_id
- atms
- attribute_definition_id
- attribute_id
- attributes
- auth_context_update_id
- available_funds_request_id
- average_response_time
- bad_attempts_since_last_success_or_reset
- balance
- balance_id
- balance_type
- bank
- bank_code
- bank_id_pattern
- bank_routing
- bank_routings
- bankid
- banks
- basket_id
- bespoke
- bic
- branch_number
- branch_routing
- branch_routings
- branch_type
- branches
- cache
- calls_made
- can_add_comment
- can_add_corporate_location
- can_add_counterparty
- can_add_image
- can_add_image_url
- can_add_more_info
- can_add_open_corporates_url
- can_add_physical_location
- can_add_private_alias
- can_add_public_alias
- can_add_tag
- can_add_transaction_request_to_any_account
- can_add_transaction_request_to_own_account
- can_add_url
- can_add_where_tag
- can_be_seen_on_views
- can_create_direct_debit
- can_create_standing_order
- can_delete_comment
- can_delete_corporate_location
- can_delete_image
- can_delete_physical_location
- can_delete_tag
- can_delete_where_tag
- can_edit_owner_comment
- can_query_available_funds
- can_see_bank_account_balance
- can_see_bank_account_bank_name
- can_see_bank_account_credit_limit
- can_see_bank_account_currency
- can_see_bank_account_iban
- can_see_bank_account_label
- can_see_bank_account_national_identifier
- can_see_bank_account_number
- can_see_bank_account_owners
- can_see_bank_account_routing_address
- can_see_bank_account_routing_scheme
- can_see_bank_account_swift_bic
- can_see_bank_account_type
- can_see_bank_routing_address
- can_see_bank_routing_scheme
- can_see_comments
- can_see_corporate_location
- can_see_image_url
- can_see_images
- can_see_more_info
- can_see_open_corporates_url
- can_see_other_account_bank_name
- can_see_other_account_iban
- can_see_other_account_kind
- can_see_other_account_metadata
- can_see_other_account_national_identifier
- can_see_other_account_number
- can_see_other_account_routing_address
- can_see_other_account_routing_scheme
- can_see_other_account_swift_bic
- can_see_other_bank_routing_address
- can_see_other_bank_routing_scheme
- can_see_owner_comment
- can_see_physical_location
- can_see_private_alias
- can_see_public_alias
- can_see_tags
- can_see_transaction_amount
- can_see_transaction_balance
- can_see_transaction_currency
- can_see_transaction_description
- can_see_transaction_finish_date
- can_see_transaction_metadata
- can_see_transaction_other_bank_account
- can_see_transaction_start_date
- can_see_transaction_this_bank_account
- can_see_transaction_type
- can_see_url
- can_see_where_tag
- cancelled
- card_attributes
- card_description
- cards
- category
- certificate_authority_ca_owner_id
- challenge
- challenge_type
- channel
- charge
- checks
- city
- client_id (Client ID)
- closing_time
- code
- collected
- collection_code
- comment_id
- comments
- company
- completed
- connector_name
- connector_version
- consent_id
- consent_id
- consent_request_id
- consents
- consumers
- contact_details
- conversion_value
- corporate_location
- count
- counterparties
- counterparty
- counterparty_limit_id
- country
- country_code
- county
- created
- created_by_user
- created_by_user_id
- creator
- credit_limit
- credit_rating
- creditoraccount
- creditorname
- crm_events
- current_credit_documentation
- current_state
- customer
- customer_address_id
- customer_attributes
- customer_name
- customer_token
- customer_user_id
- customers
- data.bankid
- date_activated
- date_added
- date_inserted
- date_of_application
- debtoraccount
- dependent_endpoints
- description
- detail
- details
- developer_email
- direct_debit_id
- display_name
- distribution_channel
- dob_of_dependants
- document_number
- documents
- domain
- drive_up
- driveup
- duration
- duration_time
- e
- effective_date
- elastic_search
- email_address
- enabled
- end_date
- energy_source
- entitlement_id
- entitlement_request_id
- entitlement_requests
- entitlements
- entity_address
- entity_certificate_public_key
- entity_code
- entity_country
- entity_id
- entity_name
- entity_post_code
- entity_town_city
- entity_type
- entity_web_site
- errorCode
- everything
- example_inbound_message
- example_outbound_message
- execution_date
- execution_time
- face_image
- family
- field
- first_check_number
- first_name
- free_form
- frequency
- friday
- from
- from_currency_code
- from_date
- from_department
- from_person
- full_name
- function_name
- future_date
- generate_accountants_view
- generate_auditors_view
- generate_public_view
- glossary_items
- group
- handle
- hide_metadata_if_alias_used
- holder
- holders
- hosted_at
- hosted_by
- hours
- how
- html
- http_method
- http_protocol
- id
- id
- image_id
- image_url
- images
- implemented_by_partial_function
- implemented_in_version
- inbound_topic
- inboundavroschema
- index
- instructedamount
- inverse_conversion_value
- invitees
- is_active
- is_alias
- is_bank_id_exact_match
- is_firehose
- is_public
- issue_place
- items
- jsonstring
- jwks_uri
- jwks_uris
- jwt
- keys
- kid
- kind
- kty
- kyc_check_id
- kyc_document
- kyc_document_id
- kyc_media_id
- last_failure_date
- last_lock_date
- last_name
- last_ok_date
- latitude
- license
- line1
- line2
- line3
- link
- list
- lobby
- location
- log_level
- logo
- logo_url
- longitude
- markdown
- match_all
- max_monthly_amount
- max_number_of_monthly_transactions
- max_number_of_transactions
- max_number_of_yearly_transactions
- max_single_amount
- max_total_amount
- max_yearly_amount
- maximum_response_time
- medias
- meeting_id
- meetings
- member_product_code
- message
- message_docs
- message_format
- messages
- meta
- metadata
- metadata_view
- method_name
- method_routing_id
- method_routings
- metrics
- minimum_response_time
- mobile_phone
- mobile_phone_number
- monday
- more_info
- more_info_url
- n
- name
- narrative
- national_identifier
- networks
- new_balance
- nickname
- nominal_interest1
- nominal_interest2
- none
- number
- number_of_checkbooks
- ok
- on_hot_list
- open_corporates_url
- opening_time
- order
- order_date
- order_id
- orders
- organisation
- organisation_website
- other_account
- other_account_id
- other_account_routing_address
- other_account_routing_scheme
- other_account_secondary_routing_address
- other_account_secondary_routing_scheme
- other_accounts
- other_bank_routing_address
- other_bank_routing_scheme
- other_branch_routing_address
- other_branch_routing_scheme
- outbound_topic
- outboundavroschema
- overall_balance
- overall_balance_date
- owners
- parameters
- parent_product
- parent_product_code
- payload
- paymentService
- per_day
- per_day_call_limit
- per_hour
- per_hour_call_limit
- per_minute
- per_minute_call_limit
- per_month
- per_month_call_limit
- per_second
- per_second_call_limit
- per_week
- per_week_call_limit
- permissions
- phone
- phone_number
- physical_location
- pin_reset
- ports
- post_code
- postcode
- posted
- present
- private_alias
- process
- product_attribute_id
- product_attributes
- product_code
- product_collection
- product_fee_id
- product_name
- products
- property
- provider
- provider_id
- public_alias
- purpose
- purpose_id
- query
- rank_amount1
- rank_amount2
- reason_requested
- reasons
- redirect_url
- relates_to_kyc_check_id
- relates_to_kyc_document_id
- replacement
- request_id
- requested_current_rate_amount1
- requested_current_rate_amount2
- requested_current_valid_end_date
- requested_temporary_valid_end_date
- require_scopes_for_all_roles
- require_scopes_for_listed_roles
- requiredfieldinfo
- requires_bank_id
- reset_in_seconds
- reset_password_url
- result
- revoked
- role
- role_name
- roles
- sandbox_tan
- satisfied
- saturday
- sca_method
- scheduled_date
- scheme
- scope_id
- scopes
- sepa
- sepaB2b
- sepaCardClearing
- sepaCreditTransfer
- sepaDirectDebit
- sepaSddCore
- service_available
- services
- settlement_accounts
- shipping_code
- short_code
- short_name
- short_reference
- shortcode
- sms
- staff_name
- staff_token
- staff_user_id
- standing_order_id
- state
- status
- status
- statuses
- success
- suggested_order
- summary
- sunday
- super_family
- supported_currencies
- supported_languages
- swift_bic
- tag_id
- tags
- tax_number
- tax_residence
- tax_residence_id
- technology
- temporary_credit_documentation
- temporary_requested_current_amount
- terms_and_conditions_url_example
- text
- this_account
- this_account_id
- this_bank_id
- this_view_id
- thursday
- time_to_live
- to
- to_counterparty
- to_currency_code
- to_date
- to_sandbox_tan
- to_sepa
- to_sepa_credit_transfers
- to_transfer_to_account
- to_transfer_to_atm
- to_transfer_to_phone
- token
- top_apis
- top_consumers
- transaction_attributes
- transaction_ids
- transaction_request_types
- transaction_requests_with_charges
- transaction_types
- transactions
- transfer_type
- transport
- trigger_name
- ttl_in_seconds
- tuesday
- type
- type_of_lock
- use
- use_type
- user
- user_auth_context_id
- user_auth_context_update_id
- user_auth_contexts
- user_customer_link_id
- user_customer_links
- users
- valid_from
- verb
- version
- version_status
- view
- view.description
- view.id
- view.is_system
- view.name
- views
- views_available
- views_basic
- vrp_consent_request.payload
- warehouse
- web_hooks
- web_ui_props_id
- website
- webui_props
- wednesday
- when
- where
- which_alias_to_use
API Glossary
ABAC_Object_Properties_Reference
ABAC Object Properties Reference
This document lists all properties available on objects passed to ABAC rules.
User Object
Available as: authenticatedUser, user, onBehalfOfUserOpt.get
Core Properties
user.userId // String - Unique user ID
user.emailAddress // String - User's email
user.name // String - Display name
user.provider // String - Auth provider
user.providerId // String - Provider's user ID
Usage Examples
// Check if user is admin
user.emailAddress.endsWith("@admin.com")
// Check specific user
user.userId == "alice@example.com"
BankAccount Object
Available as: accountOpt.get
Core Properties
account.accountId // AccountId - Account identifier
account.bankId // BankId - Bank identifier
account.accountType // String - Account type
account.balance // BigDecimal - Current balance
account.currency // String - Currency code (e.g., "EUR")
account.name // String - Account name
account.label // String - Account label
account.owners // List[User] - Account owners
Usage Examples
// Check balance
accountOpt.exists(_.balance.toDouble >= 1000.0)
// Check ownership
accountOpt.exists(account =>
account.owners.exists(owner => owner.userId == user.userId)
)
// Check currency
accountOpt.exists(_.currency == "EUR")
Bank Object
Available as: bankOpt.get
Core Properties
bank.bankId // BankId - Bank identifier
bank.shortName // String - Short name
bank.fullName // String - Full legal name
bank.logoUrl // String - URL to bank logo
bank.websiteUrl // String - Bank website URL
bank.bankRoutingScheme // String - Routing scheme
bank.bankRoutingAddress // String - Routing address
Usage Examples
// Check specific bank
bankOpt.exists(_.bankId.value == "gh.29.uk")
// Check bank by routing
bankOpt.exists(_.bankRoutingScheme == "SWIFT_BIC")
Transaction Object
Available as: transactionOpt.get
Core Properties
transaction.id // TransactionId - Transaction ID
transaction.amount // BigDecimal - Transaction amount
transaction.currency // String - Currency code
transaction.description // String - Description
transaction.startDate // Option[Date] - Posted date
transaction.finishDate // Option[Date] - Completed date
transaction.transactionType // String - Transaction type
Usage Examples
// Check transaction amount
transactionOpt.exists(tx => tx.amount.abs.toDouble < 100.0)
// Check transaction type
transactionOpt.exists(_.transactionType == "SEPA")
Customer Object
Available as: customerOpt.get
Core Properties
customer.customerId // String - Customer ID
customer.customerNumber // String - Customer number
customer.legalName // String - Legal name
customer.mobileNumber // String - Mobile number
customer.email // String - Email address
customer.dateOfBirth // Date - Date of birth
Usage Examples
// Check customer email domain
customerOpt.exists(_.email.endsWith("@company.com"))
Attribute Objects
UserAttributeTrait
attr.name // String - Attribute name
attr.value // String - Attribute value
attr.attributeType // UserAttributeType - Type of attribute
Usage Example
// Check for specific non-personal attribute
authenticatedUserAttributes.exists(attr =>
attr.name == "department" && attr.value == "finance"
)
// Note: User attributes in ABAC rules only include non-personal attributes
// (where IsPersonal=false). Personal attributes are not available for
// privacy and GDPR compliance reasons.
Related Documentation:
- ABAC_Simple_Guide - Getting started guide
- ABAC_Parameters_Summary - Complete parameter list
ABAC_Parameters_Summary
ABAC Rule Parameters Summary
The ABAC Rules Engine provides 18 parameters to your rule function, organized into three categories:
User Parameters (6 parameters)
- authenticatedUser: User - The logged-in user
- authenticatedUserAttributes: List[UserAttributeTrait] - Non-personal attributes of authenticated user (IsPersonal=false)
- authenticatedUserAuthContext: List[UserAuthContext] - Auth context of authenticated user
- onBehalfOfUserOpt: Option[User] - User being acted on behalf of (if provided)
- onBehalfOfUserAttributes: List[UserAttributeTrait] - Non-personal attributes of on-behalf-of user (IsPersonal=false)
- onBehalfOfUserAuthContext: List[UserAuthContext] - Auth context of on-behalf-of user
Target User Parameters (3 parameters)
- userOpt: Option[User] - Target user being evaluated
- userAttributes: List[UserAttributeTrait] - Non-personal attributes of target user (IsPersonal=false)
- user: User - Resolved target user (defaults to authenticatedUser)
Resource Context Parameters (9 parameters)
- bankOpt: Option[Bank] - Bank context (if bank_id provided)
- bankAttributes: List[BankAttributeTrait] - Bank attributes
- accountOpt: Option[BankAccount] - Account context (if account_id provided)
- accountAttributes: List[AccountAttribute] - Account attributes
- transactionOpt: Option[Transaction] - Transaction context (if transaction_id provided)
- transactionAttributes: List[TransactionAttribute] - Transaction attributes
- transactionRequestOpt: Option[TransactionRequest] - Transaction request context
- transactionRequestAttributes: List[TransactionRequestAttributeTrait] - Transaction request attributes
- customerOpt: Option[Customer] - Customer context (if customer_id provided)
- customerAttributes: List[CustomerAttribute] - Customer attributes
Usage in Rules
// Access user email
authenticatedUser.emailAddress
// Check if account exists and has sufficient balance
accountOpt.exists(account => account.balance.toDouble >= 1000.0)
// Check user attributes (non-personal only)
authenticatedUserAttributes.exists(attr =>
attr.name == "role" && attr.value == "admin"
)
// Note: Only non-personal attributes (IsPersonal=false) are included
// Check delegation
onBehalfOfUserOpt.isDefined
Related Documentation:
- ABAC_Simple_Guide - Getting started guide
- ABAC_Object_Properties_Reference - Detailed property reference
ABAC_Simple_Guide
ABAC Rules Engine - Simple Guide
Overview
The ABAC (Attribute-Based Access Control) Rules Engine allows you to create dynamic access control rules in Scala that evaluate whether a user should have access to a resource.
API Usage
Endpoint
POST https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/{RULE_ID}/execute
Request Example
curl -X POST \
'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/admin-only-rule/execute' \
-H 'Authorization: DirectLogin token=eyJhbGciOiJIUzI1...' \
-H 'Content-Type: application/json' \
-d '{
"bank_id": "gh.29.uk",
"account_id": "8ca8a7e4-6d02-48e3-a029-0b2bf89de9f0"
}'
Understanding the Three User Parameters
1. authenticatedUserId (Required)
The person actually logged in and making the API call
- The real user who authenticated
- Retrieved from the authentication token
2. onBehalfOfUserId (Optional)
When someone acts on behalf of another user (delegation)
- Used for delegation scenarios
- The authenticated user is acting for someone else
- Common in customer service, admin tools, power of attorney
3. userId (Optional)
The target user being evaluated by the rule
- Defaults to
authenticatedUserIdif not provided - The user whose permissions/attributes are being checked
- Useful for testing rules for different users
Writing ABAC Rules
Simple Rule Examples
Rule 1: User Must Own Account
accountOpt.exists(account =>
account.owners.exists(owner => owner.userId == user.userId)
)
Rule 2: Admin or Owner
val isAdmin = authenticatedUser.emailAddress.endsWith("@admin.com")
val isOwner = accountOpt.exists(account =>
account.owners.exists(owner => owner.userId == user.userId)
)
isAdmin || isOwner
Rule 3: Account Balance Check
accountOpt.exists(account => account.balance.toDouble >= 1000.0)
Available Objects in Rules
authenticatedUser: User // The logged in user
onBehalfOfUserOpt: Option[User] // User being acted on behalf of (if provided)
user: User // The target user being evaluated
bankOpt: Option[Bank] // Bank context (if bank_id provided)
accountOpt: Option[BankAccount] // Account context (if account_id provided)
transactionOpt: Option[Transaction] // Transaction context (if transaction_id provided)
customerOpt: Option[Customer] // Customer context (if customer_id provided)
Related Documentation:
- ABAC_Parameters_Summary - Complete list of all 18 parameters
- ABAC_Object_Properties_Reference - Detailed property reference
- ABAC_Testing_Examples - More testing examples
ABAC_Testing_Examples
ABAC Testing Examples
API Endpoint
POST https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/{RULE_ID}/execute
Example 1: Admin Only Rule
Rule Code:
authenticatedUser.emailAddress.endsWith("@admin.com")
Test Request:
curl -X POST \
'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/admin-only-rule/execute' \
-H 'Authorization: DirectLogin token=YOUR_TOKEN' \
-H 'Content-Type: application/json' \
-d '{}'
Expected Result:
- Admin user → {"result": true}
- Regular user → {"result": false}
Example 2: Account Owner Check
Rule Code:
accountOpt.exists(account =>
account.owners.exists(owner => owner.userId == user.userId)
)
Test Request:
curl -X POST \
'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/account-owner-only/execute' \
-H 'Authorization: DirectLogin token=YOUR_TOKEN' \
-H 'Content-Type: application/json' \
-d '{
"user_id": "alice@example.com",
"bank_id": "gh.29.uk",
"account_id": "8ca8a7e4-6d02-48e3-a029-0b2bf89de9f0"
}'
Example 3: Balance Check
Rule Code:
accountOpt.exists(account => account.balance.toDouble >= 1000.0)
Test Request:
curl -X POST \
'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/high-balance-only/execute' \
-H 'Authorization: DirectLogin token=YOUR_TOKEN' \
-H 'Content-Type: application/json' \
-d '{
"bank_id": "gh.29.uk",
"account_id": "8ca8a7e4-6d02-48e3-a029-0b2bf89de9f0"
}'
Example 4: Transaction Amount Check
Rule Code:
transactionOpt.exists(tx => tx.amount.abs.toDouble < 100.0)
Test Request:
curl -X POST \
'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/small-transactions/execute' \
-H 'Authorization: DirectLogin token=YOUR_TOKEN' \
-H 'Content-Type: application/json' \
-d '{
"bank_id": "gh.29.uk",
"account_id": "8ca8a7e4-6d02-48e3-a029-0b2bf89de9f0",
"transaction_id": "trans-123"
}'
Testing Patterns
Pattern 1: Test Different Users
# Test for admin
curl -X POST 'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/RULE_ID/execute' \
-d '{"user_id": "admin@admin.com", "bank_id": "gh.29.uk"}'
# Test for regular user
curl -X POST 'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/RULE_ID/execute' \
-d '{"user_id": "alice@example.com", "bank_id": "gh.29.uk"}'
Pattern 2: Test Edge Cases
# No context (minimal)
curl -X POST 'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/RULE_ID/execute' -d '{}'
# Full context
curl -X POST 'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/RULE_ID/execute' -d '{
"user_id": "alice@example.com",
"bank_id": "gh.29.uk",
"account_id": "8ca8a7e4-6d02-48e3-a029-0b2bf89de9f0",
"transaction_id": "trans-123",
"customer_id": "cust-456"
}'
Common Errors
Error 1: Rule Not Found
curl -X POST 'https://apisandbox.openbankproject.com/obp/v6.0.0/management/abac-rules/nonexistent-rule/execute' \
-H 'Authorization: DirectLogin token=YOUR_TOKEN' \
-d '{}'
Response: {"error": "ABAC Rule not found with ID: nonexistent-rule"}
Error 2: Invalid Context
Response: Objects will be None if IDs are invalid, rule should handle gracefully
Related Documentation:
- ABAC_Simple_Guide - Getting started guide
- ABAC_Parameters_Summary - Complete parameter list
- ABAC_Object_Properties_Reference - Property reference
API
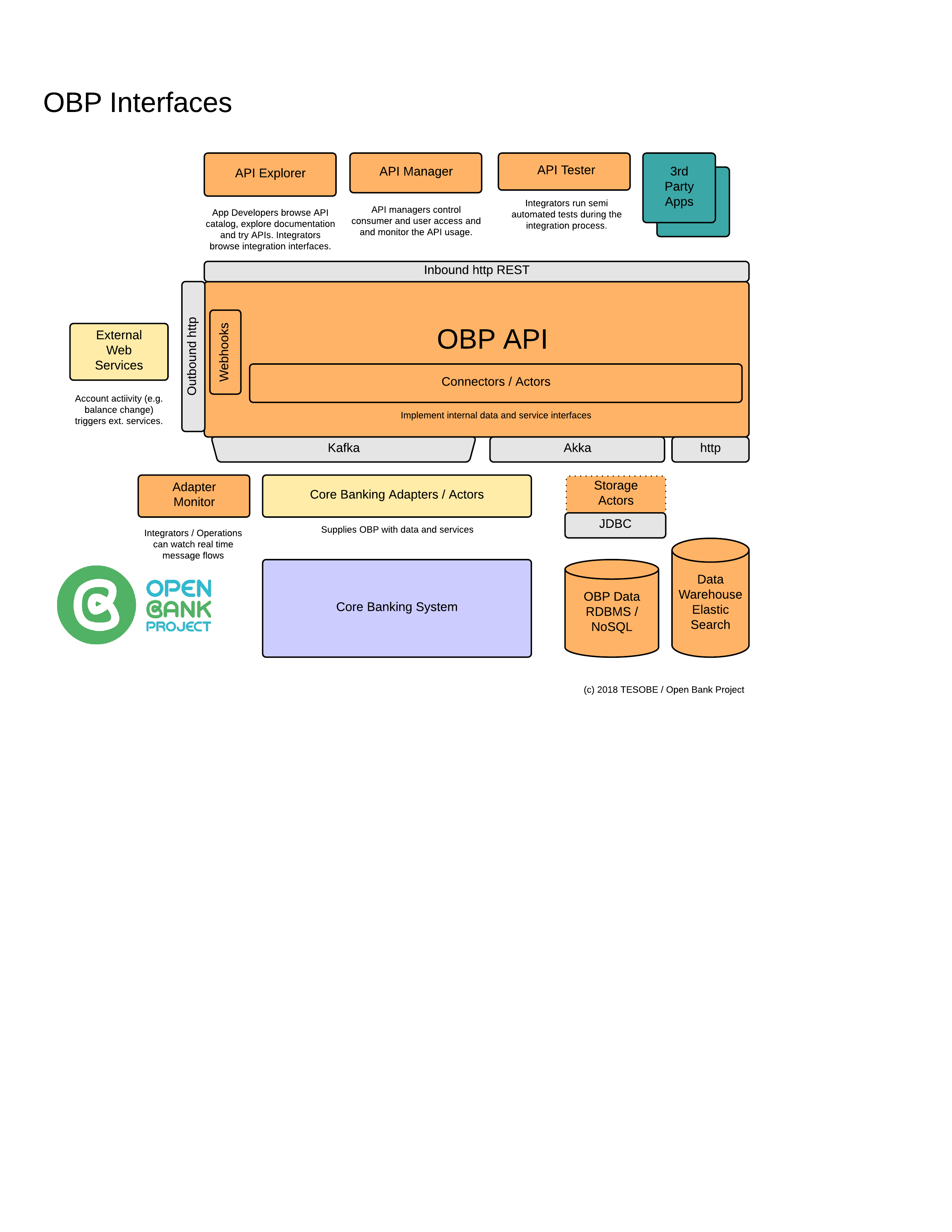
The terms API (Application Programming Interface) and Endpoint are used somewhat interchangeably.
However, an API normally refers to a group of Endpoints.
An endpoint has a unique URL path and HTTP verb (GET, POST, PUT, DELETE etc).
When we POST a Swagger file to the Create Endpoint endpoint, we are in fact creating a set of Endpoints that have a common Tag. Tags are used to group Endpoints in the API Explorer and filter the Endpoints in the Resource Doc endpoints.
Endpoints can also be grouped together in Collections.
See also Endpoint
API Collection
An API Collection is a collection of endpoints grouped together for a certain purpose.
Having read access to a Collection does not constitute execute access on the endpoints in the Collection.
(Execute access is governed by Entitlements to Roles - and in some cases, Views.)
Collections can be created and shared. You can make a collection non-sharable but the default is sharable.
Your "Favourites" in API Explorer is actually a collection you control named "Favourites".
To share a Collection (e.g. your Favourites) just click on your Favourites in the API Explorer and share the URL in the browser. If you want to share the Collection via an API, just share the collection_id with a developer.
If you share a Collection it can't be modified by anyone else, but anyone can use it as a basis for their own Favourites or another collection.
There are over 13 endpoints for controlling Collections.
Some of these endpoints require Entitlements to Roles and some operate on your own personal collections such as your favourites.
API-Explorer-II-Help
API Explorer II - How to Use
API Explorer II is an interactive Swagger/OpenAPI interface for discovering and testing OBP and other standard endpoints.
Key Features
- Browse and search all available API endpoints
- Execute API calls directly from your browser
- View request and response examples
- Test authentication and authorization flows
Finding Dynamic Entities
Dynamic Entities can be found under the More list of API Versions. Look for versions starting with OBPdynamic-entity or similar in the version selector.
For more information about Dynamic Entities see here
Creating Favorites
If you click the star icon next to an endpoint, it will be added to your favorites list.
Favorites appear in the Collections section in the left panel interface.
Note: Favorites are a special type of collection. You can create other collections using endpoints.
API.Access Control
Access Control is achieved via the following mechanisms in OBP:
-
APIs are enabled in Props. See the README.md
-
Consumers (AKA Clients or Apps) are granted access to Roles and Views via Scopes
See here for related endpoints and documentation.
- Users are granted access to System or Bank Roles via Entitlements.
See here for related endpoints and documentation.
Users may request Entitlement Requests here
Entitlements and Entitlement Requests can be managed in the OBP API Manager.
- Users are granted access to Customer Accounts, Transactions and Payments via Views.
See here for related endpoints and documentation.
User Views can be managed via the OBP Sofit Consent App.

API.correlation_id
Example value: 1flssoftxq0cr1nssr68u0mioj
Description: A string generated by OBP-API that MUST uniquely identify the API call received by OBP-API. Used for debugging and logging purposes. It is returned in header to the caller.
ATM.attribute_id
Example value: atme-9a0f-4bfa-b30b-9003aa467f51
Description: A string that MUST uniquely identify the ATM on this OBP instance.
Account
The thing that tokens of value (money) come in and out of.
An account has one or more owners which are Users.
In the future, Customers may also be owners.
An account has a balance in a specified currency and zero or more transactions which are records of successful movements of money.
Account Access
Account Access governs access to Bank Accounts by end Users. It is an intersecting entity between the User and the View Definition.
A User must have at least one Account Access record record in order to interact with a Bank Account over the OBP API.
Account.account_id
An identifier for the account that MUST NOT leak the account number or other identifier nomrally used by the customer or bank staff.
It SHOULD be a UUID. It MUST be unique in combination with the BANK_ID. ACCOUNT_ID is used in many URLS so it should be considered public.
(We do NOT use account number in URLs since URLs are cached and logged all over the internet.)
In local / sandbox mode, ACCOUNT_ID is generated as a UUID and stored in the database.
In non sandbox modes (RabbitMq etc.), ACCOUNT_ID is mapped to core banking account numbers / identifiers at the South Side Adapter level.
ACCOUNT_ID is used to link Metadata and Views so it must be persistant and known to the North Side (OBP-API).
Example value: 8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0
Account.account_routing_address
Example value: DE91 1000 0000 0123 4567 89
Description: An identifier that conforms to account_routing_scheme / accountRoutingScheme
Account.account_routing_scheme
Example value: IBAN
Description: The scheme that the account_routing_address / accountRoutingAddress is an example of.
Account.iban
Example value: DE91 1000 0000 0123 4567 89
Description: MUST uniquely identify the bank account globally.
Account.queryTagsExample
Example value: Card,Debit
Description: This field is only used for OBP to distinguish the debit accounts, card accounts ...
Adapter.Akka.Intro
Use Akka as an interface between OBP and your Core Banking System (CBS).
For an introduction to Akka see here
The OBP Akka interface allows integrators to write Java or Scala Adapters (any JVM language with Akka support)
respond to requests for data and services from OBP.
For the message definitions see here
Installation Prerequisites
-
You have OBP-API running.
-
Ideally you have API Explorer running (the application serving this page) but its not necessary - you could use any other REST client.
- You might want to also run API Manager as it makes it easier to grant yourself roles, but its not necessary - you could use the API Explorer / any REST client instead.
Create a Customer User and an Admin User
- Register a User who will use the API as a Customer.
- Register another User that will use the API as an Admin. The Admin user will need some Roles. See here. You can bootstrap an Admin user by editing the Props file. See the README for that.
Add some authentication context to the Customer User
- As the Admin User, use the Create Auth Context endpoint to add one or more attributes to the Customer User.
For instance you could add the name/value pair CUSTOMER_NUMBER/889763 and this will be sent to the Adapter / CBS inside the AuthInfo object.
Now you should be able to use the Get Auth Contexts endpoint to see the data you added.
Write or Build an Adapter to respond to the following messages.
When getting started, we suggest that you implement the messages in the following order:
1) Core (Prerequisites) - Get Adapter, Get Banks, Get Bank
Now you should be able to use the Adapter Info endpoint
Now you should be able to use the Get Banks endpoint
Now you should be able to use the Get Bank endpoint
2) Get Customers by USER_ID
Now you should be able to use the Get Customers endpoint.
3) Get Accounts
The above messages should enable at least the following endpoints:
4) Get Account
The above message should enable at least the following endpoints:
5) Get Transactions
6) Manage Counterparties
7) Get Transaction Request Types
- This is configured using OBP Props - No messages required
This glossary item is Work In Progress.
Adapter.Stored_Procedure.Intro
Use Stored_Procedure as an interface between OBP and your Core Banking System (CBS).
For an introduction to Stored Procedures see here
Installation Prerequisites
- You have OBP-API running and it is connected to a stored procedure related database.
- Ideally you have API Explorer running (the application serving this page) but its not necessary - you could use any other REST client.
- You might want to also run API Manager as it makes it easier to grant yourself roles, but its not necessary - you could use the API Explorer / any REST client instead.
Adapter.authInfo
authInfo is a JSON object sent by the Connector to the Adapter so the Adapter and/or Core Banking System can
identify the User making the call.
The authInfo object contains several optional objects and fields.
Please see the Message Docs for your connector for the current JSON structure. The following serves as a guide:
- userId is the user_id as generated by OBP
- username can be chosen explicitly to match an existing customer number (not recommended)
- linkedCustomers is a list of Customers the User is explicitly linked to. Use the Create User Customer Link endpoint to populate this data.
- userAuthContexts may contain the customer number or other tokens in order to boot strap the User Customer Links
or provide an alternative method of tagging the User with an authorisation context.
Use the Create UserAuthContext endpoint to populate this data. - cbsToken is a token used by the CBS to identify the user's session. Either generated by the CBS or Gateway.
- isFirst is a flag that indicates that OBP should refresh the user's list of accounts from the CBS (and flush / invalidate any User's cache)
- correlationId just identifies the API call.
- authViews are entitlements given by account holders to third party users e.g. Sam may grant her accountant Jill read only access to her business account. See the Create View endpoint

Adapter.card_attribute_id
Example value: b4e0352a-9a0f-4bfa-b30b-9003aa467f50
Description: A string that MUST uniquely identify the card attribute on this OBP instance. It SHOULD be a UUID.
Adapter.card_attribute_name
Example value: OVERDRAFT_START_DATE
Description: The Card attribute name
Adapter.card_id
Example value: 36f8a9e6-c2b1-407a-8bd0-421b7119307e
Description: A string that MUST uniquely identify the card on this OBP instance. It SHOULD be a UUID.
Adapter.card_type
Example value: Credit
Description: The type of the physical card. eg: credit, debit ...
Adapter.cbsToken
Example value: FYIUYF6SUYFSD
Description: A token provided by the Gateway for use by the Core Banking System
Adapter.issue_number
Example value: 1
Description: The issue number of the physical card, eg 1,2,3,4 ....
Adapter.key
Example value: CustomerNumber
Description: This key should be used with Adapter.value together. They are a pair.
Adapter.provider_id
Example value: Chris
Description: The provider id of the user which is equivalent to the username. Used in combination with the provider name (host) to uniquely identify a User on OBP.
Adapter.serial_number
Example value: 1324234
Description: The serial number of the physical card, eg 1123.
Adapter.value
Example value: 5987953
Description: This key should be used with Adapter.key together. They are a pair.
Adaptive authentication
Adaptive authentication, also known as risk-based authentication, is dynamic in a way it automatically triggers additional authentication factors, usually via MFA factors, depending on a user's risk profile.
An example of this authentication at OBP-API side is the feature "Transaction request challenge threshold".
-
Agent.agent_id
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A non human friendly string that identifies the agent and is used in URLs. This SHOULD NOT be the agent number. The combination of agentId and bankId MUST be unique on an OBP instance. AgentId SHOULD be unique on an OBP instance. Ideally agentId is a UUID. A mapping between agent number and agent id is kept in OBP.
Agent.agent_number
Example value: 5987953
Description: The human friendly agent identifier that MUST uniquely identify the Agent at the Bank ID. Agent Number is NOT used in URLs.
ApiCollection.apiCollectionId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A string that MUST uniquely identify the session on this OBP instance, can be used in all cache.
ApiCollectionEndpoint.apiCollectionEndpointId
Example value: 8uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A string that MUST uniquely identify the session on this OBP instance, can be used in all cache.
ApiCollectionEndpoint.operationId
Example value: OBPv4.0.0-getBanks
Description: A uniquely identify the obp endpoint on OBP instance, you can get it from Get Resource endpoints.
Authentication
Authentication generally refers to a set of processes which result in a resource server (in this case, OBP-API) knowing about the User and/or Application that is making the http request it receives.
In most cases when we talk about authentication we are thinking about User authentication, e.g. the user J.Brown is requesting data from the API.
However, user authentication is pretty much always accompanied by knowledge of the Client AKA Consumer, TPP or Application.
In some cases, we only perform Client authentication which results in knowledge of the Application but not the human that is making the call. This is useful when we want to protect the identity of a user but still want to control access to the API.
In most cases, OBP-API server knows about at least two entities involved in the http request / call: The Client and the User - but it will also know about (and trust) the Identity Server (Provider) that authenticated the user and other elements in the chain of trust such as load balancers and certificate authorities.
In simple terms, there are two phases of the Authentication process:
1) The phase where an authorisation token is obtained.
2) The phase where an authorisation token is used.
Phase 1 is an exchange of credentials such as a username and password and possibly knowledge of a "second factor" for a token.
Phase 2 is the execution of an http call which contains the token in a "header" in exchange for some response data or some resource being created, update or deleted.
There are several methods of obtaining and using a token which vary in their ease of use and security.
Direct Login and OAuth 1.0a are used for testing purposes / local installations and are built into OBP.
OAuth2 / Open ID Connect (OIDC) depend on the configuration of Identity Provider solutions such as Keycloak or Hydra or external services such as Google or Yahoo.
Open Bank Project can support multiple identity providers per OBP instance. For example, for a single OBP installation, some Users could authenticate against Google and some could authenticate against a local identity provider.
In the cases where multiple identity providers are configured, OBP differentiates between Users by not only their Username but also by their "Identity Provider". i.e. J.Brown logged in via Google is distinct from J.Brown who logged in via a local OBP instance.
Phase 1 generally results in a temporary token i.e. a token that is valid for a limited amount of time e.g. 2 hours or 3 minutes.
Phase 1 might also result in a token that represents a subset of the User's full permissions. This token is generally called a Consent. i.e. a User might give consent for an application to access one of her accounts but not all of them. A Consent is generally given to a Client and bound to that Client i.e. no other application may use it.
Phase 2 results in OBP having identified a User record in the OBP database so that Authorisation can proceed.
Authentication Device (AD)
The device on which the user will authenticate and authorize the request, often a smartphone.
Authentication.provider
Example value: http://127.0.0.1:8080
Description: The host name of an Identity Provider authenticating a User. OBP allows the use of multiple simultanious authentication providers. The provider name (host) along with the provider id (a username or id) uniquely identifies a user on OBP.
Authorization
If Authentication involves the process of determining the identity of a user or application, Authorization involves the process of determining what the user or application can do.
In OBP, Endpoints are protected by "Guards".
There are two types of permissions which can be granted:
1) Entitlements to Roles provide course grained access to resources which are related to the OBP system or a bank / space e.g. CanCreateAtm would allow the holder to create an ATM record.
2) Account Access records provide fine grained permissions to customer bank accounts, their transactions and payments through Views. e.g. the A User with the Balances View on Account No 12345 would be allowed to get the balances on that account.
Both types of permissions can be encapsulated in Consents or other authentication mechanisms.
When OBP receives a call, after authentication is performed, OBP checks if the caller has sufficient permissions.
If an endpoint guard blocks a call due to insufficient permissions / authorization, OBP will return an OBP- error message.
If the caller passes the guards, the OBP-API forwards the request to the next step in the process.
Note: All OBP- error messages can be found in the OBP-API logs and OBP source code for debugging purposes.
Available FAPI profiles
The following are the FAPI profiles which are either in use by multiple implementers or which are being actively developed by the OpenID Foundation’s FAPI working group:
Bank
A Bank (aka Space) represents a financial institution, brand or organizational unit under which resources such as endpoints and entities exist.
Both standard entities (e.g. financial products and bank accounts in the OBP standard) and dynamic entities and endpoints (created by you or your organisation) can exist at the Bank level.
For example see Bank/Space level Dynamic Entities and Bank/Space level Dynamic Endpoints
The Bank is important because many Roles can be granted at the Bank level. In this way, it's possible to create segregated or partitioned sets of endpoints and data structures in a single OBP instance.
A User creating a Bank (if they have the right so to do), automatically gets the Entitlement to grant any Role for that Bank. Thus the creator of a Bank / Space becomes the "god" of that Bank / Space.
Basic attributes for the bank resource include identifying information such as name, logo and website.
Using the OBP endpoints for bank accounts it's possible to view accounts at one Bank or aggregate accounts from all Banks connected to the OBP instance.
See also Props settings named "brand".
Bank.bank_id
An identifier that uniquely identifies the bank or financial institution on the OBP-API instance.
It is typically a human (developer) friendly string for ease of identification.
It SHOULD NOT contain spaces.
In sandbox mode it typically has the form: "financialinstitutuion.sequencennumber.region.language". e.g. "bnpp-irb.01.it.it"
For production, it's value could be the BIC of the institution.
Example value: gh.29.uk
Bank.bank_id
Example value: gh.29.uk
Description: A string that MUST uniquely identify the bank on this OBP instance. It COULD be a UUID but is generally a short string that easily identifies the bank / brand it represents.
Bank.bank_routing_address
Example value: GENODEM1GLS
Description: An identifier that conforms to bank_routing_scheme / bankRoutingScheme
Bank.bank_routing_scheme
Example value: BIC
Description: The scheme that the bank_routing_address / bankRoutingAddress is an example of.
Branch
The bank branches, it contains the address, location, lobby, drive_up of the Branch.
Branch.branch_id
Example value: DERBY6
Description: Uniquely identifies the Branch in combination with the bankId.
Branch.branch_routing_address
Example value: DERBY6
Description: An address that conforms to branch_routing_scheme / branchRoutingScheme
Branch.branch_routing_scheme
Example value: BRANCH-CODE
Description: The scheme that the branch_routing_address / branchRoutingAddress is an example of.
CIBA
An acronym for Client-Initiated Backchannel Authentication.
For more details about it please take a look at the official specification: OpenID Connect Client Initiated Backchannel Authentication Flow
Please note it is a cross-device protocol and SHOULD not be used for same-device scenarios.
If the Consumption Device and Authorization Device are the same device, protocols like OpenID Connect Core OpenID.Core and OAuth 2.0 Authorization Code Grant as defined in RFC6749 are more appropriate.
CRL
Certificate Revocation List.
CRL issuers issue CRLs. The CRL issuer is either the CA (certification authority) or an entity that has been authorized by the CA to issue CRLs.
CAs publish CRLs to provide status information about the certificates they issued.
However, a CA may delegate this responsibility to another trusted authority.
It is described in RFC 5280.
ChallengeAnswer.challengeId
Example value: 123chaneid13-6d02-40e3-a129-0b2bf89de9f0
Description: MUST uniquely identify the challenge globally.
ChallengeAnswer.hashOfSuppliedAnswer
Example value: a665a45920422f9d417e4867efdc4fb8a04a1f3fff1fa07e998e86f7f7a27ae3
Description: Sha256 hash value of the ChallengeAnswer.challengeId
ChallengeAnswer.suppliedAnswerExample
Example value: 123456
Description: The value of the ChallengeAnswer.challengeId
Connector
In OBP, most internal functions / methods can have different implementations which follow the same interface.
These functions are called connector methods and their implementations.
The default implementation of the connector is the "mapped" connector.
It's called "mapped" because the default datasource on OBP is a relational database, and access to that database is always done through an Object-Relational Mapper (ORM) called Mapper (from a framework we use called Liftweb).
[=============] [============] [============] [.............] [ ] [ ] [...OBP API...] ===> OBP Endpoints call connector functions (aka methods) ===> [ Connector ] ===> [ Database ] [.............] The default implementation is called "Mapped" [ (Mapped) ] [ (Adapter) ] [=============] The Mapped Connector talks to a Database [============] [============]
However, there are multiple available connector implementations - and you can also mix and create your own.|
E.g. RabbitMq
[=============] [============] [============] [============] [============] [ ] [ ] [ ] [ ] [ ] [ OBP API ] ===> RabbitMq Connector ===> [ RabbitMq ] ===> [ RabbitMq ] [ OBP RabbitMq] ===> [ CBS ] [ ] Puts OBP Messages [ Connector ] [ Cluster ] [ Adapter ] [ ] [=============] onto a RabbitMq [============] [============] [============] [============]
You can mix and match them using the Star connector and you can write your own in Scala. You can also write Adapters in any language which respond to messages sent by the connector.
we use the term "Connector" to mean the Scala/Java/Other JVM code in OBP that connects directly or indirectly to the systems of record i.e. the Core Banking Systems, Payment Systems and Databases.
A "Direct Connector" is considered to be one that talks directly to the system of record or existing service layer.
i.e. API -> Connector -> CBS
An "Indirect Connector" is considered one which pairs with an Adapter which in turn talks to the system of record or service layer.
i.e. API -> Connector -> Adapter -> CBS
The advantage of a Direct connector is that its perhaps simpler. The disadvantage is that you have to code in a JVM language, understand a bit about OBP internals and a bit of Scala.
The advantage of the Indirect Connector is that you can write the Adapter in any language and the Connector and Adapter are decoupled (you just have to respect the Outbound / Inbound message format).
The default Connector in OBP is a Direct Connector called "mapped". It is called the "mapped" connector because it talks directly to the OBP database (Postgres, MySQL, Oracle, MSSQL etc.) via the Liftweb ORM which is called Mapper.
If you want to create your own (Direct) Connector you can fork any of the connectors within OBP.
There is a special Connector called the Star Connector which can use functions from all the normal connectors.
Using the Star Connector we can dynamically reroute function calls to different Connectors per function per bank_id.
The OBP API Manager has a GUI to manage this or you can use the OBP Method Routing APIs to set destinations for each function call.
Note: We generate the source code for individual connectors automatically.
Connector Method
Developers can override all the existing Connector methods.
This function needs to be used together with the Method Routing.
When we set "connector = internal", then the developer can call their own method body at API level.
For example, the GetBanks endpoint calls the connector "getBanks" method. Then, developers can use these endpoints to modify the business logic in the getBanks method body.
The following videos are available:
* Introduction for Connector Method
* Introduction 2 for Connector Method
ConnectorMethod.connectorMethodId
Example value: ace0352a-9a0f-4bfa-b30b-9003aa467f51
Description: A string that MUST uniquely identify the connector method on this OBP instance, can be used in all cache.
Consent
Consents provide a mechanism through which a resource owner (e.g. a customer) can grant a third party certain access to their resources.
The following are important considerations in Consent flows:
1) The privacy of the resource owner (the Customer or User) should be preserved.
This means that when a TPP first asks a User if they would like to provide their data, the user should not be authenticated.
Thus the start of the Consent process authenticates the Client (TPP) but not the User.
Authentication of the user comes later.
This endpoint initiates a consent in OBP
2) Consent finalisation often involves SCA.
Since a consent gives its holder privileges on the API, we need to make sure it is not created lightly, therefore some second factor of authentication is employed.
This endpoint finalises an OBP consent
3) A User should be able to list and revoke their consents.
This endpoint lists consents for the authenticated user.
This endpoint revokes a consent for the current user.
This gives the user visibility over the consents they have granted to various apps for various purposes and confidence they can stop the TPP acting for a certain purpose.
4) The consent manager should be able to list and revoke consents.
This is a management endpoint lists consents with various query parameters
This is a management endpoint to revoke a consent
The consent manager may want to list the consents by each Client or User and the ability to revoke individual consents (rather than disabling a client completely).
This requires that the resource server stores the CONSENT_ID and other information so that it can be disabled or queried.
However, the consent manager should not be able to see the CONSENT_ID since this would make it easier to actually use it.
5) A consent is bound to the application has created it.
The User gave consent to a certain application not any application.
6) The consent will have a limited life time.
The consent can become valid in the future and need not last forever.
7) The consent will be signed using JWT.
This increases the security of the claims contained in the consent.
See here for an example flow.
See here for more information about onboarding.
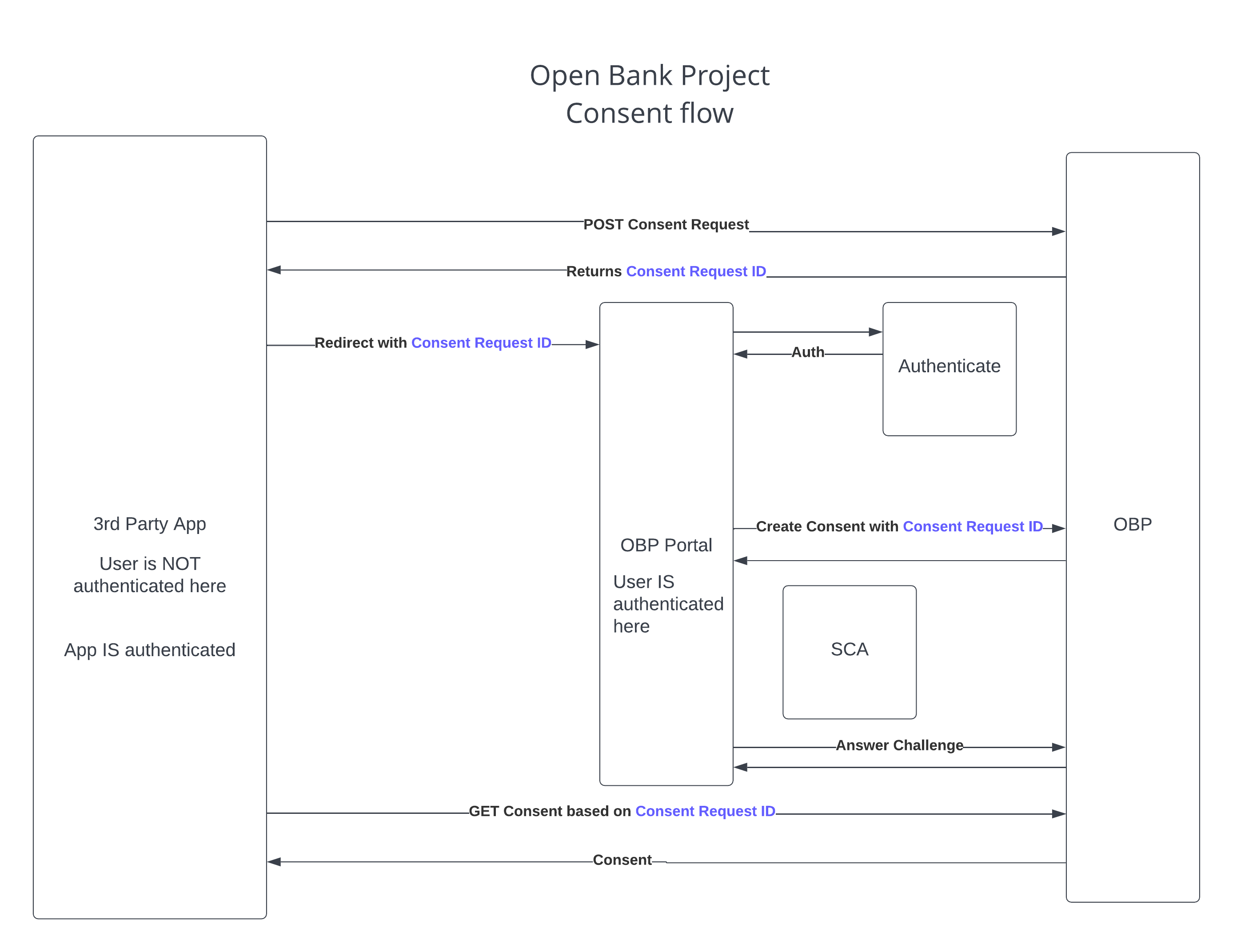
Consent_Account_Onboarding
Consent, or Account onboarding, is the process by which the account owner gives permission for their account(s) to be accessible to the API endpoints.
In OBP, the account, transaction and payment APIs are all guarded by Account Views - with one exception, the account holders endpoint which can be used to
bootstrap account on-boarding.
Note: the account holders endpoint is generally made available only to the Account Onboarding App, so if a View does not exist, no API access to the account is possible.
Consent or Account onboarding can be managed in one of two ways:
1) A backend system (CBS or other) is the system of record for User Consent, and OBP mirrors this.
In this case:
a) OBP requires the CBS or other backend system to return a list of accounts and permissions associated with a User.
b) At User login, OBP automatically creates one or more Views for that User based on the permissions supplied by the CBS.
2) OBP is the system of record for User Consent.
In this case:
a) OBP requires the CBS, Gateway or other system to provide just a basic list of accounts owned by the User.
b) The Onboarding App or Bank's Onboarding Page then authenticates the User and calls the Create View endpoint.
c) The account, transaction and payment API endpoints then work as moderated by the relevant View permissions.
d) The User can revoke access by calling the delete View endpoint.
In summary:
Prior to Views being created on an Account for a User, only the 'accounts held' endpoint will work for the account holder, and this endpoint only provides enough information
to identify the account so it can be selected and on-boarded into the API.
Once a View exists for an Account, a User can interact with the Account via the API based on permissions defined in the View.
Consent_OBP_Flow_Example
1) Call endpoint Create Consent Request using application access (Client Credentials)
Url: https://apisandbox.openbankproject.com/obp/v5.0.0/consumer/consent-requests
Post body:
{
"everything": false,
"account_access": [],
"entitlements": [
{
"bank_id": "gh.29.uk.x",
"role_name": "CanGetCustomersAtOneBank"
}
],
"email": "marko@tesobe.com"
}
Output:
{
"consent_request_id":"bc0209bd-bdbe-4329-b953-d92d17d733f4",
"payload":{
"everything":false,
"account_access":[],
"entitlements":[{
"bank_id":"gh.29.uk.x",
"role_name":"CanGetCustomersAtOneBank"
}],
"email":"marko@tesobe.com"
},
"consumer_id":"0b34068b-cb22-489a-b1ee-9f49347b3346"
}
2) Call endpoint Create Consent By CONSENT_REQUEST_ID (SMS) with logged on user
Output:
{
"consent_id":"155f86b2-247f-4702-a7b2-671f2c3303b6",
"jwt":"eyJhbGciOiJIUzI1NiJ9.eyJlbnRpdGxlbWVudHMiOlt7InJvbGVfbmFtZSI6IkNhbkdldEN1c3RvbWVyIiwiYmFua19pZCI6ImdoLjI5LnVrLngifV0sImNyZWF0ZWRCeVVzZXJJZCI6ImFiNjUzOWE5LWIxMDUtNDQ4OS1hODgzLTBhZDhkNmM2MTY1NyIsInN1YiI6IjU3NGY4OGU5LTE5NDktNDQwNy05NTMwLTA0MzM3MTU5YzU2NiIsImF1ZCI6IjFhMTA0NjNiLTc4NTYtNDU4ZC1hZGI2LTViNTk1OGY1NmIxZiIsIm5iZiI6MTY2OTg5NDU5OSwiaXNzIjoiaHR0cDpcL1wvMTI3LjAuMC4xOjgwODAiLCJleHAiOjE2Njk4OTgxOTksImlhdCI6MTY2OTg5NDU5OSwianRpIjoiMTU1Zjg2YjItMjQ3Zi00NzAyLWE3YjItNjcxZjJjMzMwM2I2Iiwidmlld3MiOltdfQ.lLbn9BtgKvgAcb07if12SaEyPAKgXOEmr6x3Y5pU-vE",
"status":"INITIATED",
"consent_request_id":"bc0209bd-bdbe-4329-b953-d92d17d733f4"
}
3) We receive the SCA message via SMS
Your consent challenge : 29131491, Application: Any application
4) Call endpoint Answer Consent Challenge with logged on user
Url: https://apisandbox.openbankproject.com/obp/v5.0.0/banks/gh.29.uk.x/consents/155f86b2-247f-4702-a7b2-671f2c3303b6/challenge
Post body:
{
"answer": "29131491"
}
Output:
{
"consent_id":"155f86b2-247f-4702-a7b2-671f2c3303b6",
"jwt":"eyJhbGciOiJIUzI1NiJ9.eyJlbnRpdGxlbWVudHMiOlt7InJvbGVfbmFtZSI6IkNhbkdldEN1c3RvbWVyIiwiYmFua19pZCI6ImdoLjI5LnVrLngifV0sImNyZWF0ZWRCeVVzZXJJZCI6ImFiNjUzOWE5LWIxMDUtNDQ4OS1hODgzLTBhZDhkNmM2MTY1NyIsInN1YiI6IjU3NGY4OGU5LTE5NDktNDQwNy05NTMwLTA0MzM3MTU5YzU2NiIsImF1ZCI6IjFhMTA0NjNiLTc4NTYtNDU4ZC1hZGI2LTViNTk1OGY1NmIxZiIsIm5iZiI6MTY2OTg5NDU5OSwiaXNzIjoiaHR0cDpcL1wvMTI3LjAuMC4xOjgwODAiLCJleHAiOjE2Njk4OTgxOTksImlhdCI6MTY2OTg5NDU5OSwianRpIjoiMTU1Zjg2YjItMjQ3Zi00NzAyLWE3YjItNjcxZjJjMzMwM2I2Iiwidmlld3MiOltdfQ.lLbn9BtgKvgAcb07if12SaEyPAKgXOEmr6x3Y5pU-vE",
"status":"ACCEPTED"
}
5) Call endpoint Get Customer by CUSTOMER_ID with Consent Header
Request Header:
Consent-JWT:eyJhbGciOiJIUzI1NiJ9.eyJlbnRpdGxlbWVudHMiOlt7InJvbGVfbmFtZSI6IkNhbkdldEN1c3RvbWVyIiwiYmFua19pZCI6ImdoLjI5LnVrLngifV0sImNyZWF0ZWRCeVVzZXJJZCI6ImFiNjUzOWE5LWIxMDUtNDQ4OS1hODgzLTBhZDhkNmM2MTY1NyIsInN1YiI6IjU3NGY4OGU5LTE5NDktNDQwNy05NTMwLTA0MzM3MTU5YzU2NiIsImF1ZCI6IjFhMTA0NjNiLTc4NTYtNDU4ZC1hZGI2LTViNTk1OGY1NmIxZiIsIm5iZiI6MTY2OTg5NDU5OSwiaXNzIjoiaHR0cDpcL1wvMTI3LjAuMC4xOjgwODAiLCJleHAiOjE2Njk4OTgxOTksImlhdCI6MTY2OTg5NDU5OSwianRpIjoiMTU1Zjg2YjItMjQ3Zi00NzAyLWE3YjItNjcxZjJjMzMwM2I2Iiwidmlld3MiOltdfQ.lLbn9BtgKvgAcb07if12SaEyPAKgXOEmr6x3Y5pU-
Output:
{
"bank_id":"gh.29.uk.x",
"customer_id":"a9c8bea0-4f03-4762-8f27-4b463bb50a93",
"customer_number":"0908977830011-#2",
"legal_name":"NONE",
"mobile_phone_number":"+3816319549071",
"email":"marko@tesobe.com1",
"face_image":{
"url":"www.openbankproject",
"date":"2017-09-18T22:00:00Z"
},
"date_of_birth":"2017-09-18T22:00:00Z",
"relationship_status":"Single",
"dependants":5,
"dob_of_dependants":[],
"credit_rating":{
"rating":"3",
"source":"OBP"
},
"credit_limit":{
"currency":"EUR",
"amount":"10001"
},
"highest_education_attained":"Bachelor’s Degree",
"employment_status":"Employed",
"kyc_status":true,
"last_ok_date":"2017-09-18T22:00:00Z",
"title":null,
"branch_id":"3210",
"name_suffix":null,
"customer_attributes":[]
}
Consumer
The "consumer" of the API, i.e. the web, mobile or serverside "App" that calls on the OBP API on behalf of the end user (or system).
Each Consumer has a consumer key and secret which allows it to enter into secure communication with the API server.
A Consumer is given a Consumer ID (a UUID) which appears in logs and messages to the backend.
A Consumer may be pinned to an mTLS certificate i.e. the consumer record in the database is given a field which matches the PEM representation of the certificate.
After pinning, the consumer must present the certificate in all communication with the server.
There is a one to one relationship between a Consumer and its certificate. i.e. OBP does not (currently) store the history of certificates bound to a Consumer. If a certificate expires, the third party provider (TPP) must generate a new consumer using a new certificate. In this case, related resources such as rate limits and scopes must be copied from the old consumer to the new consumer. In the future, OBP may store multiple certificates for a consumer, but a certificate will always identify only one consumer record.
Consumer, Consent, Transport and Payload Security
Consumer, Consent, Transport and Payload Security with MTLS and JWS
This glossary item aims to give an overview of how the communication between an Application and the OBP API server is secured with Consents, Consumer records, MTLs and JWS.
It includes some implementation step notes for the Application developer.
The following components are required:
Consumer record
The Application must have an active API Consumer / Client record on the server.
MTLS
With Mutual TLS both the Consumer and the Server (OBP API) must use certificates.
JWS
The Request is signed by the Consumer with a JWS using the client certificate of the Consumer. Example: OBP-Hola private void requestIntercept
The Request is verified by the OBP API Server using the JWS provided by the Consumer. See OBP-API def verifySignedRequest
The Response is signed by the OBP API Server with a JWS. See OBP-API def signResponse
The Response is verified by the Client using the JWS provided by the OBP API Server. Example: OBP-Hola private void responseIntercept
Consent
The end user must give permission to the Application in order for the Application to see his/her account and transaction data.

In order to get an App / Consumer key
Sign up or login as a developer.
Register your App / Consumer HERE
Be sure to enter your Client Certificate in the registration form. To create the user.crt file see HERE
Authenticate
To test the service your App will need to authenticate using OAuth2.
You can use the OBP Hola App as an example / starting point for your App.
Consumer.consumer_key (Consumer Key)
The client identifier issued to the client during the registration process. It is a unique string representing the registration information provided by the client.
At the time the consumer_key was introduced OAuth 1.0a was only available. The OAuth 2.0 counterpart for this value is client_id
Consumption Device (CD)
The Consumption Device is the device that helps the user consume the service. In the CIBA use case, the user is not necessarily in control of the CD. For example, the CD may be in the control of an RP agent (e.g. at a bank teller) or might be a device controlled by the RP (e.g. a petrol pump)|
Counterparties
In OBP, there are two types of Counterparty:
-
Explicit Counterparties are created by calling an OBP endpoint - mainly for the purpose of creating a payment or variable recurring payments (VRPs) via Transaction Requests.
-
Implicit Counterparties (or "Other Accounts") are generated automatically from transactions - mainly for the purpose of tagging or adding other metadata.
Counterparties always bound to a "View" on an Account. In this way, different managers of an account can use different sets of beneficiaries.
Counterparties can be thought of the other side of of a transaction i.e. the other account or other party.
Common fields in a Counterparty are:
-
id : A UUID which references it.
-
name : the human readable name (e.g. Piano teacher)
-
description : the human readable name (e.g. Piano teacher)
-
currency : account currency (e.g. EUR, GBP, USD, ...)
-
other_bank_routing_scheme : eg: 'OBP', 'BIC', 'bankCode' etc
-
other_bank_routing_address : eg:
gh.29.uk- it must be a valid example of the scheme and may be validated for existance. -
other_account_routing_scheme : eg: 'OBP', 'IBAN', 'AccountNumber' etc.
-
other_account_routing_address : eg:
1d65db7c-a7b2-4839-af41-95- a valid example of the scheme which may be validated for existance.
The above fields describe how the backend can route payments to the counterparty.
Alternative routings might be useful as well:
-
other_account_secondary_routing_scheme : An alternative routing scheme
-
other_account_secondary_routing_address : If it is an IBAN value, it should be unique for each counterparty.
-
other_branch_routing_scheme : eg: OBP or other branch scheme
-
other_branch_routing_address : eg: `branch-id-123. Unlikely to be used in sandbox mode.
In order to send payments to a counterparty:
- is_beneficiary : must be set to
true
If the backend wants to transmit other information we can use:
- bespoke: A list of key-value pairs can be added to the counterparty.
Note: In order to add a Counterparty to a View, the view must have the canAddCounterparty permission
Counterparties may have Limits have setup for them which constrain payments made to them through Variable Recurring Payments (VRP).
Counterparty-Limits
Counterparty Limits can be used to restrict payment (Transaction Request) amounts and frequencies (per month, year, total) that can be made to a Counterparty (Beneficiary).
Counterparty Limits can be used to limit both single or repeated payments (VRPs) to a Counterparty Beneficiary.
Counterparty Limits reference a counterparty_id (a UUID) rather an an IBAN or Account Number.
This means it is possible to have multiple Counterparties that refer to the same external bank account.
In other words, a Counterparty Limit restricts an OBP Counterparty rather than a certain IBAN or other Bank Account Number.
Since Counterparties are bound to OBP Views it is possible to create similar Counterparties used by different Views. This is by design i.e. a Two Users called Accountant1 could Accountant2 could create their own Views and Counterparties referencing the same corporation but still have their own limits say for different cost centers.
To manually create and use a Counterparty Limit via a Consent for Variable Recurring Payments (VRP) you would:
1) Create a Custom View named e.g. VRP1.
2) Place a Beneficiary Counterparty on that view.
3) Add Counterparty Limits for that Counterparty.
4) Generate a Consent containing the bank, account and view (e.g. VRP1)
5) Let the App use the consent to trigger Transaction Requests.
However, you can use the following endpoint to automate the above steps.
Counterparty.counterpartyId
Example value: 9fg8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: The Counterparty ID used in URLs. This SHOULD NOT be a name of a Counterparty.
Counterparty.counterpartyName
Example value: John Smith Ltd.
Description: The name of a Counterparty. Ideally unique for an Account
Counterparty.isBeneficiary
Example value: false
Description: This is a boolean. True if the originAccount can send money to the Counterparty
Cross-Device Authorization
Cross-device authorization flows enable a user to initiate an authorization flow on one device
(the Consumption Device) and then use a second, personally trusted, device (Authorization Device) to
authorize the Consumption Device to access a resource (e.g., access to a service).
Two examples of popular cross-device authorization flows are:
- The Device Authorization Grant RFC8628
- Client-Initiated Backchannel Authentication CIBA
Customer
The legal entity that has the relationship to the bank. Customers are linked to Users via User Customer Links. Customer attributes include Date of Birth, Customer Number etc.
Customer.attributeId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: Customer attribute id
Customer.attributeId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: User attribute id
Customer.consumerId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A non human friendly string that identifies the consumer. It is the app which calls the apis
Customer.customerAccountLinkId
Example value: xyz8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A non human friendly string that identifies the Customer Account Link and is used in URLs.
Customer.customerAttributeId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A non human friendly string that identifies the customer attribute and is used in URLs.
Customer.customerAttributeName
Example value: SPECIAL_TAX_NUMBER
Description: The Customer Attribute name, eg: SPECIAL_TAX_NUMBER
Customer.customerAttributeType
Example value: STRING
Description: It can be STRING, INTEGER, DOUBLE, DATE_WITH_DAY
Customer.customerAttributeValue
Example value: 123456789
Description: The Customer Attribute value of the current attribute type, eg: 123456789.
Customer.customerId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A non human friendly string that identifies the customer and is used in URLs. This SHOULD NOT be the customer number. The combination of customerId and bankId MUST be unique on an OBP instance. customerId SHOULD be unique on an OBP instance. Ideally customerId is a UUID. A mapping between customer number and customer id is kept in OBP.
Customer.customerNumber
Example value: 5987953
Description: The human friendly customer identifier that MUST uniquely identify the Customer at the Bank ID. Customer Number is NOT used in URLs.
Customer.customer_id
The identifier that MUST NOT leak the customer number or other identifier normally used by the customer or bank staff. It SHOULD be a UUID and MUST be unique in combination with BANK_ID.
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Customer.key
Example value: bwf0ykmwoirip1yjxcn15wnhuyxcziwgtcoaildq
Description: This key should be used with Adapter.value together. They are a pair.
Customer.kycStatus
Example value: false
Description: This is boolean to indicate if the cusomter's KYC has been checked.
Customer.mobileNumber
Example value: +44 07972 444 876
Description: The mobile number name of the Customer.
Customer.secret
Example value: xwdgylv3vau0n2gkxu1aize4glapftfldp5y1bic
Description: This key should be used with Adapter.value together. They are a pair.
DAuth
DAuth Introduction, Setup and Usage
DAuth is an experimental authentication mechanism that aims to pin an ethereum or other blockchain Smart Contract to an OBP "User".
In the future, it might be possible to be more specific and pin specific actors (wallets) that are acting within the smart contract, but so far, one smart contract acts on behalf of one User.
Thus, if a smart contract "X" calls the OBP API using the DAuth header, OBP will get or create a user called X and the call will proceed in the context of that User "X".
DAuth is invoked by the REST client (caller) including a specific header (see step 3 below) in any OBP REST call.
When OBP receives the DAuth token, it creates or gets a User with a username based on the smart_contract_address and the provider based on the network_name. The combination of username and provider is unique in OBP.
If you are calling OBP-API via an API3 Airnode, the Airnode will take care of constructing the required header.
When OBP detects a DAuth header / token it first checks if the Consumer is allowed to make such a call. OBP will validate the Consumer ip address and signature etc.
Note: The DAuth flow does not require an explicit POST like Direct Login to create the token.
Permissions may be assigned to an OBP User at any time, via the UserAuthContext, Views, Entitlements to Roles or Consents.
Note: DAuth is NOT enabled on this instance!
Note: The DAuth client is responsible for creating a token which will be trusted by OBP absolutely!
To use DAuth:
1) Configure OBP API to accept DAuth.
Set up properties in your props file
# -- DAuth --------------------------------------
# Define secret used to validate JWT token
# jwt.public_key_rsa=path-to-the-pem-file
# Enable/Disable DAuth communication at all
# In case isn't defined default value is false
# allow_dauth=false
# Define comma separated list of allowed IP addresses
# dauth.host=127.0.0.1
# -------------------------------------- DAuth--
Please keep in mind that property jwt.public_key_rsa is used to validate JWT token to check it is not changed or corrupted during transport.
2) Create / have access to a JWT
The following videos are available:
* DAuth in local environment
HEADER:ALGORITHM & TOKEN TYPE
{
"alg": "RS256",
"typ": "JWT"
}
PAYLOAD:DATA
{
"smart_contract_address": "0xe123425E7734CE288F8367e1Bb143E90bb3F051224",
"network_name": "AIRNODE.TESTNET.ETHEREUM",
"msg_sender": "0xe12340927f1725E7734CE288F8367e1Bb143E90fhku767",
"consumer_key": "0x1234a4ec31e89cea54d1f125db7536e874ab4a96b4d4f6438668b6bb10a6adb",
"timestamp": "2021-11-04T14:13:40Z",
"request_id": "0Xe876987694328763492876348928736497869273649"
}
VERIFY SIGNATURE
RSASHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
) your-RSA-key-pair
Here is an example token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzbWFydF9jb250cmFjdF9hZGRyZXNzIjoiMHhlMTIzNDI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGJiM0YwNTEyMjQiLCJuZXR3b3JrX25hbWUiOiJFVEhFUkVVTSIsIm1zZ19zZW5kZXIiOiIweGUxMjM0MDkyN2YxNzI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGZoa3U3NjciLCJjb25zdW1lcl9rZXkiOiIweDEyMzRhNGVjMzFlODljZWE1NGQxZjEyNWRiNzUzNmU4NzRhYjRhOTZiNGQ0ZjY0Mzg2NjhiNmJiMTBhNmFkYiIsInRpbWVzdGFtcCI6IjIwMjEtMTEtMDRUMTQ6MTM6NDBaIiwicmVxdWVzdF9pZCI6IjBYZTg3Njk4NzY5NDMyODc2MzQ5Mjg3NjM0ODkyODczNjQ5Nzg2OTI3MzY0OSJ9.XSiQxjEVyCouf7zT8MubEKsbOBZuReGVhnt9uck6z6k
3) Try a REST call using the header
Using your favorite http client:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/users/current
Body
Leave Empty!
Headers:
DAuth: your-jwt-from-step-above
Here is it all together:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/users/current HTTP/1.1
Host: localhost:8080
User-Agent: curl/7.47.0
Accept: /
DAuth: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzbWFydF9jb250cmFjdF9hZGRyZXNzIjoiMHhlMTIzNDI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGJiM0YwNTEyMjQiLCJuZXR3b3JrX25hbWUiOiJFVEhFUkVVTSIsIm1zZ19zZW5kZXIiOiIweGUxMjM0MDkyN2YxNzI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGZoa3U3NjciLCJjb25zdW1lcl9rZXkiOiIweDEyMzRhNGVjMzFlODljZWE1NGQxZjEyNWRiNzUzNmU4NzRhYjRhOTZiNGQ0ZjY0Mzg2NjhiNmJiMTBhNmFkYiIsInRpbWVzdGFtcCI6IjIwMjEtMTEtMDRUMTQ6MTM6NDBaIiwicmVxdWVzdF9pZCI6IjBYZTg3Njk4NzY5NDMyODc2MzQ5Mjg3NjM0ODkyODczNjQ5Nzg2OTI3MzY0OSJ9.XSiQxjEVyCouf7zT8MubEKsbOBZuReGVhnt9uck6z6k
CURL example
curl -v -H 'DAuth: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzbWFydF9jb250cmFjdF9hZGRyZXNzIjoiMHhlMTIzNDI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGJiM0YwNTEyMjQiLCJuZXR3b3JrX25hbWUiOiJFVEhFUkVVTSIsIm1zZ19zZW5kZXIiOiIweGUxMjM0MDkyN2YxNzI1RTc3MzRDRTI4OEY4MzY3ZTFCYjE0M0U5MGZoa3U3NjciLCJjb25zdW1lcl9rZXkiOiIweDEyMzRhNGVjMzFlODljZWE1NGQxZjEyNWRiNzUzNmU4NzRhYjRhOTZiNGQ0ZjY0Mzg2NjhiNmJiMTBhNmFkYiIsInRpbWVzdGFtcCI6IjIwMjEtMTEtMDRUMTQ6MTM6NDBaIiwicmVxdWVzdF9pZCI6IjBYZTg3Njk4NzY5NDMyODc2MzQ5Mjg3NjM0ODkyODczNjQ5Nzg2OTI3MzY0OSJ9.XSiQxjEVyCouf7zT8MubEKsbOBZuReGVhnt9uck6z6k' https://apisandbox.openbankproject.com/obp/v3.0.0/users/current
You should receive a response like:
{
"user_id": "4c4d3175-1e5c-4cfd-9b08-dcdc209d8221",
"email": "",
"provider_id": "0xe123425E7734CE288F8367e1Bb143E90bb3F051224",
"provider": "ETHEREUM",
"username": "0xe123425E7734CE288F8367e1Bb143E90bb3F051224",
"entitlements": {
"list": []
}
}
Under the hood
The file, dauth.scala handles the DAuth,
We:
-> Check if Props allow_dauth is true
-> Check if DAuth header exists
-> Check if getRemoteIpAddress is OK
-> Look for "token"
-> parse the JWT token and getOrCreate the user
-> get the data of the user
More information
Parameter names and values are case sensitive.
Each parameter MUST NOT appear more than once per request.
Data Model Overview
An overview of the Open Bank Project Data Model.
This diagram may help in understanding the Open Bank Project entities, capabilities and concepts. However, it is subject to change. If we change the data model, we release migration scripts.
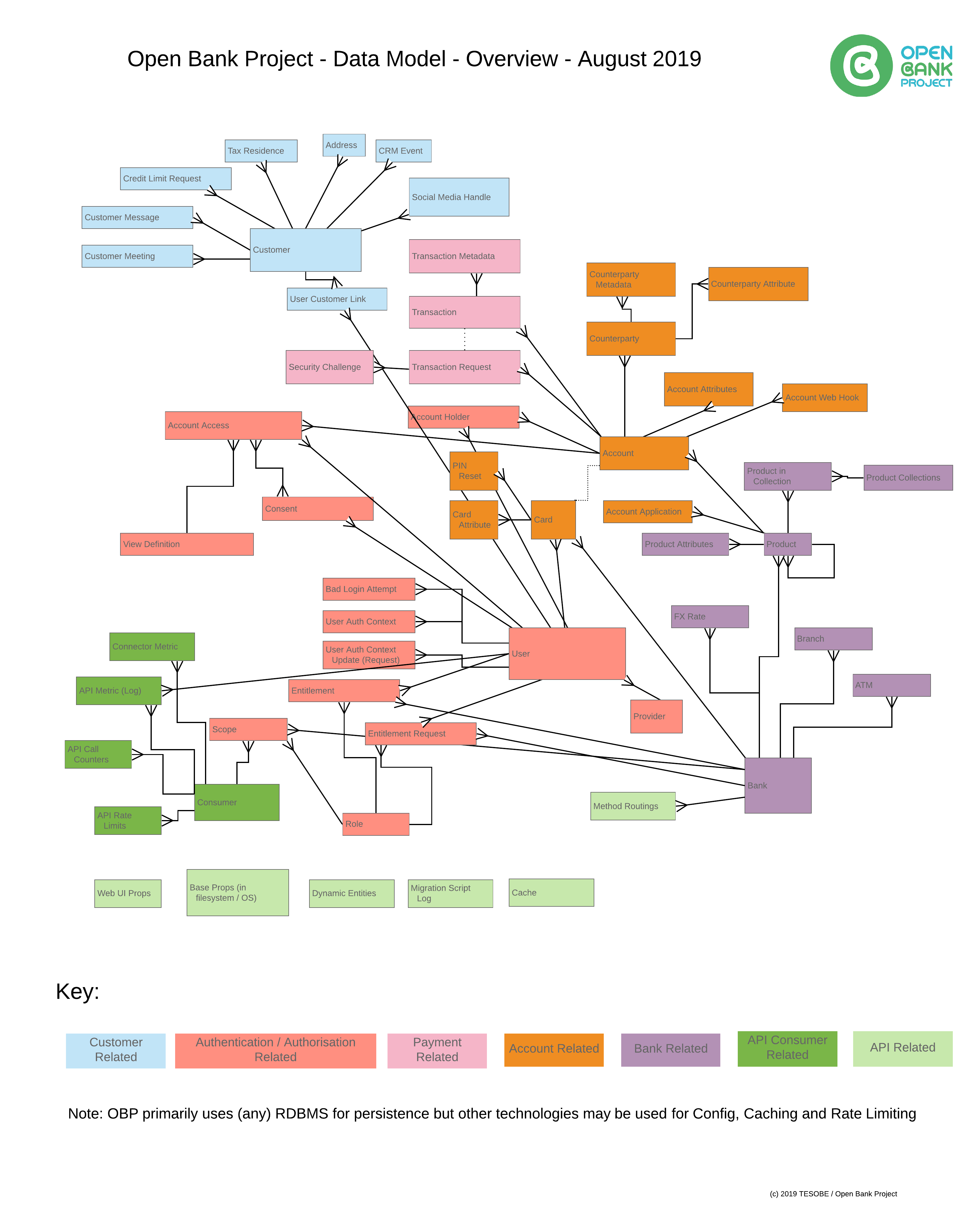
Direct Login
Direct Login is a simple authentication process to be used at hackathons and trusted environments:
1) Get your App key
Sign up or login as a developer.
Register your App key HERE
Copy and paste the consumer key for step two below.
2) Authenticate
Using your favorite http client:
POST https://apisandbox.openbankproject.com/my/logins/direct
Body
Leave Empty!
Headers:
Content-Type: application/json
directlogin: username=janeburel,
password=the-password-of-jane,
consumer_key=your-consumer-key-from-step-one
Here is it all together:
POST https://apisandbox.openbankproject.com/my/logins/direct HTTP/1.1
directlogin: username=janeburel, password=686876, consumer_key=GET-YOUR-OWN-API-KEY-FROM-THE-OBP
Content-Type: application/json
Host: 127.0.0.1:8080
Connection: close
User-Agent: Paw/2.3.3 (Macintosh; OS X/10.11.3) GCDHTTPRequest
Content-Length: 0
Note: HTTP/2.0 requires that header names are lower case. Currently the header name for directlogin is case insensitive.
To troubleshoot request headers, you may want to ask your administrator to Echo Request headers.
You should receive a token:
{"token":"a-long-token-string"}
3) Make authenticated API calls
In subsequent calls you can use the token received in step 2
e.g.
Action:
PUT https://apisandbox.openbankproject.com/obp/v2.0.0/banks/obp-bankx-n/accounts/my-new-account-id
Body:
{ "type":"CURRENT", "balance":{ "currency":"USD", "amount":"0" }}
Headers:
Content-Type: application/json
directlogin: token=your-token-from-step-2
Here is another example:
PUT https://apisandbox.openbankproject.com/obp/v2.0.0/banks/enbd-egy--p3/accounts/newaccount1 HTTP/1.1
directlogin: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyIiOiIifQ.C8hJZNPDI59OOu78pYs4BWp0YY_21C6r4A9VbgfZLMA
Content-Type: application/json
Cookie: JSESSIONID=7h1ssu6d7j151u08p37a6tsx1
Host: 127.0.0.1:8080
Connection: close
User-Agent: Paw/2.3.3 (Macintosh; OS X/10.11.3) GCDHTTPRequest
Content-Length: 60
{"type":"CURRENT","balance":{"currency":"USD","amount":"0"}}
More information
Parameter names and values are case sensitive.
The following parameters must be sent by the client to the server:
username
The name of the user to authenticate.
password
The password used to authenticate user. Alphanumeric string.
consumer_key
The application identifier. Generated on OBP side via
https://apiexplorer-ii-sandbox.openbankproject.com//consumers/register endpoint.
Each parameter MUST NOT appear more than once per request.
Dummy Customer Logins
The following dummy Customer Logins may be used by developers testing their applications on this sandbox:
Customer Logins:
{"email":"robert.uk.29@example.com","password":"d9c663","user_name":"robert.uk.29@example.com"},
{"email":"susan.uk.29@example.com","password":"2b78e8","user_name":"susan.uk.29@example.com"},
{"email":"anil.uk.29@example.com","password":"588848","user_name":"anil.uk.29@example.com"},
{"email":"ellie.uk.29@example.com","password":"a81594","user_name":"ellie.uk.29@example.com"},
{"email":"robin.fr.29@example.com","password":"c42142","user_name":"robin.fr.29@example.com"},
{"email":"suzanne.fr.29@example.com","password":"a4f9af","user_name":"suzanne.fr.29@example.com"},
{"email":"nathan.fr.29@example.com","password":"bde179","user_name":"nathan.fr.29@example.com"},
{"email":"elise.fr.29@example.com","password":"79a0cb","user_name":"elise.fr.29@example.com"},
{"email":"roberto.it.29@example.com","password":"6a463a","user_name":"roberto.it.29@example.com"},
{"email":"susanna.it.29@example.com","password":"57a19b","user_name":"susanna.it.29@example.com"},
{"email":"alfio.it.29@example.com","password":"69e8d6","user_name":"alfio.it.29@example.com"},
{"email":"elisa.it.29@example.com","password":"14adc9","user_name":"elisa.it.29@example.com"},
{"email":"rob.us.29@example.com","password":"a50eda","user_name":"rob.us.29@example.com"},
{"email":"sue.us.29@example.com","password":"e1788f","user_name":"sue.us.29@example.com"},
{"email":"alf.us.29@example.com","password":"9122a1","user_name":"alf.us.29@example.com"},
{"email":"emily.us.29@example.com","password":"4984b4","user_name":"emily.us.29@example.com"},
{"email":"roby.tr.29@example.com","password":"7deb47","user_name":"roby.tr.29@example.com"},
{"email":"suzan.tr.29@example.com","password":"5f68f1","user_name":"suzan.tr.29@example.com"},
{"email":"asil.tr.29@example.com","password":"af2d2b","user_name":"asil.tr.29@example.com"},
{"email":"ela.tr.29@example.com","password":"09cf2b","user_name":"ela.tr.29@example.com"},
{"email":"robert.be.29@example.com","password":"00f680","user_name":"robert.be.29@example.com"},
{"email":"susan.be.29@example.com","password":"f46941","user_name":"susan.be.29@example.com"},
{"email":"anil.be.29@example.com","password":"9404f4","user_name":"anil.be.29@example.com"},
{"email":"ellie.be.29@example.com","password":"58e2a9","user_name":"ellie.be.29@example.com"},
{"email":"robert.de.29@example.com","password":"ab4a83","user_name":"robert.de.29@example.com"},
{"email":"susan.de.29@example.com","password":"432da0","user_name":"susan.de.29@example.com"},
{"email":"anil.de.29@example.com","password":"adfa28","user_name":"anil.de.29@example.com"},
{"email":"ellie.de.29@example.com","password":"2efb1f","user_name":"ellie.de.29@example.com"},
{"email":"jaakko.fi.29@example.com","password":"8132cf","user_name":"jaakko.fi.29@example.com"},
{"email":"helmi.fi.29@example.com","password":"9f5cc8","user_name":"helmi.fi.29@example.com"},
{"email":"timo.fi.29@example.com","password":"6addcd","user_name":"timo.fi.29@example.com"},
{"email":"katja.fi.29@example.com","password":"ca0317","user_name":"katja.fi.29@example.com"}
https://apisandbox-portal.openbankproject.com/#customer-logins
Dynamic Endpoint Manage
If you want to create endpoints from Swagger / Open API specification files, use Dynamic Endpoints.
We use the term "Dynamic" because these Endpoints persist in the OBP database and are served from real time generated Scala code.
This contrasts to the "Static" endpoints (see the Static glossary item) which are served from static Scala code.
Dynamic endpoints can be changed in real-time and do not require an OBP instance restart.
When you POST a swagger file, all the endpoints defined in the swagger file, will be created in this OBP instance.
You can create a set of endpoints in three different modes:
1) If the host field in the Swagger file is set to "dynamic_entity", then you should link the swagger JSON fields to Dynamic Entity fields. To do this use the Endpoint Mapping endpoints.
2) If the host field in the Swagger file is set to "obp_mock", the Dynamic Endpoints created will return example responses defined in the swagger file.
3) If you need to link the responses to external resource, use the Method Routing endpoints.
Dynamic Endpoints can be created at the System level (bank_id is null) or Bank / Space level (bank_id is NOT null).
You might want to create Bank level Dynamic Entities in order to grant automated roles based on user email domain. See the OBP-API sample.props.template
Upon the successful creation of each Dynamic Endpoint, OBP will automatically:
*Create a Guard with a named Role on the Endpoint to protect it from unauthorised users.
*Grant you an Entitlement to the required Role so you can call the endpoint and pass its Guard.
The following videos are available:
Dynamic Message Doc
In OBP we represent messages sent by a Connector method / function as MessageDocs.
A MessageDoc defines the message the Connector sends to an Adapter and the response it expects from the Adapter.
Using this endpoint, developers can create their own scala methods aka Connectors in OBP code.
These endpoints are designed for extending the current connector methods.
When you call the Dynamic Resource Doc endpoints, sometimes you need to call internal Scala methods which
don't yet exist in the OBP code. In this case you can use these endpoints to create your own internal Scala methods.
You can also use these endpoints to create your own helper methods in OBP code.
This feature is somewhat work in progress (WIP).
The following videos are available:
* Introduction to Dynamic Message Doc
Dynamic Resource Doc
In OBP we largely define our endpoints using an internal case class or model called ResourceDoc
Using this endpoint, developers can create their own Resource Docs at run time thus creating fully featured
Open Bank Project style endpoints dynamically.
In order to do this you need to prepare your desired Resource Doc as JSON.
The business logic code can be written in the method_body field as encoded Scala code.
This feature is somewhat work in progress (WIP).
The following videos are available:
* Introduction to Dynamic Resource Docs
Dynamic-Entities
Dynamic Entities allow you to create custom data structures and their corresponding CRUD endpoints at runtime without writing code or restarting the OBP-API instance.
Overview:
Dynamic Entities enable you to define custom business objects (entities) with their fields, types, and validation rules via API calls. Once created, OBP automatically generates fully functional REST API endpoints for Create, Read, Update, and Delete operations.
Types of Dynamic Entities:
- System Level Dynamic Entities - Available across the entire OBP instance
- Bank Level Dynamic Entities - Scoped to a specific bank
Creating a Dynamic Entity:
POST /management/system-dynamic-entities
{
"hasPersonalEntity": true,
"CustomerPreferences": {
"description": "Customer preferences and settings",
"required": ["theme"],
"properties": {
"theme": {
"type": "string",
"example": "dark"
},
"language": {
"type": "string",
"example": "en"
},
"notifications_enabled": {
"type": "boolean",
"example": "true"
}
}
}
}
IMPORTANT - JSON Structure:
The entity name (e.g., "CustomerPreferences") MUST be a direct top-level key in the JSON. The root object can contain at most TWO fields: your entity name and optionally "hasPersonalEntity".
Common mistake - DO NOT do this:
{
"entity": {
"CustomerPreferences": { ... }
}
}
This will fail with error: "There must be 'required' field in entity"
Supported field types:
STRING, INTEGER, DOUBLE, BOOLEAN, DATE_WITH_DAY (format: yyyy-MM-dd), JSON (objects and arrays), and reference types (foreign keys)
The hasPersonalEntity flag:
When hasPersonalEntity = true (default):
OBP generates TWO sets of endpoints:
- Regular endpoints - Access all entities (requires specific roles)
- POST /CustomerPreferences
- GET /CustomerPreferences
- GET /CustomerPreferences/ID
- PUT /CustomerPreferences/ID
- DELETE /CustomerPreferences/ID
- Personal 'my' endpoints - User-scoped access (see here)
- POST /my/CustomerPreferences
- GET /my/CustomerPreferences
- GET /my/CustomerPreferences/ID
- PUT /my/CustomerPreferences/ID
- DELETE /my/CustomerPreferences/ID
When hasPersonalEntity = false:
OBP generates ONLY the regular endpoints. No 'my' endpoints are created. Use this when the entity represents shared data that should not be user-scoped.
For bank-level entities, endpoints include the bank ID:
- POST /banks/BANK_ID/CustomerPreferences
- POST /banks/BANK_ID/my/CustomerPreferences (if hasPersonalEntity = true)
Auto-generated roles:
When you create a Dynamic Entity named 'FooBar', OBP automatically creates these roles:
- CanCreateDynamicEntity_FooBar
- CanUpdateDynamicEntity_FooBar
- CanGetDynamicEntity_FooBar
- CanDeleteDynamicEntity_FooBar
Management endpoints:
- POST /management/system-dynamic-entities - Create system level entity
- POST /management/banks/BANK_ID/dynamic-entities - Create bank level entity
- GET /management/system-dynamic-entities - List all system level entities
- GET /management/banks/BANK_ID/dynamic-entities - List bank level entities
- PUT /management/system-dynamic-entities/DYNAMIC_ENTITY_ID - Update entity definition
- DELETE /management/system-dynamic-entities/DYNAMIC_ENTITY_ID - Delete entity (and all its data)
Required roles to manage Dynamic Entities:
- CanCreateSystemLevelDynamicEntity
- CanCreateBankLevelDynamicEntity
Use cases:
- Customer preferences and settings
- Custom metadata for accounts or transactions
- Business-specific data structures
- Rapid prototyping of new features
- Extension of core banking data model
For user-scoped Dynamic Entities, see here
For more detailed information about managing Dynamic Entities, see here
Dynamic-Entity-Intro
Dynamic Entities can be used to store and retrieve custom data objects (think your own tables and fields) in the OBP instance.
You can define your own Dynamic Entities or use Dynamic Entities created by others.
You would use Dynamic Entities if you want to go beyond the OBP standard data model and store custom data structures. Note, if you want to extend the core OBP banking model of Customers, Products, Accounts, Transactions and so on you can also add Custom Attributes to these standard objects.
You would use Dynamic Endpoints if you want to go beyond the standard OBP or other open banking standard APIs.
Dynamic Entities have their own REST APIs so you can easily Create, Read, Update and Delete records. However, you can also connect Dynamic Endpoints with your own API definitions (via Swagger) and so create custom GET endpoints connecting to any combination of Dynamic Entities.
Dynamic Endpoints can retrieve the data of Dynamic Entities so you can effectively create bespoke endpoint / data combinations - at least for GET endpoints - using Dynamic Endpoints, Entities and Endpoint Mapping.
In order to use Dynamic Entities you will need to have the appropriate Entitlements to Create, Read, Update or Delete records in the Dynamic Entity.
You define your Dynamic Entities in JSON.
Fields are typed, have an example value and a (markdown) description. They can also be constrained in size.
You can also create field "references" to other fields in other Entities. These are like foreign keys to other Dynamic or Static (built in) entities.
In other words, if you create an Entity called X which has a field called A, you can force the values of X.A to match the values of Y.B where Y is another Dynamic Entity or Z.B where Z is a Static (OBP) Entity.
If you want to add data to an existing Entity, you can create a Dynamic Entity which has a reference field to the existing entity.
Dynamic Entities can be created at the System level (bank_id is null) - or Bank / Space level (bank_id is not null). You might want to create Bank level Dynamic Entities in order to grant automated roles based on user email domain.
When creating a Dynamic Entity, OBP automatically:
- Creates a data structure in the OBP database in which to store the records of the new Entity.
- Creates a primary key for the Entity which can be used to update and delete the Entity.
- Creates Create, Read, Update and Delete endpoints to operate on the Entity so you can insert, get, modify and delete records. These CRUD operations are all available over the generated REST endpoints.
- Creates Roles to guard the above endpoints.
Following the creation of a Dynamic Entity you will need to grant yourself or others the appropriate roles before you can insert or get records.
The generated Roles required for CRUD operations on a Dynamic Entity are like any other OBP Role i.e. they can be requested, granted, revoked and auto-granted using the API Explorer / API Manager or via REST API. To see the Roles required for a Dynamic Entities endpoints, see the API Explorer for each endpoint concerned.
Each Dynamic Entity gets a dynamicEntityId which uniquely identifies it and also the userId which identifies the user who created the Entity. The dynamicEntityId is used to update the definition of the Entity.
To visualise any data contained in Dynamic Entities you could use external BI tools and use the GET endpoints and authenticate using OAuth or Direct Login.
The following videos are available:
DynamicConnectorMethod.lang
Example value: Scala
Description: the programming language of OBP connector method body.
DynamicConnectorMethod.methodBody.Java
Example value: package%20code.bankconnectors%3B%0A%0Aimport%20com.openbankproject.commons.model.%3B%0Aimport%20java.util.function.Function%3B%0Aimport%20java.util.function.Supplier%3B%0A%0A%2F**%0A%20%20This%20is%20a%20java%20dynamic%20function%20template.%0A%20*%20Must%20copy%20the%20whole%20content%20of%20the%20file%20as%20%22dynamic%20method%20body%22.%0A%20*%20Currently%2C%20support%20Java%201.8%20version%20language%20features%0A%20*%2F%0Apublic%20class%20DynamicJavaConnector%20implements%20Supplier%3CFunction%3CObject%5B%5D%2C%20Object%3E%3E%20%7B%0A%20%20%20%20private%20Object%20apply(Object%5B%5D%20args)%20%7B%0A%20%20%20%20%20%20%20BankId%20bankId%20%3D%20(BankId)%20args%5B0%5D%3B%0A%0A%20%20%20%20%20%20%20Bank%20bank%20%3D%20new%20BankCommons(bankId%2C%20%22The%20Java%20Bank%20of%20Scotland%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22The%20Royal%20Bank%20of%20Scotland%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22http%3A%2F%2Fwww.red-bank-shoreditch.com%2Flogo.gif%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22http%3A%2F%2Fwww.red-bank-shoreditch.com%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22OBP%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22Java%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22Swift%20bic%20value%22%2C%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%22Java%22%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20)%3B%0A%20%20%20%20%20%20%20return%20bank%3B%0A%20%20%20%20%7D%0A%0A%20%20%20%20%40Override%0A%20%20%20%20public%20Function%3CObject%5B%5D%2C%20Object%3E%20get()%20%7B%0A%20%20%20%20%20%20%20%20return%20this%3A%3Aapply%3B%0A%20%20%20%20%7D%0A%7D%0A
Description: the URL-encoded format String, the original Java code is the OBP connector method body.
DynamicConnectorMethod.methodBody.Js
Example value: %7B%0A%20%20%20%20const%20%5BbankId%5D%20%3D%20args%3B%0A%20%20%20%20%2F%2F%20call%20java%20or%20scala%20type%20in%20this%20way%0A%20%20%20%20const%20BigDecimal%20%3D%20Java.type(%27java.math.BigDecimal%27)%3B%0A%20%20%20%20%2F%2F%20define%20a%20class%0A%20%20%20%20class%20SwiftBic%7B%0A%20%20%20%20%20%20%20%20constructor(name%2C%20value)%20%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20this.name%20%3D%20name%3B%0A%20%20%20%20%20%20%20%20%20%20%20%20this.value%20%3D%20value%3B%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%7D%0A%20%20%20%20%2F%2F%20define%20async%20function%0A%20%20%20%20const%20someAsyncFn%20%3D%20async%20()%20%3D%3E%20new%20BigDecimal(%27123.456%27)%0A%20%20%20%20%2F%2F%20call%20other%20async%20methods%0A%20%20%20%20const%20data%20%3D%20await%20someAsyncFn()%3B%0A%0A%20%20%20%20const%20bank%20%3D%20%7B%0A%20%20%20%20%20%20%20%20%22bankId%22%3A%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20%22value%22%3A%22HelloJsBank%3A%22%2B%20bankId%0A%20%20%20%20%20%20%20%20%7D%2C%0A%20%20%20%20%20%20%20%20%22shortName%22%3A%22The%20Js%20Bank%20of%20Scotland%22%20%2Bdata.toString()%2C%0A%20%20%20%20%20%20%20%20%22fullName%22%3A%22The%20Js%20Bank%20of%20Scotland%22%2C%0A%20%20%20%20%20%20%20%20%22logoUrl%22%3A%22http%3A%2F%2Fwww.red-bank-shoreditch.com%2Flogo.gif%22%2C%0A%20%20%20%20%20%20%20%20%22websiteUrl%22%3A%22http%3A%2F%2Fwww.red-bank-shoreditch.com%22%2C%0A%20%20%20%20%20%20%20%20%22bankRoutingScheme%22%3A%22OBP%22%2C%0A%20%20%20%20%20%20%20%20%22bankRoutingAddress%22%3A%22Js%22%2C%0A%20%20%20%20%20%20%20%20%22swiftBic%22%3A%20new%20SwiftBic(%22Mock%20Swift%22%2C%2010).name%2C%0A%20%20%20%20%20%20%20%20%22nationalIdentifier%22%3A%22Js%22%2C%0A%20%20%20%20%7D%0A%0A%20%20%20%20return%20bank%3B%0A%7D
Description: the URL-encoded format String, the original Js code is the OBP connector method body.
DynamicConnectorMethod.methodBody.scala
Example value: %20%20%20%20%20%20Future.successful%28%0A%20%20%20%20%20%20%20%20Full%28%28BankCommons%28%0A%20%20%20%20%20%20%20%20%20%20BankId%28%22Hello%20bank%20id%22%29%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%228%22%0A%20%20%20%20%20%20%20%20%29%2C%20None%29%29%0A%20%20%20%20%20%20%29
Description: the URL-encoded format String, the original code is the OBP connector method body.
DynamicResourceDoc.description
Example value: Create one User
Description: the description for this endpoint
DynamicResourceDoc.dynamicResourceDocId
Example value: vce035ca-9a0f-4bfa-b30b-9003aa467f51
Description: A string that MUST uniquely identify the dynamic Resource Doc on this OBP instance, can be used in all cache.
DynamicResourceDoc.errorResponseBodies
Example value: OBP-50000: Unknown Error.,OBP-20001: User not logged in. Authentication is required!,OBP-20006: User is missing one or more roles: ,OBP-10001: Incorrect json format.
Description: The possible error messages of the endpoint.
DynamicResourceDoc.exampleRequestBody
Example value: {"name": "Jhon", "age": 12, "hobby": ["coding"],"optional_fields": ["hobby"]}
Description: the json string of the request body.
DynamicResourceDoc.methodBody
Example value: %20%20%20%20val%20Some(resourceDoc)%20%3D%20callContext.resourceDocument%0A%20%20%20%20val%20hasRequestBody%20%3D%20request.body.isDefined%0A%0A%20%20%20%20%2F%2F%20get%20Path%20Parameters%2C%20example%3A%0A%20%20%20%20%2F%2F%20if%20the%20requestUrl%20of%20resourceDoc%20is%20%2Fhello%2Fbanks%2FBANK_ID%2Fworld%0A%20%20%20%20%2F%2F%20the%20request%20path%20is%20%2Fhello%2Fbanks%2Fbank_x%2Fworld%0A%20%20%20%20%2F%2FpathParams.get(%22BANK_ID%22)%20will%20get%20Option(%22bank_x%22)%20value%0A%0A%20%20%20%20val%20myUserId%20%3D%20pathParams(%22MY_USER_ID%22)%0A%0A%0A%20%20%20%20val%20requestEntity%20%3D%20request.json%20match%20%7B%0A%20%20%20%20%20%20case%20Full(zson)%20%3D%3E%0A%20%20%20%20%20%20%20%20try%20%7B%0A%20%20%20%20%20%20%20%20%20%20zson.extract%5BRequestRootJsonClass%5D%0A%20%20%20%20%20%20%20%20%7D%20catch%20%7B%0A%20%20%20%20%20%20%20%20%20%20case%20e%3A%20MappingException%20%3D%3E%0A%20%20%20%20%20%20%20%20%20%20%20%20return%20Full(errorJsonResponse(s%22%24InvalidJsonFormat%20%24%7Be.msg%7D%22))%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%20%20case%20_%3A%20EmptyBox%20%3D%3E%0A%20%20%20%20%20%20%20%20return%20Full(errorJsonResponse(s%22%24InvalidRequestPayload%20Current%20request%20has%20no%20payload%22))%0A%20%20%20%20%7D%0A%0A%0A%20%20%20%20%2F%2F%20please%20add%20business%20logic%20here%0A%20%20%20%20val%20responseBody%3AResponseRootJsonClass%20%3D%20ResponseRootJsonClass(s%22%24%7BmyUserId%7D_from_path%22%2C%20requestEntity.name%2C%20requestEntity.age%2C%20requestEntity.hobby)%0A%20%20%20%20Future.successful%20%7B%0A%20%20%20%20%20%20(responseBody%2C%20HttpCode.%60200%60(callContext.callContext))%0A%20%20%20%20%7D
Description: the URL-encoded format String, the original code is the OBP connector method body.
DynamicResourceDoc.requestUrl
Example value: /my_user/MY_USER_ID
Description: The URL of the endpoint.
DynamicResourceDoc.requestVerb
Example value: POST
Description: This is the HTTP methods, eg: GET, POST, PUT, DELETE
DynamicResourceDoc.successResponseBody
Example value: {"my_user_id": "some_id_value", "name": "Jhon", "age": 12, "hobby": ["coding"],"optional_fields": ["hobby"]}
Description: the json string of the success response body.
Echo Request Headers
Question: How can I see the request headers that OBP API finally receives from a REST client after the request has passed through HTTP infrastructure such as load balancers, firewalls and proxies?
Answer: If your OBP administrator (you?) sets the following OBP API Props:
echo_request_headers=true
then OBP API will echo all the request headers it receives to the response headers except that every request header name is prefixed with echo_
e.g. if you send the request header:value "DirectLogin:hello" it will be echoed in the response headers as "echo_DirectLogin:hello"
Note: HTTP/2.0 requires that header names must be lower case. This can be a source of confusion as some libraries / tools may drop or convert header names to lowercase.
Endpoint
The terms Endpoint and API (Application Programming Interface) are used somewhat interchangeably. However, an Endpoint is a specific URL defined by its path (eg. /obp/v4.0/root) and its http verb (e.g. GET, POST, PUT, DELETE etc).
Endpoints are like arrows into a system. Like any good computer function, endpoints should expect much and offer little in return. They should fail early and be clear about any reason for failure. In other words each endpoint should have a tight and limited contract with any caller - and especially the outside world!
In OBP, all system endpoints are RESTful - and most Open Banking Standards are RESTful. However, it is possible to create non-RESTful APIs in OBP using the Create Endpoint endpoints.
You can immediately tell if an endpoint is not RESTful by seeing a verb in the URL. For example:
POST /customers is RESTful = GOOD
POST /create-customer is NOT RESTful (due to the word "create") = BAD
RESTful APIs use resource names in URL paths. You can think of RESTful resources like database tables. You wouldn't name a database table "create-customer", so don't use that in a URL path.
If we consider interacting with a Customers table, we read the data using GET /Customers and write to the table using POST /Customers. This model keeps the names clear and predictable.
Note that we are only talking about the front end interface here - anything could be happening in the backend - and that is one of the beauties of APIs. For instance GET /Customers could call 5 different databases and 3 XML services in the background. Similarly POST /Customers could insert into various different tables and backend services. The important thing is that the user of the API (The Consumer or Client in OAuth parlance) has a simple and consistent experience.
In OBP, all Endpoints are implemented by Partial Functions. A Partial Function is a function which only accepts (and responds) to calls with certain parameter values. In the case of API Endpoints the inputs to the Partial Functions are the URL path and http verb. Note that it would be possible to have different Partial Functions respond even to different query parameters, but for OBP static endpoints at least, we take the approach of URL path + http Verb is handled by one Partial Function.
Each Partial Function is identified by an Operation ID which uniquely identifies the endpoint in the system. Having an Operation ID allows us to decorate the Endpoint with metadata (e.g. Tags) and surround the Endpoint with behaviour such as JSON Schema Validation.
See also API
Endpoint Mapping
Endpoint Mapping can be used to map each JSON field in a Dynamic Endpoint to different Dynamic Entity fields.
This document assumes you already have some knowledge of OBP Dynamic Endpoints and Dynamic Entities.
To enable Endpoint Mapping for your Dynamic Endpoints, either set the host in the swagger file to "dynamic_entity" upon creation of the Dynamic Endpoints - or update the host using the Update Dynamic Endpoint Host endpoints.
Once the host is thus set, you can use the Endpoint Mapping endpoints to map the Dynamic Endpoint fields to Dynamic Entity data.
See the Create Endpoint Mapping JSON body. You will need to know the operation_id in advance and you can prepare the request_mapping and response_mapping objects. You can get the operation ID from the API Explorer or Get Dynamic Endpoints endpoints.
For more details and a walk through, please see the following video:
EndpointTag.endpointTagId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A string that MUST uniquely identify the endpointTag on this OBP instance, can be used in all cache.
FAPI 1.0
The Financial-grade API is a highly secured OAuth profile that aims to provide specific implementation guidelines for security and interoperability.
The Financial-grade API security profile can be applied to APIs in any market area that requires a higher level of security than provided by standard OAuth or OpenID Connect.
Financial-grade API Security Profile 1.0 consists of the following parts:
- Financial-grade API Security Profile 1.0 - Part 1: Baseline
- Financial-grade API Security Profile 1.0 - Part 2: Advanced
These parts are intended to be used with RFC6749, RFC6750, RFC7636, and OIDC.
FAPI 2.0
FAPI 2.0 has a broader scope than FAPI 1.0.
It aims for complete interoperability at the interface between client and authorization server as well as interoperable security mechanisms at the interface between client and resource server.
It also has a more clearly defined attacker model to aid formal analysis.
Please note that FAPI 2.0 is still in draft.
FX-Rates
You can use the following endpoint to get the FX Rates available on this OBP instance: Get FX Rates
Gateway Login
Introduction
Note: Gateway Login is NOT enabled on this instance!
Gateway Login Authorisation is made by including a specific header (see step 3 below) in any OBP REST call.
Note: Gateway Login does not require an explicit POST like Direct Login to create the token.
The Gateway is responsible for creating a token which is trusted by OBP absolutely!
When OBP recieves a token via Gateway Login, OBP creates or gets a user based on the username supplied.
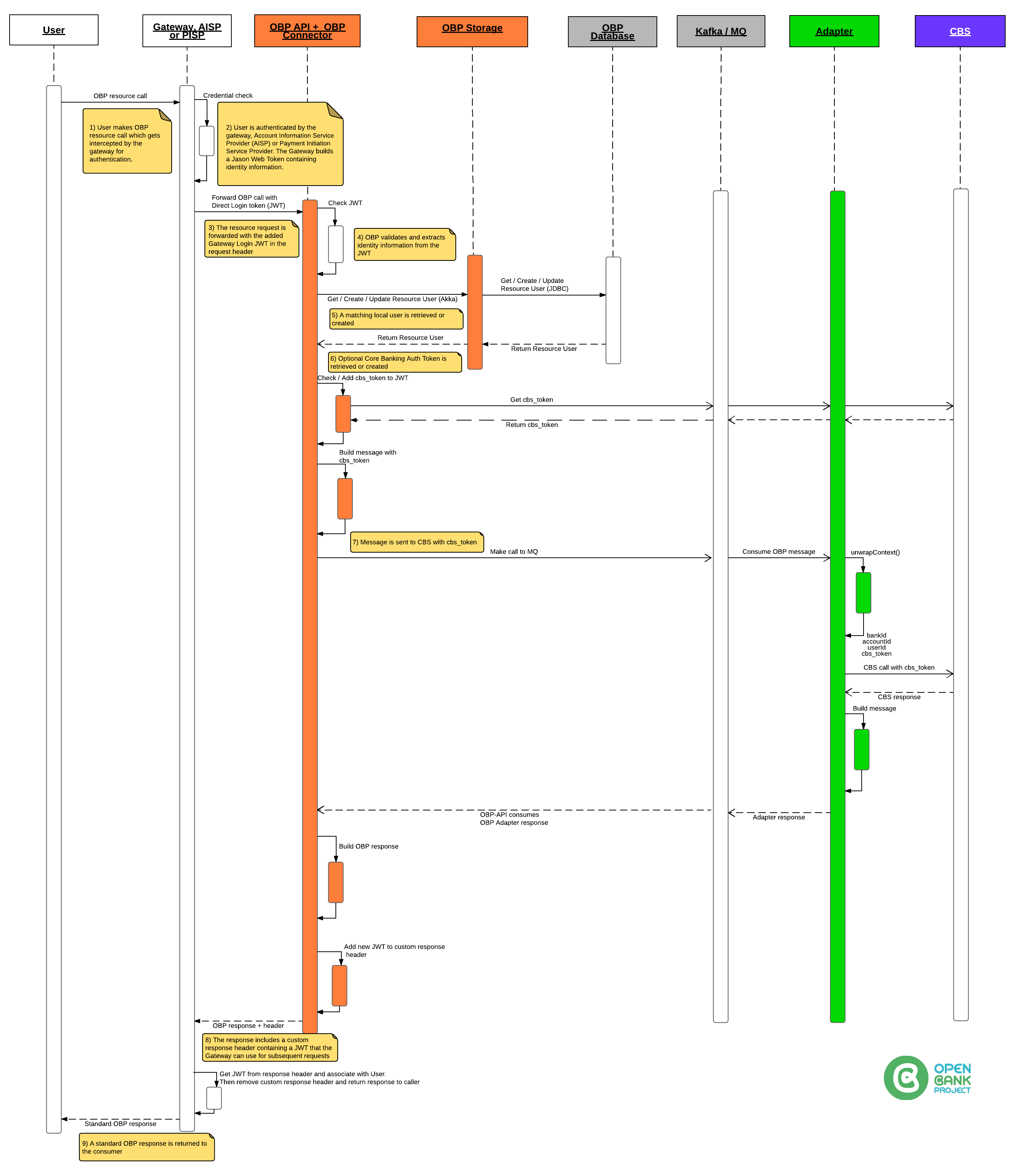
To use Gateway Login:
1) Configure OBP API to accept Gateway Login.
Set up properties in a props file
# -- Gateway login --------------------------------------
# Enable/Disable Gateway communication at all
# In case isn't defined default value is false
# allow_gateway_login=false
# Define comma separated list of allowed IP addresses
# gateway.host=127.0.0.1
# Define secret used to validate JWT token
# jwt_token_secret=your-at-least-256-bit-secret-token
# -------------------------------------- Gateway login --
Please keep in mind that property jwt_token_secret is used to validate JWT token to check it is not changed or corrupted during transport.
2) Create / have access to a JWT
HEADER:ALGORITHM & TOKEN TYPE
{
"alg": "HS256",
"typ": "JWT"
}
PAYLOAD:DATA
{
"login_user_name": "username",
"is_first": false,
"app_id": "85a965f0-0d55-4e0a-8b1c-649c4b01c4fb",
"app_name": "GWL",
"time_stamp": "2018-08-20T14:13:40Z",
"cbs_token": "your_token",
"cbs_id": "your_cbs_id",
"session_id": "123456789"
}
VERIFY SIGNATURE
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
) your-at-least-256-bit-secret-token
Here is the above example token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJsb2dpbl91c2VyX25hbWUiOiJ1c2VybmFtZSIsImlzX2ZpcnN0IjpmYWxzZSwiYXBwX2lkIjoiODVhOTY1ZjAtMGQ1NS00ZTBhLThiMWMtNjQ5YzRiMDFjNGZiIiwiYXBwX25hbWUiOiJHV0wiLCJ0aW1lX3N0YW1wIjoiMjAxOC0wOC0yMFQxNDoxMzo0MFoiLCJjYnNfdG9rZW4iOiJ5b3VyX3Rva2VuIiwiY2JzX2lkIjoieW91cl9jYnNfaWQiLCJzZXNzaW9uX2lkIjoiMTIzNDU2Nzg5In0.
bfWGWttEEcftiqrb71mE6Xy1tT_I-gmDPgjzvn6kC_k
3) Try a REST call using the header
Using your favorite http client:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/users/current
Body
Leave Empty!
Headers:
Authorization: GatewayLogin token="your-jwt-from-step-above"
Here is it all together:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/users/current HTTP/1.1
Host: localhost:8080
User-Agent: curl/7.47.0
Accept: /
Authorization: GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0.
KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU"
CURL example
curl -v -H 'Authorization: GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJsb2dpbl91c2VyX25hbWUiOiJ1c2VybmFtZSIsImlzX2ZpcnN0IjpmYWxzZSwiYXBwX2lkIjoiODVhOTY1ZjAtMGQ1NS00ZTBhLThiMWMtNjQ5YzRiMDFjNGZiIiwiYXBwX25hbWUiOiJHV0wiLCJ0aW1lX3N0YW1wIjoiMjAxOC0wOC0yMFQxNDoxMzo0MFoiLCJjYnNfdG9rZW4iOiJ5b3VyX3Rva2VuIiwiY2JzX2lkIjoieW91cl9jYnNfaWQiLCJzZXNzaW9uX2lkIjoiMTIzNDU2Nzg5In0.
bfWGWttEEcftiqrb71mE6Xy1tT_I-gmDPgjzvn6kC_k"' https://apisandbox.openbankproject.com/obp/v3.0.0/users/current
You should receive a response like:
{
"user_id": "33fd104f-3e6f-4025-97cc-b76bbdc9148e",
"email": "marko@tesobe.com",
"provider_id": "marko.milic",
"provider": "https://tesobe.openbankproject.com",
"username": "marko.milic",
"entitlements": {
"list": []
}
}
and custom response header i.e. OBP returns a new token in the custom response header called GatewayLogin (to the Gateway)
{
"username": "simonr",
"CBS_auth_token": "fapsoidfuipoi889w3ih", (Encrypted by OBP Adapter)
"timestamp": "timestamp",
"consumer_id": "123",
"consumer_name": "Name of Consumer"
}
GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0.
KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU"
Example python script
import jwt
from datetime import datetime, timezone
import requests
env = 'local'
DATE_FORMAT = '%Y-%m-%dT%H:%M:%SZ'
obp_api_host = 'https://yourhost.com'
payload = {
"login_user_name": "username",
"is_first": False,
"app_id": "85a965f0-0d55-4e0a-8b1c-649c4b01c4fb",
"app_name": "Name",
"time_stamp": datetime.now(timezone.utc).strftime(DATE_FORMAT),
"cbs_token": "yourtokenforcbs",
"cbs_id": "yourcbs_id",
"session_id": "123456789"
}
token = jwt.encode(payload, 'your-at-least-256-bit-secret-token', algorithm='HS256').decode("utf-8")
authorization = 'GatewayLogin token="{}"'.format(token)
headers = {'Authorization': authorization}
url = obp_api_host + '/obp/v4.0.0/users/current'
req = requests.get(url, headers=headers)
print(req.text)
Under the hood
The file, GatewayLogin.scala handles the Gateway Login.
We:
-> Check if Props allow_gateway_login is true
-> Check if GatewayLogin header exists
-> Check if getRemoteIpAddress is OK
-> Look for "token"
-> If "is_first" is true -OR- CBS_auth_token is empty then, call CBS to get accounts
The CBS_auth_token (either the new one from CBS or existing one from previous token) is returned in the GatewayLogin custom response header.
More information
Parameter names and values are case sensitive.
Each parameter MUST NOT appear more than once per request.
Hola App log trace
Please see:
[OBP Hola App Log Trace](https://github.com/OpenBankProject/OBP-API/wiki/Log-trace-of-the-Hola-App-performing-Georgian-flavour-of-Berlin-Group-authentication,-consent-generation-and-consuming-Berlin-Group-Account,-Balance-and-Transaction-resources)
How OpenID Connect Works
The OpenID Connect protocol, in abstract, follows these steps:
- End user navigates to a website or web application via a browser.
- End user clicks sign-in and types their username and password.
- The RP (Client) sends a request to the OpenID Provider (OP).
- The OP authenticates the User and obtains authorization.
- The OP responds with an Identity Token and usually an Access Token.
- The RP can send a request with the Access Token to the User device.
- The UserInfo Endpoint returns Claims about the End-User.
Terminology
Authentication
The secure process of establishing and communicating that the person operating an application or browser is who they claim to be.
Client
A client is a piece of software that requests tokens either for authenticating a user or for accessing a resource (also often called a relying party or RP).
A client must be registered with the OP. Clients can be web applications, native mobile and desktop applications, etc.
Relying Party (RP)
RP stands for Relying Party, an application or website that outsources its
user authentication function to an IDP.
OpenID Provider (OP) or Identity Provider (IDP)
An OpenID Provider (OP) is an entity that has implemented the OpenID Connect and OAuth 2.0 protocols,
OP’s can sometimes be referred to by the role it plays, such as: a security token service,
an identity provider (IDP), or an authorization server.
Identity Token
An identity token represents the outcome of an authentication process.
It contains at a bare minimum an identifier for the user (called the sub aka subject claim)
and information about how and when the user authenticated. It can contain additional identity data.
User
A user is a person that is using a registered client to access resources.
JSON Schema Validation
JSON Schema is "a vocabulary that allows you to annotate and validate JSON documents".
By applying JSON Schema Validation to your OBP endpoints you can constrain POST and PUT request bodies. For example, you can set minimum / maximum lengths of fields and constrain values to certain lists or regular expressions.
See JSONSchema.org for more information about the JSON Schema standard.
To create a JSON Schema from an any JSON Request body you can use JSON Schema Net
(The video link below shows how to use that)
Note: OBP Dynamic Entities also use JSON Schema Validation so you don't need to additionally wrap the resulting endpoints with extra JSON Schema Validation but you could do.
You can apply JSON schema validations to any OBP endpoint's request body using the POST and PUT endpoints listed in the link below.
PLEASE SEE the following video explanation: JSON schema validation of request for Static and Dynamic Endpoints and Entities
Just In Time Entitlements
Just in Time Entitlements are ENABLED on this instance.
This is how Just in Time Entitlements work:
If Just in Time Entitlements are enabled then OBP does the following:
If a user is trying to use a Role (via an endpoint) and the user could grant them selves the required Role(s), then OBP automatically grants the Role.
i.e. if the User already has canCreateEntitlementAtOneBank or canCreateEntitlementAtAnyBank then OBP will automatically grant a role that would be granted by a manual process anyway.
This speeds up the process of granting of roles. Certain roles are excluded from this automation:
- CanCreateEntitlementAtOneBank
- CanCreateEntitlementAtAnyBank
If create_just_in_time_entitlements is again set to false after it was true for a while, any auto granted Entitlements to roles are kept in place.
Note: In the entitlements model we set createdbyprocess=create_just_in_time_entitlements. For manual operations we set createdbyprocess=manual
To enable / disable this feature set the Props create_just_in_time_entitlements=true or false. The default is false.
KYC (Know Your Customer)
KYC is the process by which the Bank can be assured that the customer is who they say they are.
OBP provides a number of endpoints that KYC Apps can interact with in order to get and store relevant data and update the KYC status of a Customer.
For instance:
1) Use KYC documents to add information about passports, ID cards, driving licenses including:
- customer_number
- type (of document)
- number (of document)
- issue_date
- issue_place
- expiry_date
For more info see here.
2) Use KYC check to record a check of the customer via phone call, in person meeting or PEP database search.
KYC Checks store:
- customer_number
- date
- how (FACE_TO_FACE_MEETING, PHONE_INTERVIEW, PEP_SEARCH)
- staff_user_id (who recorded the record)
- staff_name (who recorded the record)
- satisfied (True/False)
- comments
For more info see here.
3) Use KYC Media to add media (image or video etc.) related to:
A) the documents listed in KYC documents
B) media that identifies the user e.g. a video ident.
C) media that relates to a KYC check
KYC Media stores:
- customer_number
- type
- url
- date
- relates_to_kyc_document_id
- relates_to_kyc_check_id
For more information see here.
4) Use KYC status to update the KYC status of a customer following a meeting or using one of the above calls.
KYC status stores:
- customer_number
- ok (True/False)
- date
For more information see here.
5) Use other Customer related endpoints shown here to check for known Addresses, contact details, Tax Residences etc.
Keycloak Onboarding
Keycloak Onboarding Guide
Overview
Keycloak is an open-source identity and access management solution that provides production-grade OpenID Connect (OIDC) and OAuth 2.0 authentication services for the OBP-API. It serves as a centralized authentication provider that enables secure user authentication, authorization, and user management for banking applications.
What is Keycloak?
Keycloak is a comprehensive identity provider that offers:
- Single Sign-On (SSO) capabilities across multiple applications
- Identity Federation with external identity providers (Google, Facebook, LDAP, etc.)
- User Management with role-based access control
- Multi-factor Authentication (MFA) support
- Standards Compliance with OAuth 2.0, OpenID Connect, and SAML 2.0
Prerequisites for Onboarding
System Requirements
- Docker or Java 11+ for running Keycloak
- Network access to Keycloak instance (default:
localhost:7787) - Administrative access to configure realms and clients
OBP-API Configuration
Before integrating with Keycloak, ensure your OBP-API instance has the following properties configured:
Enable OAuth2 login
allow_oauth2_login=true
Keycloak-specific configuration
oauth2.oidc_provider=keycloak
oauth2.keycloak.host=http://localhost:7787
oauth2.keycloak.realm=master
oauth2.keycloak.issuer=http://localhost:7787/realms/master
oauth2.jwk_set.url=http://localhost:7787/realms/master/protocol/openid-connect/certs
Step-by-Step Onboarding Process
1. Setting Up Keycloak Instance
Option A: Using Docker (Recommended for Development)
The OBP project provides a pre-configured Keycloak Docker image available at:
Docker Hub: https://hub.docker.com/r/openbankproject/obp-keycloak/tags
Inspect Available Tags
First, check available image tags:
docker search openbankproject/obp-keycloak
Common available tags:
- main-themed: Latest themed version with OBP branding
- latest: Standard latest version
- dev: Development version
- Version-specific tags (e.g., 21.1.2-themed)
Pull and Inspect the Image
Pull the OBP-themed Keycloak image
docker pull openbankproject/obp-keycloak:main-themed
Inspect image details
docker inspect openbankproject/obp-keycloak:main-themed
View image layers and size
docker images | grep openbankproject/obp-keycloak
Check image history
docker history openbankproject/obp-keycloak:main-themed
Basic Container Setup
Run Keycloak container with basic configuration
docker run -p 7787:8080 -e KEYCLOAK_ADMIN=admin -e KEYCLOAK_ADMIN_PASSWORD=admin \
openbankproject/obp-keycloak:main-themed start-dev
Advanced Container Setup with Persistent Data
Create a volume for persistent data
docker volume create keycloak_data
Run with persistent data and custom configuration
docker run -d --name obp-keycloak \
-p 7787:8080 \
-e KEYCLOAK_ADMIN=admin \
-e KEYCLOAK_ADMIN_PASSWORD=admin \
-e KC_DB=h2-file \
-e KC_DB_URL_PATH=/opt/keycloak/data/keycloak \
-v keycloak_data:/opt/keycloak/data \
openbankproject/obp-keycloak:main-themed start-dev
Container Management Commands
Check container status
docker ps | grep obp-keycloak
View container logs
docker logs obp-keycloak
Follow logs in real-time
docker logs -f obp-keycloak
Stop the container
docker stop obp-keycloak
Start existing container
docker start obp-keycloak
Remove container (data will be preserved in volume)
docker rm obp-keycloak
Troubleshooting Container Issues
Execute commands inside running container
docker exec -it obp-keycloak bash
Check container resource usage
docker stats obp-keycloak
Inspect container configuration
docker inspect obp-keycloak
Environment Variables and Configuration
The OBP Keycloak image supports these key environment variables:
Admin Configuration:
- KEYCLOAK_ADMIN: Admin username (default: admin)
- KEYCLOAK_ADMIN_PASSWORD: Admin password
- KC_PROXY: Proxy mode (edge, reencrypt, passthrough)
Database Configuration:
- KC_DB: Database type (h2-file, postgres, mysql, mariadb)
- KC_DB_URL: Database connection URL
- KC_DB_USERNAME: Database username
- KC_DB_PASSWORD: Database password
Network Configuration:
- KC_HOSTNAME: External hostname for Keycloak
- KC_HTTP_PORT: HTTP port (default: 8080)
- KC_HTTPS_PORT: HTTPS port (default: 8443)
Example with External Database:
docker run -d --name obp-keycloak \
-p 7787:8080 \
-e KEYCLOAK_ADMIN=admin \
-e KEYCLOAK_ADMIN_PASSWORD=securepassword \
-e KC_DB=postgres \
-e KC_DB_URL=jdbc:postgresql://localhost:5432/keycloak \
-e KC_DB_USERNAME=keycloak \
-e KC_DB_PASSWORD=keycloak_password \
openbankproject/obp-keycloak:main-themed start-dev
Option B: Manual Installation
- Download Keycloak from keycloak.org
- Extract and navigate to the Keycloak directory
- Start Keycloak in development mode:
./bin/kc.sh start-dev --http-port=7787
2. Initial Keycloak Configuration
Access Keycloak Admin Console
- Navigate to http://localhost:7787/admin
- Login with admin credentials (admin/admin for Docker setup)
Create or Configure Realm
- Select or create a realm (e.g., "obp" or use "master")
- Configure realm settings:
- SSL required: None (for development) or External requests (for production)
- User registration: Enable if needed
- Login with email: Enable for email-based authentication
3. Configure OBP Client Application
Create Client
- Navigate to Clients → Create Client
- Set Client ID:
obp-client(or your preferred identifier) - Set Client Type:
OpenID Connect - Enable Client authentication
Configure Client Settings
- Root URL: your OBP-API URL
- Valid redirect URIs: callback URL
- Web origins: OBP-API URL
- Access Type:
confidential
Retrieve Client Credentials
- Go to Clients → obp-client → Credentials
- Copy the Client Secret for OBP-API configuration
4. Update OBP-API Configuration
Add the following to your OBP-API properties file:
OpenID Connect Client Configuration
openid_connect_1.button_text=Keycloak Login
openid_connect_1.client_id=obp-client
openid_connect_1.client_secret=YOUR_CLIENT_SECRET_HERE
openid_connect_1.callback_url=https://apisandbox.openbankproject.com/auth/openid-connect/callback
openid_connect_1.endpoint.discovery=http://localhost:7787/realms/master/.well-known/openid-configuration
openid_connect_1.endpoint.authorization=http://localhost:7787/realms/master/protocol/openid-connect/auth
openid_connect_1.endpoint.userinfo=http://localhost:7787/realms/master/protocol/openid-connect/userinfo
openid_connect_1.endpoint.token=http://localhost:7787/realms/master/protocol/openid-connect/token
openid_connect_1.endpoint.jwks_uri=http://localhost:7787/realms/master/protocol/openid-connect/certs
openid_connect_1.access_type_offline=true
5. User Management Setup
Create Test Users
- Navigate to Users → Add User
- Fill in user details:
- Username:
testuser - Email:
testuser@example.com - First Name and Last Name
- Set temporary password in Credentials tab
- Assign appropriate roles if using role-based access control
Configure User Attributes (Optional)
Map additional user attributes that OBP-API might need:
- email (standard)
- name (standard)
- preferred_username (standard)
- Custom attributes as required by your banking application
6. Testing the Integration
Verify Configuration
- Restart OBP-API after configuration changes
- Navigate to OBP-API login page
- Look for "Keycloak Login" button (or your configured button text)
Test Authentication Flow
- Click the Keycloak login button
- Should redirect to Keycloak login page
- Login with test user credentials
- Should redirect back to OBP-API with successful authentication
- Verify user session and JWT token validity
Production Considerations
Security Best Practices
- Use HTTPS for all Keycloak and OBP-API communications
- Strong passwords for admin accounts
- Regular updates of Keycloak version
- Backup realm configurations and user data
- Monitor authentication logs for suspicious activity
Scalability
- Database: Configure external database (PostgreSQL, MySQL) instead of H2
- Clustering: Set up Keycloak cluster for high availability
- Load Balancing: Use load balancer for multiple Keycloak instances
Integration with Banking Systems
- LDAP/Active Directory: Integrate with existing user directories
- Multi-factor Authentication: Enable MFA for enhanced security
- Compliance: Ensure configuration meets banking regulatory requirements
Troubleshooting Common Issues
Authentication Failures
- Check redirect URIs: Ensure they match exactly in both Keycloak and OBP-API
- Verify client credentials: Confirm client ID and secret are correct
- Check realm configuration: Ensure realm name matches in all configurations
JWT Token Issues
- Issuer mismatch: Verify
oauth2.keycloak.issuermatches JWTissclaim - JWKS endpoint: Confirm
oauth2.jwk_set.urlis accessible and returns valid keys - Token expiration: Check token validity periods in Keycloak settings
Network Connectivity
- Firewall rules: Ensure ports 7787 (Keycloak) and 8080 (OBP-API) are accessible
- DNS resolution: Verify hostnames resolve correctly
- SSL certificates: For HTTPS setups, ensure valid certificates
Additional Resources
- Keycloak Official Documentation
- OpenID Connect Specification
- OBP OAuth 2.0 Client Credentials Flow Manual
- OBP OIDC Configuration Guide
Support
For issues related to Keycloak integration with OBP-API:
1. Check the OBP-API logs for detailed error messages
2. Verify Keycloak server logs for authentication issues
3. Consult the OBP community forums or GitHub issues
4. Review the comprehensive troubleshooting section in the OBP documentation
Message Doc
OBP can communicate with core banking systems (CBS) and other back end services using a "Connector -> Adapter" approach.
The OBP Connector is a core part of the OBP-API and is written in Scala / Java and potentially other JVM languages.
The OBP Connector implements multiple functions / methods in a style that satisfies a particular transport / protocol such as HTTP REST, Akka or RabbitMq.
An OBP Adapter is a separate software component written in any programming language that responds to requests from the OBP Connector.
Requests are sent by the Connector to the Adapter (or a message queue).
The Adapter must satisfy the Connector method's request for data (or return an error).
"Message Docs" are used to define and document the request / response structure.
Message Docs are visible in the API Explorer.
Message Docs are also available over the Message Doc endpoints.
Each Message Doc relates to one OBP function / method.
The Message Doc includes:
1) The Name of the internal OBP function / method e.g. getAccountsForUser
2) The Outbound Message structure.
3) The Inbound Message structure.
4) The Connector name which denotes the protocol / transport used (e.g. REST, Akka, RabbitMq etc)
5) Outbound / Inbound Topic
6) A list of required Inbound fields
7) A list of dependent endpoints.
The perspective is that of the OBP-API Connector i.e. the OBP Connector sends the message Out, and it receives the answer In.
The Outbound message contains several top level data structures:
1) The outboundAdapterCallContext
This tells the Adapter about the specific REST call that triggered the request and contains the correlationId to uniquely identify the REST call, the consumerId to identify the API Consumer (App) and a generalContext which is a list of key / value pairs that give the Adapter additional custom information about the call.
2) outboundAdapterAuthInfo
This tells the Adapter about the authenticated User that is making the call including: the userId, the userName, the userAuthContext (a list of key / value pairs that have been validated using SCA (see the UserAuthContext endpoints)) and other optional structures such as linked Customers and Views on Accounts to further identify the User.
3) The body
The body contains named fields that are specific to each Function / Message Doc.
For instance, getTransaction might send the bankId, accountId and transactionId so the Adapter can route the request based on bankId and check User permissions on the AccountId before retrieving a Transaction.
The Inbound message
The Inbound message is the reply or response from the Adapter and has the following structure:
1) The inboundAdapterCallContext
This is generally an echo of the outboundAdapterCallContext so the Connector can double check the target destination of the response.
2) The status
This contains information about status of the response including any errorCode and a list of backendMessages.
3) The data
This contains the named fields and their values which are specific to each Function / Message Doc.
The Outbound / Inbound Topics are used for routing in multi OBP instance / RabbitMq installations. (so OBP nodes only listen only to the correct Topics).
The dependent endpoints are listed to facilitate navigation in the API Explorer so integrators can test endpoints during integration.
Message Docs can be generated automatically using OBP code tools. Thus, it's possible to create custom connectors that follow specific protocol and structural patterns e.g. for message queue X over XML format Y.
Method Routing
Open Bank Project can have different connectors, to connect difference data sources.
We support several sources at the moment, eg: databases, rest services, stored procedures and RabbitMq.
If OBP set connector=star, then you can use this method routing to switch the sources.
And we also provide the fields mapping in side the endpoints. If the fields in the source are different from connector,
then you can map the fields yourself.
The following videos are available:
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) is a multi-step account login process that requires users to enter more information than just a password. For example, along with the password, users might be asked to enter a code sent to their email, answer a secret question, or scan a fingerprint.
My-Dynamic-Entities
My Dynamic Entities are user-scoped endpoints that are automatically generated when you create a Dynamic Entity with hasPersonalEntity set to true (which is the default).
How it works:
- Create a Dynamic Entity definition (System or Bank Level) with hasPersonalEntity = true
- OBP automatically generates both regular CRUD endpoints AND 'my' endpoints
- The 'my' endpoints only return data created by the authenticated user
Example workflow:
Step 1: Create a Dynamic Entity definition
POST /management/system-dynamic-entities
{
"hasPersonalEntity": true,
"CustomerPreferences": {
"description": "User preferences",
"required": ["theme"],
"properties": {
"theme": {"type": "string"},
"language": {"type": "string"}
}
}
}
Step 2: Use the auto-generated 'my' endpoints:
- POST /my/CustomerPreferences - Create my preference
- GET /my/CustomerPreferences - Get all my preferences
- GET /my/CustomerPreferences/ID - Get one of my preferences
- PUT /my/CustomerPreferences/ID - Update my preference
- DELETE /my/CustomerPreferences/ID - Delete my preference
For bank-level entities:
- POST /banks/BANK_ID/my/CustomerPreferences
- GET /banks/BANK_ID/my/CustomerPreferences
- GET /banks/BANK_ID/my/CustomerPreferences/ID
- PUT /banks/BANK_ID/my/CustomerPreferences/ID
- DELETE /banks/BANK_ID/my/CustomerPreferences/ID
Key differences:
- Regular endpoints (e.g., /CustomerPreferences): Access ALL entities (requires roles)
- My endpoints (e.g., /my/CustomerPreferences): Access only your own entities (user-scoped)
Note: If hasPersonalEntity is set to false, no 'my' endpoints are generated.
Management endpoints for Dynamic Entity definitions:
- GET /my/dynamic-entities - Get all Dynamic Entity definitions I created
- PUT /my/dynamic-entities/DYNAMIC_ENTITY_ID - Update a definition I created
Required roles:
- CanCreateSystemLevelDynamicEntity - To create system level dynamic entities
- CanCreateBankLevelDynamicEntity - To create bank level dynamic entities
For general information about Dynamic Entities, see here
OAuth 1.0a
The following steps will explain how to connect an instance of the Open Bank Project OAuth Server 1.0a. This authentication mechanism is necessary so a third party application can consume the Open Bank project API securely.
The following documentation is based on the OAuth 1.0a specification so if you need more details you can refer to it.
Before starting to interact with the API, third party applications needs to get OAuth keys (consumer key and secret key). You can register your application here to get those keys for interacting with real data. If you want to use the sandbox before handling real data, please register your application here
1) Obtain a request token
To start a sign in flow, the application must obtain a request token by sending a signed message to :
POST https://apisandbox.openbankproject.com/oauth/initiate
-
oauth_callback: an absolute URI back to which the server will redirect the resource owner (user) when Authorization step is completed. If the application is unable to receive callbacks the parameter value MUST be set to “oob” (case sensitive), to indicate an out-of-band configuration.
-
oauth_consumer_key : The identifier portion of the client credentials (consumer key) which is obtained after application registration.
-
oauth_nonce : A nonce is a random string, uniquely generated by the client to allow the server to verify that a request has never been made before. The nonce value MUST be unique across all requests with the same timestamp, application credentials, and token combinations.
-
oauth_signature : the result of signing the request. Explained in detail here.
-
oauth_signature_method : The name of the signature method that will be used by the application to sign the request, as defined in OAuth protocol. The Open Bank Project OAuth server support "SHA1" and "SHA256" so the parameter MUST be set to “HMAC-SHA1" or “HMAC-SHA256”
-
oauth_timestamp : The timestamp value MUST be a positive integer and is expressed in the number of seconds since January 1, 1970 00:00:00 GMT.
-
oauth_version : OPTIONAL. If present, MUST be set to "1.0". Provides the version of the authentication process as defined in the OAuth 1.0 protocol specification.
Example:
POST /oauth/initiate HTTP/1.1
Host: https://apisandbox.openbankproject.com
Authorization: OAuth
oauth_callback="http%3A%2F%2Fprinter.example.com%2Fready",
oauth_consumer_key="cChZNFj6T5R0TigYB9yd1w",
oauth_nonce="ea9ec8429b68d6b77cd5600adbbb0456",
oauth_signature="F1Li3tvehgcraF8DMJ7OyxO4w9Y%3D",
oauth_signature_method="HMAC-SHA256",
oauth_timestamp="1318467427",
oauth_version="1.0"
important: We will explain below in the "signature" section how to calculate the value of the "oauth_signature" field.
Note : line breaks are for display purposes only, the application MUST send the parameters on one line and the only separator between the parameters is a coma “,”.
The server validates the request and replies with a set of temporary credentials in the body of the HTTP response.
Example (line breaks are for display purposes only) :
HTTP/1.1 200 OK
Content-Type: application/x-www-form-urlencoded
oauth_token=hh5s93j4hdidpola&oauth_token_secret=hdhd0244k9j7ao03&oauth_callback_confirmed=true
The application should examine the HTTP status of the response. Any value other than 200 indicates a failure. The body of the response will contain the oauth_token, oauth_token_secret, and oauth_callback_confirmed parameters. The application should verify that oauth_callback_confirmed is true and store the other two values for the next steps.
2) Redirect the user
The next step is to direct the user to Open Bank Project so that he may complete the authentication.
Direct the user to :
GET oauth/authorize
and the request token obtained in step 1 should be passed as the oauth_token parameter.
The most seamless way for a website to implement this would be to issue a HTTP 302 redirect as the response to the original request. Mobile and desktop applications should open a new browser window or direct to the URL via an embedded web view.
Example :
https://apisandbox.openbankproject.com/oauth/authorize?oauth_token=NPcudxy0yU5T3tBzho7iCotZ3cnetKwcTIRlX0iwRl0
Upon a successful authentication, the callback URL would receive a request containing the oauth_token and oauth_verifier parameters. The application should verify that the token matches the request token received in step 1.
If the callback URL was not specified (oob) than the verifier will be shown in the page and the user has to enter it into the application manually.
3) Convert the request token to an access token
To convert the request token into a usable access token, the application must make a:
POST https://apisandbox.openbankproject.com/oauth/token
request containing the oauth_verifier value obtained in step 2. The request token is also passed as oauth_token parameter of the header.
Note : The oauth_callback_url parameter is not necessary any more.
Example :
POST /oauth/token HTTP/1.1
Host: https://apisandbox.openbankproject.com
Authorization: OAuth
oauth_verifier="9312832",
oauth_token=”aze2342352aze”,
oauth_consumer_key="cChZNFj6T5R0TigYB9yd1w",
oauth_nonce="ea9ec8429b68d6b77cd5600adbbb0456",
oauth_signature="F1Li3tvehgcraF8DMJ7OyxO4w9Y%3D",
oauth_signature_method="HMAC-SHA256",
oauth_timestamp="1318467427",
oauth_version="1.0"
Like the step 1, a successful response contains the oauth_token & oauth_token_secret and they should be stored and used for future authenticated requests to the OBP API.
The application can now use the access token to access protected resources.
4) Access protected resources
Once the application has an a access token and secret token, it can access protected resources. The request is the same as in step 3 except the oauth_verifer which MUST not be included in the header.
Please see the API documentation for more details on how to access protected resources.
Recommended OAuth 1.0 libraries:
If you want to use a OAuth library to handle the OAuth process for your application, we have successfully tested these ones:
- JAVA:
signpost. Warning any version below 1.2.1.2 probably will not work. Version 1.2 which is the current Maven version seems to cause problems.
- PHP:
OAuth Consumer And Server Library
- Scala:
- OBP SDKs / examples of client code with OAuth:
Examples :
To show the OAuth integration in concrete examples, please check out these projects listed here:
Hello-OBP-OAuth1.0a-LANGUAGE/PLATFORM
Signature :
According to the section-3.4 in the OAuth 1.0 protocol specification the signature computation is done following theses steps :
a) Signature Base String :
The signature base string is a consistent, reproducible concatenation of several of the HTTP request elements into a single string. The string is used as an input to the signature methods.
The signature base string includes the following components of the HTTP request:
-
The HTTP request method (e.g., "GET", "POST", etc.).
-
The authority as declared by the HTTP "Host" request header field.
-
The path and query components of the request resource URI.
-
he protocol parameters excluding the "oauth_signature".
The signature base string does not cover the entire HTTP request. Most notably, it does not include the entity-body in most requests, nor does it include most HTTP entity-headers.
The signature base string is constructed by concatenating together, in order, the following HTTP request elements:
-
The HTTP request method in uppercase. For example: "HEAD", "GET", "POST", etc. If the request uses a custom HTTP method, it MUST be encoded (Section 3.6).
-
An "&" character (ASCII code 38).
-
The base string URI from Section 3.4.1.2, after being encoded (Section 3.6).
-
An "&" character (ASCII code 38).
-
The request parameters as normalized in Section 3.4.1.3.2, after being encoded (Section 3.6).
Explained shortly below the example.
Example:
POST /oauth/token HTTP/1.1
Host: https://apisandbox.openbankproject.com
Content-Type: application/x-www-form-urlencoded
Authorization: OAuth
oauth_consumer_key="91919",
oauth_token="OGESD9MrWQEGPXOyPjHCRrCw7BPelWJjnomibV6bePU",
oauth_signature_method="HMAC-SHA256",
oauth_timestamp="1340878170",
oauth_nonce="DFXOQFZVK8K46KDR11",
oauth_signature="bYT5CMsGcbgUdFHObYMEfcx6bsw%3D"
Is represented by the following signature base string (line breaks are for display purposes only):
POST&https%3A%2F%2Fhttps://apisandbox.openbankproject.com&oauth_consumer_key%3D91919%26oauth_nonce%3DDFXOQFZVK8K46KDR11%26oauth_signature_method%3Dhmac-sha256%26oauth_timestamp%3D1340878170%26oauth_token%3DOGESD9MrWQEGPXOyPjHCRrCw7BPelWJjnomibV6bePU%26oauth_verifier%3DT0dXUDBZR09LUVlGTU9NSlhIUUc%26oauth_version%3D1
The request parameters normalization :
-
The name and value of each parameter are encoded Section 3.6.
-
The parameters are sorted by name, using ascending byte value ordering.
-
The name of each parameter is concatenated to its corresponding value using an "=" character (ASCII code 61) as a separator, even if the value is empty.
-
The sorted name/value pairs are concatenated together into a single string by using an "&" character (ASCII code 38) as separator.
B) Signing the request :
The Open Bank Project OAuth 1.0 implementation uses the “HMAC-SHA1” and “HMAC-SHA256” as signing methods. The key to sign the base string is the concatenation of the consumer secret and the token secret with the “&” character in the middle like this: oauth_consumer_secret&oauth_token_secret, in the first step the application does not have yet a token so it will be an empty string.
The signature that results from the signature process MUST be encoded in base 64 also since the protocol requires encoding all the OAuth parameters.
Illustration of integration with a bank back-end :
The following link shows how the integration of the OAuth process would be with a bank back-end: https://github.com/OpenBankProject/OBP-API/wiki/OAuth-Integration-Illustration
OAuth 2
OAuth2 is allowed on this instance.
OAuth2 is an authorization framework that enables applications to obtain limited access to user accounts on an HTTP service, in this case any OBP REST call. It works by delegating user authentication to the service that hosts the user account, and authorizing third-party applications to access the user account. OAuth 2 provides authorization flows for web and desktop applications, and mobile devices.
OAuth2 Roles
The following is a general introduction to a so called "3 legged OAuth2" flow:
- Resource Owner
- Client
- Resource Server
- Authorization Server
Resource Owner: User
The resource owner is the user who authorizes an application to access their account. The application's access to the user's account is limited to the "scope" of the authorization granted (e.g. openid).
Authorization Server: API
The authorization server verifies the identity of the user then issues access tokens to the application. E.g. Hydra
Resource Server: API
The resource server hosts the protected user resources. E.g. OBP-API
Client: Application
The client is the application that wants to access the user's resource. In order to do that, it must be authorized by the user, and the authorization must be validated by the Authorization Server: API.
Authorization Grant
OAuth 2 defines four grant types, each of which is useful in different cases:
-
Authorization Code: used with server-side Applications
-
Implicit: used with Mobile Apps or Web Applications (applications that run on the user's device)
-
Resource Owner Password Credentials: used with trusted Applications, such as those owned by the service itself
-
Client Credentials: used with Applications API access
Step 1: Get your App key
Sign up or login as a developer
Register your App key HERE
Copy and paste the CLIENT ID (AKA CONSUMER KEY), CLIENT SECRET (AKA CONSUMER SECRET) and REDIRECT_URL for the subsequent steps below.
Step 2: Initiate the OAuth 2.0 / OpenID Connect Flow
Once you have registered your App you should initiate the OAuth2 / OIDC flow using the following URL
OBP-00010: Missing props value at this API instance - hydra_public_url/oauth2/auth
WITH THE following parameters:
OBP-00010: Missing props value at this API instance - hydra_public_url/oauth2/auth?client_id=YOUR-CLIENT-ID&response_type=code&state=GENERATED_BY_YOUR_APP&scope=openid+offline+ReadAccountsBasic+ReadAccountsDetail+ReadBalances+ReadTransactionsBasic+ReadTransactionsDebits+ReadTransactionsDetail&redirect_uri=https%3A%2F%2FYOUR-APP.com%2Fmain.html
Step 3: Exchange the code for an access token
The token endpoint is:
OBP-00010: Missing props value at this API instance - hydra_public_url/oauth2/token
For further information please see here
In this sandbox, this will cause the following flow:
1) The User is authenticated using OAuth2 / OpenID Connect against the banks authentication system
2) The User grants consent to the App on the bank's Consent page.
3) The User grants access to one or more accounts that they own on the bank's Account Selection page
4) The User is redirected back to the App where they can now see the Accounts they have selected.
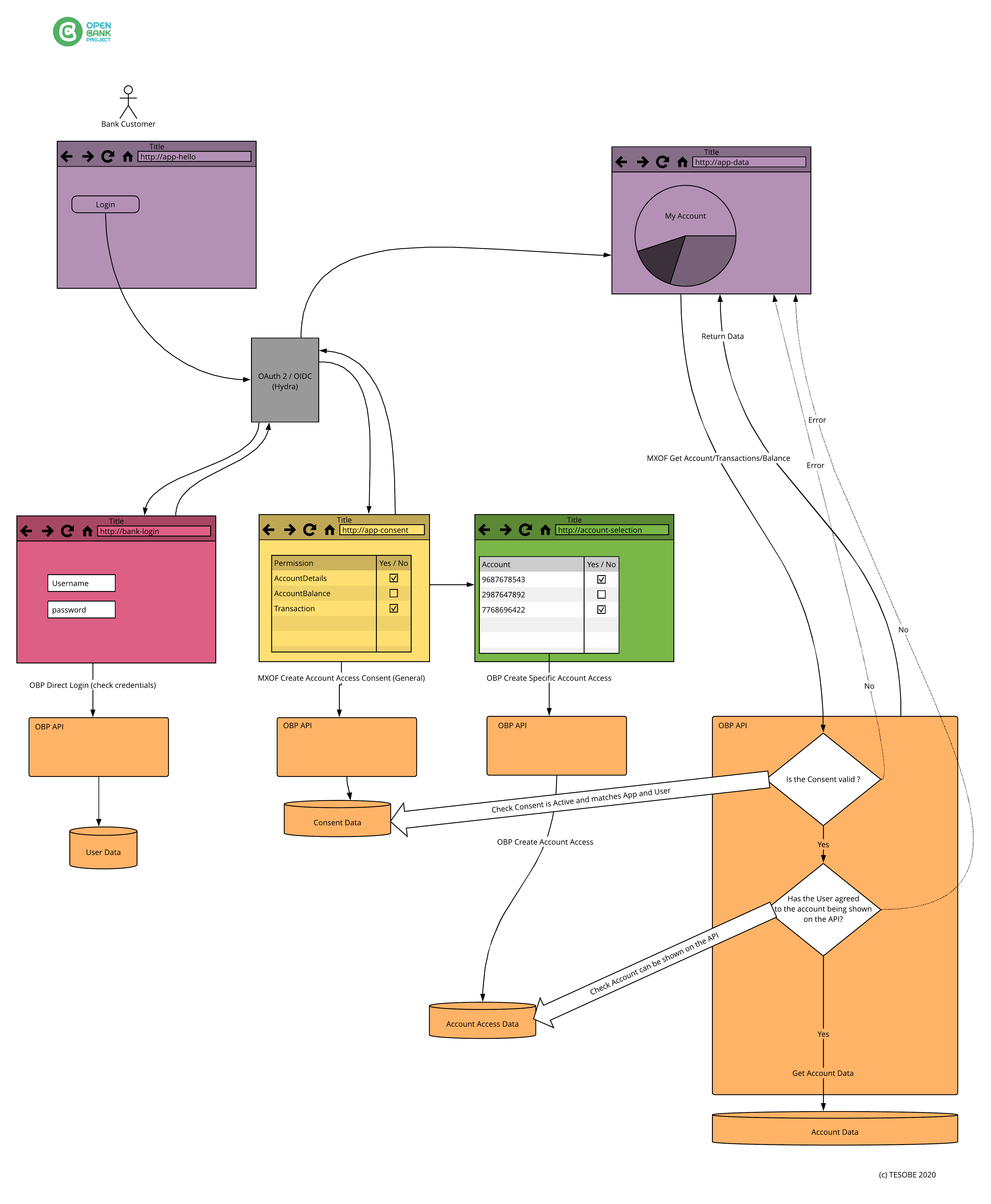
An example Consent Testing App (Hola) using this flow can be found here
OAuth 2.0
OAuth 2.0, is a framework, specified by the IETF in RFCs 6749 and 6750 (published in 2012) designed to support the development of authentication and authorization protocols. It provides a variety of standardized message flows based on JSON and HTTP.
OAuth 2.0 Client Credentials Flow Manual
OAuth 2.0 Client Credentials Flow Manual
Overview
OAuth 2.0 Client Credentials Flow is used when a client application (such as a backend service) needs to authenticate and request access to resources without user interaction. This flow is typically used for machine-to-machine (M2M) authentication.
Prerequisites / Assumptions
Before making requests, ensure you have:
- A valid client_id and client_secret.
- This example assumes the authorization server (Keycloak) is running on localhost:7070. Replace this with the actual auth server URL.
- A realm needs to been configured (e.g. 'master') and respective endpoint available: /realms/master/protocol/openid-connect/token.
1. Requesting an Access Token
To obtain an access token, send a POST request to the token endpoint with the following details.
Request
POST /realms/master/protocol/openid-connect/token HTTP/1.1
Host: localhost:7070
Content-Type: application/x-www-form-urlencoded
Authorization: Basic Og==
Content-Length: 104
client_id=<client_id>&client_secret=<client_secret>&grant_type=client_credentials
Explanation of Parameters
| Parameter | Description |
|---|---|
client_id | The unique identifier for your client application. |
client_secret | The secret key assigned to your client. |
grant_type | Must be set to client_credentials to indicate this authentication flow. |
Example cURL Command
curl -X POST "http://localhost:7070/realms/master/protocol/openid-connect/token" \
-H "Content-Type: application/x-www-form-urlencoded" \
-u "open-bank-project:WWJ04UzMhWmLEqW2KIgBHwD4UNEotzXz" \
-d "grant_type=client_credentials"
2. Expected Response
A successful request will return a JSON response containing the access token:
{
"access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...",
"token_type": "Bearer",
"expires_in": 3600
}
Response Fields
| Field | Description |
|---|---|
access_token | The token required to authenticate API requests. |
token_type | Usually Bearer, meaning it should be included in the Authorization header. |
expires_in | The token expiration time in seconds. |
3. Using the Access Token
Once you obtain the access token, include it in the Authorization header of your subsequent API requests:
Example API Request with Token
curl -X GET "http://localhost:7070/protected/resource" \
-H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9..."
OCSP
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate.
It is described in RFC 6960 and is on the Internet standards track. It was created as an alternative to certificate revocation lists (CRL),
OIDC
An acronym for OpenID Connect (OIDC) is an identity authentication protocol that is an extension of open authorization (OAuth) 2.0 to standardize the process for authenticating and authorizing users when they sign in to access digital services.
OpenID Connect with Google
OAuth2 is allowed on this instance.
OpenID Connect with Google
Introduction
Google's OAuth 2.0 APIs can be used for both authentication and authorization. This document describes our OAuth 2.0 implementation for authentication, which conforms to the OpenID Connect specification, and is OpenID Certified.
For complete documentation please refer to the official doc's page: OpenID Connect

Obtain OAuth 2.0 credentials
Please refer to the official doc's page: OpenID Connect
In case you use Google's OAuth 2.0 Playground
example of an response is shown below:
{
"access_token": "ya29.a0Adw1xeVr_WAYaipiH_6QKCFjIFsnZxW7kbxA8a2RU_uy5meEufErwPDLSHMga8IEQghNSX2GbkOfZUQb6j_fMGHL_HaW3RoULZq5AayUdEjI9bC4TMe-Nd4cZR17C0Rg3GLNzuHTXXe05UyMmNODZ6Up0aXZBBTHl-4",
"id_token": "eyJhbGciOiJSUzI1NiIsImtpZCI6ImE1NDFkNmVmMDIyZDc3YTIzMThmN2RkNjU3ZjI3NzkzMjAzYmVkNGEiLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL2FjY291bnRzLmdvb2dsZS5jb20iLCJhenAiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJhdWQiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJzdWIiOiIxMTM5NjY4NTQyNDU3ODA4OTI5NTkiLCJlbWFpbCI6Im1hcmtvLm1pbGljLnNyYmlqYUBnbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwiYXRfaGFzaCI6ImtrcENIWUFaSTZVOFZiZEJsRHNfX1EiLCJuYW1lIjoiTWFya28gTWlsacSHIiwicGljdHVyZSI6Imh0dHBzOi8vbGg1Lmdvb2dsZXVzZXJjb250ZW50LmNvbS8tWGQ0NGhuSjZURG8vQUFBQUFBQUFBQUkvQUFBQUFBQUFBQUEvQUtGMDVuQ1pyaTdmWHdkUUhuZUNwN09pTVh1WGlOMkpVQS9zOTYtYy9waG90by5qcGciLCJnaXZlbl9uYW1lIjoiTWFya28iLCJmYW1pbHlfbmFtZSI6Ik1pbGnEhyIsImxvY2FsZSI6ImVuIiwiaWF0IjoxNTg0NTIxNDU3LCJleHAiOjE1ODQ1MjUwNTd9.LgwY-OhltYS2p91l2Lt4u5lUR5blR7L8097J0ZpK0GyxWxOlnhSouk9MRMmyfSGuYfWKBtdSUy3Esaphk2f7wpLS-wBx3KJpvrXhgbsyemt9s7eu5bAdHaCteO8MqHPjbU9tych8iH0tA1MSL_tVZ73hy56rS2irzIC33wYDoBf8C5nEOd2uzQ758ydK5QvvdFwRgkLhKDS8vq2qVJTWgtk9VVd5JwJ5OfiVimXfGUzNJmGreEJKj14iUj-78REybpUbI9mGevRhjLPhs51Uc9j-SsdRMymVbVhVxlbsWAPTpjLAJnOodeHzAvmKFkOUfahQHHctx4fl8V3PVYf1aA",
"expires_in": 3599,
"token_type": "Bearer",
"scope": "https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/userinfo.email openid",
"refresh_token": "1//04w7RCdl9ZnG-CgYIARAAGAQSNwF-L9IrNZVxs6fliP7xAlHjKcZpfpw7JoYyBsvxKMD7n0xyB74G8aRlFoBkkCbloETrWMU6yOA"
}
Note: The OAuth Playground will automatically revoke refresh tokens after 24h. You can avoid this by specifying your own application OAuth credentials using the Configuration panel.
An ID token's payload
{
"iss": "https://accounts.google.com",
"azp": "407408718192.apps.googleusercontent.com",
"aud": "407408718192.apps.googleusercontent.com",
"sub": "113966854245780892959",
"email": "marko.milic.srbija@gmail.com",
"email_verified": true,
"at_hash": "nGKRToKNnVA28H6MhwXBxw",
"name": "Marko Milić",
"picture": "https://lh5.googleusercontent.com/-Xd44hnJ6TDo/AAAAAAAAAAI/AAAAAAAAAAA/AKxrwcadwzhm4N4tWk5E8Avxi-ZK6ks4qg/s96-c/photo.jpg",
"given_name": "Marko",
"family_name": "Milić",
locale: "en",
"iat": 1547705691,
"exp": 1547709291
}
Try a REST call using the authorization's header
Using your favorite http client:
GET /obp/v3.0.0/users/current
Body
Leave Empty!
Headers:
Authorization: Bearer ID_TOKEN
Here is it all together:
GET /obp/v3.0.0/users/current HTTP/1.1
Host: https://apisandbox.openbankproject.com
Authorization: Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IjA4ZDMyNDVjNjJmODZiNjM2MmFmY2JiZmZlMWQwNjk4MjZkZDFkYzEiLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL2FjY291bnRzLmdvb2dsZS5jb20iLCJhenAiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJhdWQiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJzdWIiOiIxMTM5NjY4NTQyNDU3ODA4OTI5NTkiLCJlbWFpbCI6Im1hcmtvLm1pbGljLnNyYmlqYUBnbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwiYXRfaGFzaCI6IkFvYVNGQTlVTTdCSGg3YWZYNGp2TmciLCJuYW1lIjoiTWFya28gTWlsacSHIiwicGljdHVyZSI6Imh0dHBzOi8vbGg1Lmdvb2dsZXVzZXJjb250ZW50LmNvbS8tWGQ0NGhuSjZURG8vQUFBQUFBQUFBQUkvQUFBQUFBQUFBQUEvQUt4cndjYWR3emhtNE40dFdrNUU4QXZ4aS1aSzZrczRxZy9zOTYtYy9waG90by5qcGciLCJnaXZlbl9uYW1lIjoiTWFya28iLCJmYW1pbHlfbmFtZSI6Ik1pbGnEhyIsImxvY2FsZSI6ImVuIiwiaWF0IjoxNTQ3NzExMTE1LCJleHAiOjE1NDc3MTQ3MTV9.MKsyecCSKS4Y0C8R4JP0J0d2Oa-xahvMAbtfFrGHncTm8xBgeaNb50XSJn20ak1YyA8hZiRP2M3el0f4eIVQZsMMa22MrwaiL8pLb1zGfawDLPb1RvOmoCWTDJGc_s1qQMlyc21Wenr9rjuu1bQCerGTYM6M0Aq-Uu_GT0lCEjz5WVDI5xDUf4Mhdi8HYq7UQ1kGz1gQFiBm5nI3_xtYm75EfXFeDg3TejaMmy36NpgtwN_vwpHByoHE5BoTl2J55rJ2creZZ7CmtZttm-9HsT6v1vxT8zi0RXObFrZSk-LgfF0tJQcGZ5LXQZL0yMKXPQVFIMCg8J0Gg7l_QACkCA
Cache-Control: no-cache
CURL example:
curl -X GET
https://apisandbox.openbankproject.com/obp/v3.0.0/users/current
-H 'Authorization: Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IjA4ZDMyNDVjNjJmODZiNjM2MmFmY2JiZmZlMWQwNjk4MjZkZDFkYzEiLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL2FjY291bnRzLmdvb2dsZS5jb20iLCJhenAiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJhdWQiOiI0MDc0MDg3MTgxOTIuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJzdWIiOiIxMTM5NjY4NTQyNDU3ODA4OTI5NTkiLCJlbWFpbCI6Im1hcmtvLm1pbGljLnNyYmlqYUBnbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwiYXRfaGFzaCI6IkFvYVNGQTlVTTdCSGg3YWZYNGp2TmciLCJuYW1lIjoiTWFya28gTWlsacSHIiwicGljdHVyZSI6Imh0dHBzOi8vbGg1Lmdvb2dsZXVzZXJjb250ZW50LmNvbS8tWGQ0NGhuSjZURG8vQUFBQUFBQUFBQUkvQUFBQUFBQUFBQUEvQUt4cndjYWR3emhtNE40dFdrNUU4QXZ4aS1aSzZrczRxZy9zOTYtYy9waG90by5qcGciLCJnaXZlbl9uYW1lIjoiTWFya28iLCJmYW1pbHlfbmFtZSI6Ik1pbGnEhyIsImxvY2FsZSI6ImVuIiwiaWF0IjoxNTQ3NzExMTE1LCJleHAiOjE1NDc3MTQ3MTV9.MKsyecCSKS4Y0C8R4JP0J0d2Oa-xahvMAbtfFrGHncTm8xBgeaNb50XSJn20ak1YyA8hZiRP2M3el0f4eIVQZsMMa22MrwaiL8pLb1zGfawDLPb1RvOmoCWTDJGc_s1qQMlyc21Wenr9rjuu1bQCerGTYM6M0Aq-Uu_GT0lCEjz5WVDI5xDUf4Mhdi8HYq7UQ1kGz1gQFiBm5nI3_xtYm75EfXFeDg3TejaMmy36NpgtwN_vwpHByoHE5BoTl2J55rJ2creZZ7CmtZttm-9HsT6v1vxT8zi0RXObFrZSk-LgfF0tJQcGZ5LXQZL0yMKXPQVFIMCg8J0Gg7l_QACkCA'
-H 'Cache-Control: no-cache'
-H 'Postman-Token: aa812d04-eddd-4752-adb7-4d56b3a98f36'
And we get the response:
{
"user_id": "6d411bce-50c1-4eb8-b8b0-3953e4211773",
"email": "marko.milic.srbija@gmail.com",
"provider_id": "113966854245780892959",
"provider": "https://accounts.google.com",
"username": "Marko Milić",
"entitlements": {
"list": []
}
}
QSealC
Qualified electronic Seal Certificate.
A certificate for electronic seals allows the relying party to validate the identity of the subject of the certificate,
as well as the authenticity and integrity of the sealed data, and also prove it to third parties.
The electronic seal provides strong evidence, capable of having legal effect, that given data is originated by the legal entity identified in the certificate.
QWAC
A Qualified Website Authentication Certificate is a qualified digital certificate under the trust services defined in the European Union eIDAS Regulation.
A website authentication certificate makes it possible to establish a Transport Layer Security channel with the subject of the certificate, which secures data transferred through the channel.
Rate Limiting
Rate Limiting controls the number of API requests a Consumer can make within specific time periods. This prevents abuse and ensures fair resource allocation across all API consumers.
Architecture - Single Source of Truth
┌─────────────────────────────────────────────────────────────────────────┐
│ RateLimitingUtil.scala │
│ │
│ ┌───────────────────────────────────────────────────────────────────┐ │
│ │ │ │
│ │ getActiveRateLimitsWithIds(consumerId, date): │ │
│ │ Future[(CallLimit, List[String])] │ │
│ │ │ │
│ │ ═══════════════════════════════════════════════════════ │ │
│ │ Single Source of Truth │ │
│ │ ═══════════════════════════════════════════════════════ │ │
│ │ │ │
│ │ This function calculates active rate limits │ │
│ │ │ │
│ │ Logic: │ │
│ │ 1. Query RateLimiting table for active records │ │
│ │ 2. If found: │ │
│ │ • Sum positive values (> 0) for each period │ │
│ │ • Return -1 if no positive values (unlimited) │ │
│ │ • Extract rate_limiting_ids │ │
│ │ 3. If not found: │ │
│ │ • Return system defaults from props │ │
│ │ • Empty ID list │ │
│ │ 4. Return: (CallLimit, List[rate_limiting_ids]) │ │
│ │ │ │
│ └───────────────────────────────────────────────────────────────────┘ │
│ ▲ │
│ │ │
└──────────────────────────────┼──────────────────────────────────────────┘
│
│ Both callers use
│ the same function
│
┌───────────────┴───────────────┐
│ │
│ │
┌──────────▼──────────┐ ┌──────────▼──────────┐
│ │ │ │
│ AfterApiAuth.scala │ │ APIMethods600.scala │
│ │ │ │
│ checkRateLimiting()│ │ getActiveCallLimits │
│ │ │ AtDate │
│ ───────────────── │ │ ──────────────── │
│ │ │ │
│ Called: Every │ │ Endpoint: │
│ API request │ │ GET /management/ │
│ │ │ consumers/ID/ │
│ Uses: │ │ consumer/active- │
│ (rateLimit, _) │ │ rate-limits/DATE │
│ │ │ │
│ Ignores IDs, │ │ Uses: │
│ just needs the │ │ (rateLimit, ids) │
│ CallLimit for │ │ │
│ enforcement │ │ Returns both in │
│ │ │ JSON response │
│ │ │ │
└─────────────────────┘ └─────────────────────┘
Key Point: There is one function that calculates active rate limits. Both enforcement and API reporting call this one function.
How It Works
- Rate Limit Records: Stored in the
RateLimitingtable with date ranges (from_date, to_date) - Multiple Records: A consumer can have multiple active rate limit records that overlap
- Aggregation: When multiple records are active, their limits are summed together (positive values only)
- Enforcement: On every API request, the system checks Redis counters against the aggregated limits
Time Periods
Rate limits can be set for six time periods:
- per_second_rate_limit: Maximum requests per second
- per_minute_rate_limit: Maximum requests per minute
- per_hour_rate_limit: Maximum requests per hour
- per_day_rate_limit: Maximum requests per day
- per_week_rate_limit: Maximum requests per week
- per_month_rate_limit: Maximum requests per month
A value of -1 means unlimited for that period.
HTTP Headers
When rate limiting is active, responses include:
- X-Rate-Limit-Limit: Maximum allowed requests for the period
- X-Rate-Limit-Remaining: Remaining requests in current period
- X-Rate-Limit-Reset: Seconds until the limit resets
HTTP Status Codes
- 200 OK: Request allowed, headers show current limit status
- 429 Too Many Requests: Rate limit exceeded for a time period
Querying Active Rate Limits
Use the endpoint:
GET /obp/v6.0.0/management/consumers/{CONSUMER_ID}/active-rate-limits/{DATE_WITH_HOUR}
Where DATE_WITH_HOUR is in format YYYY-MM-DD-HH in UTC timezone (e.g., 2025-12-31-13 for hour 13:00-13:59 UTC on Dec 31, 2025).
Returns the aggregated active rate limits for the specified hour, including which rate limit records contributed to the totals.
Rate limits are cached and queried at hour-level granularity for performance. All hours are interpreted in UTC for consistency across all servers.
System Defaults
If no rate limit records exist for a consumer, system-wide defaults are used from properties:
- rate_limiting_per_second
- rate_limiting_per_minute
- rate_limiting_per_hour
- rate_limiting_per_day
- rate_limiting_per_week
- rate_limiting_per_month
Default value: -1 (unlimited)
Example
A consumer with two overlapping rate limit records:
- Record 1: 10 requests/second, 100 requests/minute
- Record 2: 5 requests/second, 50 requests/minute
Aggregated limits: 15 requests/second, 150 requests/minute
Configuration
Enable rate limiting by setting:
use_consumer_limits=true
For anonymous access, configure:
user_consumer_limit_anonymous_access=1000
(Default: 1000 requests per hour)
Related Concepts
- Consumer: The API client subject to rate limiting
- Redis: Storage system for tracking request counts
- Single Source of Truth:
RateLimitingUtil.getActiveRateLimitsWithIds()function calculates all active rate limits
Regulated-Entities
In the context of the Open Bank Project (OBP), a "Regulated Entity" refers to organizations that are recognized and authorized to provide financial services under regulatory frameworks. These entities are overseen by regulatory authorities to ensure compliance with financial regulations and standards.
Key Points About Regulated Entities in OBP:
Endpoint for Retrieval: You can retrieve information about regulated entities using the Get Regulated Entities endpoint. This does not require authentication and provides data on various regulated entities, including their services, entity details, and more.
Creating a Regulated Entity: The API also allows for the creation of a regulated entity using the Create Regulated Entity endpoint. User authentication is required for this operation.
Retrieving Specific Entity Details: To get details of a specific regulated entity, you can use the Get Regulated Entity by Id endpoint, where you need to specify the entity ID. No authentication is needed.
Deleting a Regulated Entity: If you need to remove a regulated entity, the Delete Regulated Entity endpoint is available, but it requires authentication.
Entity Information:
Each regulated entity has several attributes, including:
- Entity Code: A unique identifier for the entity
- Website: The entitys official website URL
- Country and Address Details: Location information for the entity
- Certificate Public Key: Public key used for digital certificates
- Entity Type and Name: Classification and official name of the entity
- Services offered: List of financial services provided by the entity
Regulated entities play a crucial role in maintaining trust and compliance within the financial ecosystem managed through the OBP platform.
Configuration Properties:
Regulated entities functionality is supported by several configuration properties in OBP:
Certificate and Signature Verification (for Berlin Group/PSD2 TPP authentication):
truststore.path.tpp_signature- Path to the truststore containing TPP certificatestruststore.password.tpp_signature- Password for the TPP signature truststoretruststore.alias.tpp_signature- Alias for the TPP signature certificate
Fallback Certificate Configuration:
truststore.path- General truststore path (fallback if TPP-specific not set)keystore.path- Path to the keystore for certificate operationskeystore.password- Password for the keystorekeystore.passphrase- Passphrase for keystore private keyskeystore.alias- Alias for certificate entries in keystore
These properties are used for TPP (Third Party Provider) certificate validation in PSD2/Berlin Group implementations, where regulated entities authenticate using QWAC (Qualified Website Authentication Certificate) or other qualified certificates.
Internal Usage by OBP:
OBP internally uses regulated entities for several authentication and authorization functions:
Certificate-Based Authentication: When the property requirePsd2Certificates=ONLINE is set, OBP automatically validates incoming API requests against registered regulated entities using their certificate information.
Automatic Consumer Creation: For Berlin Group/PSD2 compliance, OBP automatically creates API consumers for TPPs based on their regulated entity registration and certificate validation.
Service Provider Authorization: OBP checks if regulated entities have the required service provider roles (PSP_AI, PSP_PI, PSP_IC, PSP_AS) before granting access to specific API endpoints.
Berlin Group/UK Open Banking Integration: Many Berlin Group (v1.3) and UK Open Banking (v3.1.0) API endpoints automatically call passesPsd2Aisp() and related functions to validate regulated entity certificates.
This integration ensures that only properly registered and certificated Third Party Providers can access sensitive banking data and payment initiation services in compliance with PSD2 regulations.
Real-Time Entity / Certificate Retrieval:
Regulated Entities can be retrieved in real time from the National Authority / National Bank through the following data flow patterns:
Direct National Authority Connection:
OBP BG API instance -> getRegulatedEntities -> Connector -> National Authority
Via OBP Regulated Entities API Instance:
OBP BG API instance -> getRegulatedEntities -> Connector -> OBP Regulated Entities API instance -> Connector -> National Authority
This real-time integration ensures that regulated entity information is always current and reflects the latest regulatory status and certifications from official national sources.
RabbitMQ Message Documentation (other connectors are also available):
- obp.getRegulatedEntities - Retrieve all regulated entities
- obp.getRegulatedEntityByEntityId - Retrieve a specific regulated entity by ID
For instance, a National Authority might publish:
{
"comercialName": "BANK_X_TPP_AISP",
"idno": "1234567890123",
"licenseNumber": "123456_bank_x",
"roles": [
"PISP"
],
"certificate": {
"snCert": "117",
"caCert": "Bank (test)"
}
}
and the Bank's OBP Adapter converts this and returns it to the connector like so:
{
"inboundAdapterCallContext": {
"correlationId": "f347feb7-0c25-4a2f-8a40-d853917d0ccd"
},
"status": {
"errorCode": "",
"backendMessages": []
},
"data": [
{
"entityName": "BANCA COM S.A.",
"entityCode": "198762948",
"attributes": [
{
"attributeType": "STRING",
"name": "CERTIFICATE_SERIAL_NUMBER",
"value": "1082"
},
{
"attributeType": "STRING",
"name": "CERTIFICATE_CA_NAME",
"value": "BANK CA (test)"
}
],
"services": [
{
"roles": [
"PSP_PI",
"PSP_AI"
]
}
]
},
{
"entityName": "Bank Y S.A.",
"entityCode": "1029876963",
"attributes": [
{
"attributeType": "STRING",
"name": "CERTIFICATE_SERIAL_NUMBER",
"value": "1135"
},
{
"attributeType": "STRING",
"name": "CERTIFICATE_CA_NAME",
"value": "BANK CA (test)"
}
],
"services": [
{
"roles": [
"PSP_PI",
"PSP_AI"
]
}
]
}
]
}
Note the use of Regulated Entity Attribute Names to handle different data types from the national authority.
Note: You can / should run a separate instance of OBP for surfacing the Regulated Entities endpoints.
RegulatedEntity.attribute_id
Example value: attrafa-9a0f-4bfa-b30b-9003aa467f51
Description: A string that MUST uniquely identify the Regulated Entity Attribute on this OBP instance.
RegulatedEntity.attribute_name
Example value: Attribute Name
Description: regulatedEntity attribute name
RegulatedEntity.attribute_type
Example value: Attribute Name
Description: regulatedEntity attribute name
RegulatedEntity.attribute_value
Example value: Attribute Name
Description: regulatedEntity attribute name
Roles of Open Bank Project
- CanAddKycCheck
- CanAddKycDocument
- CanAddKycMedia
- CanAddKycStatus
- CanAddSocialMediaHandle
- CanAddUserToGroupAtAllBanks
- CanAddUserToGroupAtOneBank
- CanCheckFundsAvailable
- CanCreateAbacRule
- CanCreateAccount
- CanCreateAccountAttributeAtOneBank
- CanCreateAccountAttributeDefinitionAtOneBank
- CanCreateAccountNotificationWebhookAtOneBank
- CanCreateAnyTransactionRequest
- CanCreateAtm
- CanCreateAtmAtAnyBank
- CanCreateAtmAttribute
- CanCreateAtmAttributeAtAnyBank
- CanCreateAuthenticationTypeValidation
- CanCreateBank
- CanCreateBankAccountBalance
- CanCreateBankAttribute
- CanCreateBankAttributeDefinitionAtOneBank
- CanCreateBankLevelDynamicEndpoint
- CanCreateBankLevelDynamicEntity
- CanCreateBankLevelDynamicMessageDoc
- CanCreateBankLevelDynamicResourceDoc
- CanCreateBankLevelEndpointMapping
- CanCreateBankLevelEndpointTag
- CanCreateBranch
- CanCreateBranchAtAnyBank
- CanCreateCardAttributeDefinitionAtOneBank
- CanCreateCardsForBank
- CanCreateConnectorMethod
- CanCreateConsumer
- CanCreateCounterparty
- CanCreateCounterpartyAtAnyBank
- CanCreateCustomView
- CanCreateCustomer
- CanCreateCustomerAccountLink
- CanCreateCustomerAddress
- CanCreateCustomerAtAnyBank
- CanCreateCustomerAttributeAtAnyBank
- CanCreateCustomerAttributeAtOneBank
- CanCreateCustomerAttributeDefinitionAtOneBank
- CanCreateCustomerMessage
- CanCreateDirectDebitAtOneBank
- CanCreateDynamicEndpoint
- CanCreateDynamicEndpoint_POST_account118
- CanCreateDynamicEntity_D-Entity1
- CanCreateDynamicEntity_InsurancePolicy
- CanCreateDynamicEntity_InsurancePremium
- CanCreateDynamicEntity_MarchHare
- CanCreateDynamicEntity_ObpActivity
- CanCreateDynamicEntity_Odometer
- CanCreateDynamicEntity_SystemCovidAPIDays
- CanCreateDynamicEntity_SystemFishPort
- CanCreateDynamicEntity_SystemFooBar
- CanCreateDynamicEntity_SystemSimonCovid
- CanCreateDynamicEntity_Systemcustomer_cars
- CanCreateDynamicEntity_Systemsustrans
- CanCreateDynamicEntity_Systemtest1
- CanCreateDynamicEntity_Systemtest_daniel707
- CanCreateDynamicMessageDoc
- CanCreateDynamicResourceDoc
- CanCreateEndpointMapping
- CanCreateEntitlementAtAnyBank
- CanCreateEntitlementAtOneBank
- CanCreateFxRate
- CanCreateFxRateAtAnyBank
- CanCreateGroupAtAllBanks
- CanCreateGroupAtOneBank
- CanCreateHistoricalTransaction
- CanCreateHistoricalTransactionAtBank
- CanCreateJsonSchemaValidation
- CanCreateMethodRouting
- CanCreateNonPersonalUserAttribute
- CanCreateProduct
- CanCreateProductAtAnyBank
- CanCreateProductAttribute
- CanCreateProductAttributeDefinitionAtOneBank
- CanCreateProductFee
- CanCreateRateLimits
- CanCreateRegulatedEntity
- CanCreateRegulatedEntityAttribute
- CanCreateResetPasswordUrl
- CanCreateSandbox
- CanCreateScopeAtAnyBank
- CanCreateScopeAtOneBank
- CanCreateSettlementAccountAtOneBank
- CanCreateStandingOrderAtOneBank
- CanCreateSystemAccountNotificationWebhook
- CanCreateSystemLevelDynamicEntity
- CanCreateSystemLevelEndpointTag
- CanCreateSystemView
- CanCreateSystemViewPermission
- CanCreateTaxResidence
- CanCreateTransactionAttributeAtOneBank
- CanCreateTransactionAttributeDefinitionAtOneBank
- CanCreateTransactionRequestAttributeAtOneBank
- CanCreateTransactionRequestAttributeDefinitionAtOneBank
- CanCreateTransactionType
- CanCreateUserAttribute
- CanCreateUserAuthContext
- CanCreateUserAuthContextUpdate
- CanCreateUserCustomerLink
- CanCreateUserCustomerLinkAtAnyBank
- CanCreateUserInvitation
- CanCreateWebUiProps
- CanCreateWebhook
- CanDeleteAbacRule
- CanDeleteAccountAttributeDefinitionAtOneBank
- CanDeleteAccountCascade
- CanDeleteAtm
- CanDeleteAtmAtAnyBank
- CanDeleteAtmAttribute
- CanDeleteAtmAttributeAtAnyBank
- CanDeleteAuthenticationValidation
- CanDeleteBankAccountBalance
- CanDeleteBankAttribute
- CanDeleteBankCascade
- CanDeleteBankLevelDynamicEndpoint
- CanDeleteBankLevelDynamicEntity
- CanDeleteBankLevelDynamicMessageDoc
- CanDeleteBankLevelDynamicResourceDoc
- CanDeleteBankLevelEndpointMapping
- CanDeleteBankLevelEndpointTag
- CanDeleteBranch
- CanDeleteBranchAtAnyBank
- CanDeleteCacheKey
- CanDeleteCacheNamespace
- CanDeleteCardAttributeDefinitionAtOneBank
- CanDeleteCardsForBank
- CanDeleteCascadeSystemDynamicEntity
- CanDeleteCounterparty
- CanDeleteCounterpartyAtAnyBank
- CanDeleteCustomerAccountLink
- CanDeleteCustomerAddress
- CanDeleteCustomerAttributeAtAnyBank
- CanDeleteCustomerAttributeAtOneBank
- CanDeleteCustomerAttributeDefinitionAtOneBank
- CanDeleteCustomerCascade
- CanDeleteDynamicEndpoint
- CanDeleteDynamicEntity_D-Entity1
- CanDeleteDynamicEntity_InsurancePolicy
- CanDeleteDynamicEntity_InsurancePremium
- CanDeleteDynamicEntity_MarchHare
- CanDeleteDynamicEntity_ObpActivity
- CanDeleteDynamicEntity_Odometer
- CanDeleteDynamicEntity_SystemCovidAPIDays
- CanDeleteDynamicEntity_SystemFishPort
- CanDeleteDynamicEntity_SystemFooBar
- CanDeleteDynamicEntity_SystemSimonCovid
- CanDeleteDynamicEntity_Systemcustomer_cars
- CanDeleteDynamicEntity_Systemsustrans
- CanDeleteDynamicEntity_Systemtest1
- CanDeleteDynamicEntity_Systemtest_daniel707
- CanDeleteDynamicMessageDoc
- CanDeleteDynamicResourceDoc
- CanDeleteEndpointMapping
- CanDeleteEntitlementAtAnyBank
- CanDeleteEntitlementAtOneBank
- CanDeleteEntitlementRequestsAtAnyBank
- CanDeleteGroupAtAllBanks
- CanDeleteGroupAtOneBank
- CanDeleteJsonSchemaValidation
- CanDeleteMethodRouting
- CanDeleteNonPersonalUserAttribute
- CanDeleteProductAttribute
- CanDeleteProductAttributeDefinitionAtOneBank
- CanDeleteProductCascade
- CanDeleteProductFee
- CanDeleteRateLimits
- CanDeleteRegulatedEntity
- CanDeleteRegulatedEntityAttribute
- CanDeleteScopeAtAnyBank
- CanDeleteSystemLevelDynamicEntity
- CanDeleteSystemLevelEndpointTag
- CanDeleteSystemView
- CanDeleteSystemViewPermission
- CanDeleteTaxResidence
- CanDeleteTransactionAttributeDefinitionAtOneBank
- CanDeleteTransactionCascade
- CanDeleteTransactionRequestAttributeDefinitionAtOneBank
- CanDeleteUser
- CanDeleteUserAttribute
- CanDeleteUserAuthContext
- CanDeleteUserCustomerLink
- CanDeleteUserCustomerLinkAtAnyBank
- CanDeleteWebUiProps
- CanDisableConsumers
- CanEnableConsumers
- CanExecuteAbacRule
- CanGetAbacRule
- CanGetAccountApplications
- CanGetAccountAttributeDefinitionAtOneBank
- CanGetAccountsHeldAtAnyBank
- CanGetAccountsHeldAtOneBank
- CanGetAccountsMinimalForCustomerAtAnyBank
- CanGetAdapterInfo
- CanGetAdapterInfoAtOneBank
- CanGetAllApiCollections
- CanGetAllBankLevelDynamicResourceDocs
- CanGetAllBankLevelEndpointMappings
- CanGetAllConnectorMethods
- CanGetAllDynamicMessageDocs
- CanGetAllDynamicResourceDocs
- CanGetAllEndpointMappings
- CanGetAnyKycChecks
- CanGetAnyKycDocuments
- CanGetAnyKycMedia
- CanGetAnyKycStatuses
- CanGetAnyUser
- CanGetApiCollectionsForUser
- CanGetAtmAttribute
- CanGetAtmAttributeAtAnyBank
- CanGetAuthenticationTypeValidation
- CanGetBankAttribute
- CanGetBankLevelDynamicEndpoint
- CanGetBankLevelDynamicEndpoints
- CanGetBankLevelDynamicEntities
- CanGetBankLevelDynamicMessageDoc
- CanGetBankLevelDynamicResourceDoc
- CanGetBankLevelEndpointMapping
- CanGetBankLevelEndpointTag
- CanGetCacheConfig
- CanGetCacheInfo
- CanGetCacheNamespaces
- CanGetCallContext
- CanGetCardAttributeDefinitionAtOneBank
- CanGetCardsForBank
- CanGetConfig
- CanGetConnectorEndpoint
- CanGetConnectorMethod
- CanGetConnectorMetrics
- CanGetConsentsAtAnyBank
- CanGetConsentsAtOneBank
- CanGetConsumers
- CanGetCorrelatedUsersInfo
- CanGetCorrelatedUsersInfoAtAnyBank
- CanGetCounterparties
- CanGetCounterpartiesAtAnyBank
- CanGetCounterparty
- CanGetCounterpartyAtAnyBank
- CanGetCurrentConsumer
- CanGetCustomViews
- CanGetCustomerAccountLink
- CanGetCustomerAccountLinks
- CanGetCustomerAddress
- CanGetCustomerAttributeAtAnyBank
- CanGetCustomerAttributeAtOneBank
- CanGetCustomerAttributeDefinitionAtOneBank
- CanGetCustomerAttributesAtAnyBank
- CanGetCustomerAttributesAtOneBank
- CanGetCustomerMessages
- CanGetCustomerOverview
- CanGetCustomerOverviewFlat
- CanGetCustomersAtAllBanks
- CanGetCustomersAtOneBank
- CanGetCustomersMinimalAtAllBanks
- CanGetCustomersMinimalAtOneBank
- CanGetDatabaseInfo
- CanGetDoubleEntryTransactionAtAnyBank
- CanGetDoubleEntryTransactionAtOneBank
- CanGetDynamicEndpoint
- CanGetDynamicEndpoint__account202
- CanGetDynamicEndpoints
- CanGetDynamicEntityDiagnostics
- CanGetDynamicEntityReferenceTypes
- CanGetDynamicEntity_D-Entity1
- CanGetDynamicEntity_InsurancePolicy
- CanGetDynamicEntity_InsurancePremium
- CanGetDynamicEntity_MarchHare
- CanGetDynamicEntity_ObpActivity
- CanGetDynamicEntity_Odometer
- CanGetDynamicEntity_SystemCovidAPIDays
- CanGetDynamicEntity_SystemFishPort
- CanGetDynamicEntity_SystemFooBar
- CanGetDynamicEntity_SystemSimonCovid
- CanGetDynamicEntity_Systemcustomer_cars
- CanGetDynamicEntity_Systemsustrans
- CanGetDynamicEntity_Systemtest1
- CanGetDynamicEntity_Systemtest_daniel707
- CanGetDynamicMessageDoc
- CanGetDynamicResourceDoc
- CanGetEndpointMapping
- CanGetEntitlementRequestsAtAnyBank
- CanGetEntitlementsForAnyBank
- CanGetEntitlementsForAnyUserAtAnyBank
- CanGetEntitlementsForAnyUserAtOneBank
- CanGetEntitlementsForOneBank
- CanGetGroupsAtAllBanks
- CanGetGroupsAtOneBank
- CanGetJsonSchemaValidation
- CanGetMethodRoutings
- CanGetMetricsAtOneBank
- CanGetMigrations
- CanGetNonPersonalUserAttributes
- CanGetProductAttribute
- CanGetProductAttributeDefinitionAtOneBank
- CanGetProductFee
- CanGetProviders
- CanGetRateLimits
- CanGetRegulatedEntityAttribute
- CanGetRegulatedEntityAttributes
- CanGetRolesWithEntitlementCountsAtAllBanks
- CanGetSettlementAccountAtOneBank
- CanGetSocialMediaHandles
- CanGetSystemConnectorMethodNames
- CanGetSystemIntegrity
- CanGetSystemLevelDynamicEntities
- CanGetSystemLevelEndpointTag
- CanGetSystemLogCacheAll
- CanGetSystemLogCacheDebug
- CanGetSystemLogCacheError
- CanGetSystemLogCacheInfo
- CanGetSystemLogCacheTrace
- CanGetSystemLogCacheWarning
- CanGetSystemView
- CanGetSystemViews
- CanGetTaxResidence
- CanGetTransactionAttributeAtOneBank
- CanGetTransactionAttributeDefinitionAtOneBank
- CanGetTransactionAttributesAtOneBank
- CanGetTransactionRequestAtAnyBank
- CanGetTransactionRequestAttributeAtOneBank
- CanGetTransactionRequestAttributeDefinitionAtOneBank
- CanGetTransactionRequestAttributesAtOneBank
- CanGetUserAttributes
- CanGetUserAuthContext
- CanGetUserCustomerLink
- CanGetUserCustomerLinkAtAnyBank
- CanGetUserGroupMembershipsAtAllBanks
- CanGetUserGroupMembershipsAtOneBank
- CanGetUserInvitation
- CanGetUsersWithAttributes
- CanGetViewPermissionsAtAllBanks
- CanGetWebUiProps
- CanGetWebhooks
- CanInvalidateCacheNamespace
- CanLockUser
- CanMaintainProductCollection
- CanReadAggregateMetrics
- CanReadCallLimits
- CanReadDynamicResourceDocsAtOneBank
- CanReadFx
- CanReadGlossary
- CanReadMetrics
- CanReadResourceDoc
- CanReadStaticResourceDoc
- CanReadUserLockedStatus
- CanRefreshUser
- CanRemoveUserFromGroupAtAllBanks
- CanRemoveUserFromGroupAtOneBank
- CanRevokeConsentAtBank
- CanSearchMetrics
- CanSearchWarehouse
- CanSearchWarehouseStatistics
- CanSeeAccountAccessForAnyUser
- CanSyncUser
- CanUnlockUser
- CanUpdateAbacRule
- CanUpdateAccount
- CanUpdateAccountApplications
- CanUpdateAccountAttribute
- CanUpdateAgentStatusAtAnyBank
- CanUpdateAgentStatusAtOneBank
- CanUpdateAtm
- CanUpdateAtmAtAnyBank
- CanUpdateAtmAttribute
- CanUpdateAtmAttributeAtAnyBank
- CanUpdateAuthenticationTypeValidation
- CanUpdateBankAccountBalance
- CanUpdateBankAttribute
- CanUpdateBankLevelDynamicEndpoint
- CanUpdateBankLevelDynamicEntity
- CanUpdateBankLevelDynamicResourceDoc
- CanUpdateBankLevelEndpointMapping
- CanUpdateBankLevelEndpointTag
- CanUpdateBranch
- CanUpdateCardsForBank
- CanUpdateConnectorMethod
- CanUpdateConsentAccountAccessAtAnyBank
- CanUpdateConsentAccountAccessAtOneBank
- CanUpdateConsentStatusAtAnyBank
- CanUpdateConsentStatusAtOneBank
- CanUpdateConsentUserAtAnyBank
- CanUpdateConsentUserAtOneBank
- CanUpdateConsumerCertificate
- CanUpdateConsumerLogoUrl
- CanUpdateConsumerName
- CanUpdateConsumerRedirectUrl
- CanUpdateCustomerAccountLink
- CanUpdateCustomerAttributeAtAnyBank
- CanUpdateCustomerAttributeAtOneBank
- CanUpdateCustomerBranch
- CanUpdateCustomerCreditLimit
- CanUpdateCustomerCreditRatingAndSource
- CanUpdateCustomerCreditRatingAndSourceAtAnyBank
- CanUpdateCustomerData
- CanUpdateCustomerEmail
- CanUpdateCustomerIdentity
- CanUpdateCustomerMobilePhoneNumber
- CanUpdateCustomerNumber
- CanUpdateDynamicEndpoint
- CanUpdateDynamicEntity_D-Entity1
- CanUpdateDynamicEntity_InsurancePolicy
- CanUpdateDynamicEntity_InsurancePremium
- CanUpdateDynamicEntity_MarchHare
- CanUpdateDynamicEntity_ObpActivity
- CanUpdateDynamicEntity_Odometer
- CanUpdateDynamicEntity_SystemCovidAPIDays
- CanUpdateDynamicEntity_SystemFishPort
- CanUpdateDynamicEntity_SystemFooBar
- CanUpdateDynamicEntity_SystemSimonCovid
- CanUpdateDynamicEntity_Systemcustomer_cars
- CanUpdateDynamicEntity_Systemsustrans
- CanUpdateDynamicEntity_Systemtest1
- CanUpdateDynamicEntity_Systemtest_daniel707
- CanUpdateDynamicMessageDoc
- CanUpdateDynamicResourceDoc
- CanUpdateEndpointMapping
- CanUpdateGroupAtAllBanks
- CanUpdateGroupAtOneBank
- CanUpdateJsonSchemaValidation
- CanUpdateMethodRouting
- CanUpdateProductAttribute
- CanUpdateProductFee
- CanUpdateRateLimits
- CanUpdateRegulatedEntityAttribute
- CanUpdateSystemLevelDynamicEntity
- CanUpdateSystemLevelEndpointTag
- CanUpdateSystemView
- CanUpdateTransactionAttributeAtOneBank
- CanUpdateTransactionRequestAttributeAtOneBank
- CanUpdateTransactionRequestStatusAtAnyBank
- CanUpdateUserAttribute
- CanUpdateWebhook
- CanUseAccountFirehose
- CanUseAccountFirehoseAtAnyBank
- CanUseCustomerFirehoseAtAnyBank
- CanValidateUser
Run via IntelliJ IDEA
To run via IntelliJ IDEA
-
Make sure that Redis is running and properly configured if redis is not running without password protection on default port at localhost
-
Make sure you have the IntelliJ Scala plugin installed.
-
Create a new folder e.g. OpenBankProject and cd there
-
In IntelliJ IDEA do File -> New -> Project from existing sources, navigate to the folder and IMPORTANTLY select pom.xml
-
Alternatively you can do File -> New -> Project from VCS and checkout the project directly from github.
-
When / if prompted for SDK, choose Java 11 (and Scala 2.12) otherwise keep the defaults. Use the Maven options. Do not change the project name etc.
-
If you see a message about an unmanaged pom.xml, click the option to let Maven manage it.
-
Navigate to obp-api/test/scala/code/RunWebApp. You may see a Setup Scala SDK link. Click this and check Scala 2.12.12 or so.
-
In obp-api/src/main/resources/props create a <yourloginname>.props (or default.props) for development. Set connector=mapped
-
Now Rebuild the project so everything is compiled. At this point you may need to select the SDK, see above.
-
Once you have rebuilt the project without compile errors, you should be able to RunWebApp/RunTLSWebApp/RunMTLSWebApp in obp-api/src/test/scala
-
If you have trouble (re)building, try using the IntelliJ IDEA terminal: mvn clean test-compile
To run via IntelliJ IDEA in development mode without secure connection
-
Run RunWebApp by right clicking on it or selecting Run. The built in jetty server should start on localhost:8080
-
Browse to http://localhost:8080 but don't try anything else there yet.
To run via IntelliJ IDEA in TLS development mode (secure connection)
-
Run RunTLSWebApp by right clicking on it and selecting Run/Debug. The built in jetty server should start on localhost:8080
-
Browse to https://localhost:8080 but don't try anything else there yet
In development mode we use this option in order to try OpenID Connect functionality. I.e. redirect URI must be https one.
To run via IntelliJ IDEA in MTLS development mode (secure connection)
-
Run RunMTLSWebApp by right clicking on it and selecting Run/Debug. The built in jetty server should start on localhost:8080
-
Import certificate obp-api/src/test/resources/cert/localhost_SAN_dns_ip.pfx into your browser.
-
Browse to https://localhost:8080 but don't try anything else there yet
In development mode we use this option in order to try UK Open Banking APIs functionality where mutual TLS is part of that standard.
SCA (Strong Customer Authentication)
SCA is the process by which a Customer of the Bank securely identifies him/her self to the Bank.
Generally this involves using an Out Of Band (OOB) form of communication e.g. a One Time Password (OTP) / code sent to a mobile phone.
In the OBP APIs, SCA is invoked during Transaction Requests and Consent creation.
See the following endpoints:
Create Consent via SMS
Create Consent via Email (for testing purposes)
Answer Consent Challenge
Create Transaction Request
Answer Transaction Request Challenge
Possible SCA flows:

Scenario 1: Onboarding a User
1) Create a user
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/users
Body:
{ "email":"ellie@example.com", "username":"ellie", "password":"P@55w0RD123", "first_name":"Ellie", "last_name":"Williams"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
Please note the user_id
2) Create customer
Requires CanCreateCustomer and CanCreateUserCustomerLink roles
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/customers
Body:
{ "legal_name":"Eveline Tripman", "mobile_phone_number":"+44 07972 444 876", "email":"eveline@example.com", "face_image":{ "url":"www.openbankproject", "date":"1100-01-01T00:00:00Z" }, "date_of_birth":"1100-01-01T00:00:00Z", "relationship_status":"single", "dependants":10, "dob_of_dependants":["1100-01-01T00:00:00Z"], "credit_rating":{ "rating":"OBP", "source":"OBP" }, "credit_limit":{ "currency":"EUR", "amount":"10" }, "highest_education_attained":"Master", "employment_status":"worker", "kyc_status":true, "last_ok_date":"1100-01-01T00:00:00Z", "title":"Dr.", "branch_id":"DERBY6", "name_suffix":"Sr"}
Headers:
Content-Type: application/json
Authorization: directlogin token="your-token-from-direct-login"
3) List customers for the user
Action:
GET https://apisandbox.openbankproject.com/obp/v4.0.0/users/current/customers
Body:
Leave empty!
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
4) Create user customer link
Requires CanCreateCustomer and CanCreateUserCustomerLink roles
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/user_customer_links
Body:
{ "user_customer_link_id":"String", "customer_id":"customer-id-from-step-2", "user_id":"user-id-from-step-1", "date_inserted":"2018-03-22T00:08:00Z", "is_active":true }
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
5) Create account
Requires CanCreateAccount role
Action:
PUT https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/ACCOUNT_ID
Body:
{ "user_id":"userid-from-step-1", "label":"My Account", "product_code":"AC", "balance":{ "currency":"EUR", "amount":"10" }, "branch_id":"DERBY6", "account_routing":{ "scheme":"AccountNumber", "address":"4930396" }, "account_attributes":[{ "product_code":"saving1", "account_attribute_id":"613c83ea-80f9-4560-8404-b9cd4ec42a7f", "name":"OVERDRAFT_START_DATE", "type":"DATE_WITH_DAY", "value":"2012-04-23" }]}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
6) List accounts
Action:
GET https://apisandbox.openbankproject.com/obp/v4.0.0/my/banks/BANK_ID/accounts/account-id-from-step-5/account
Body:
Leave empty!
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
7) Create card
Requires CanCreateCardsForBank role
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/management/banks/BANK_ID/cards
Body:
{ "card_number":"364435172576215", "card_type":"Credit", "name_on_card":"SusanSmith", "issue_number":"1", "serial_number":"1324234", "valid_from_date":"2017-09-19T00:00:00Z", "expires_date":"2017-09-19T00:00:00Z", "enabled":true, "technology":"technology1", "networks":["network1","network2"], "allows":["credit","debit"], "account_id":"account_id from step 5", "replacement":{ "requested_date":"2017-09-19T00:00:00Z", "reason_requested":"RENEW" }, "pin_reset":[{ "requested_date":"2017-09-19T00:00:00Z", "reason_requested":"FORGOT" },{ "requested_date":"2020-01-18T16:39:23Z", "reason_requested":"GOOD_SECURITY_PRACTICE" }], "collected":"2017-09-19T00:00:00Z", "posted":"2017-09-19T00:00:00Z", "customer_id":"customer_id from step 2"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct0login"
8) List cards
Action:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/cards
Body:
Leave empty!
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct0login"
Scenario 2: Create a Public Account
1) Create account
Create an account as described in Step 5 of section Onboarding a user
2) Create a view
Action:
POST https://apisandbox.openbankproject.com/obp/v3.0.0/banks/BANK_ID/accounts/your-account-id-from-step-1/views
Body:
{ "name":"_test", "description":"This view is for family", "metadata_view":"_test", "is_public":true, "which_alias_to_use":"family", "hide_metadata_if_alias_used":false, "allowed_actions":[can_see_transaction_this_bank_account,can_see_transaction_other_bank_account,can_see_transaction_metadata,,can_see_transaction_amount,can_see_transaction_type,can_see_transaction_currency,can_see_transaction_start_date,can_see_transaction_finish_date,can_see_transaction_balance,can_see_comments,can_see_tags,can_see_images,can_see_bank_account_owners,can_see_bank_account_type,can_see_bank_account_balance,can_see_bank_account_currency,can_see_bank_account_label,can_see_bank_account_national_identifier,can_see_bank_account_swift_bic,can_see_bank_account_iban,can_see_bank_account_number,can_see_bank_account_bank_name,can_see_other_account_national_identifier,can_see_other_account_swift_bic,can_see_other_account_iban,can_see_other_account_bank_name,can_see_other_account_number,can_see_other_account_metadata,can_see_other_account_kind,can_see_more_info,can_see_url,can_see_image_url,can_see_open_corporates_url,can_see_corporate_location,can_see_physical_location,can_see_public_alias,can_see_private_alias,can_add_more_info,can_add_url,can_add_image_url,can_add_open_corporates_url,can_add_corporate_location,can_add_physical_location,can_add_public_alias,can_add_private_alias,can_delete_corporate_location,can_delete_physical_location,can_add_comment,can_delete_comment,can_add_tag,can_delete_tag,can_add_image,can_delete_image,can_add_where_tag,can_see_where_tag,can_delete_where_tag,can_see_bank_routing_scheme,can_see_bank_routing_address,can_see_bank_account_routing_scheme,can_see_bank_account_routing_address,can_see_other_bank_routing_scheme,can_see_other_bank_routing_address,can_see_other_account_routing_scheme,can_see_other_account_routing_address,can_query_available_funds,can_add_transaction_request_to_own_account,can_add_transaction_request_to_any_account,can_see_bank_account_credit_limit,can_create_direct_debit,can_create_standing_order]} |
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
3) Grant user access to view
Action:
POST https://apisandbox.openbankproject.com/obp/v3.0.0/banks/BANK_ID/accounts/your-account-id-from-step-1/permissions/PROVIDER/PROVIDER_ID/views/view-id-from-step-2
Body:
{ "json_string":"{}"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
Scenario 3: Create counterparty and make payment
1) Create counterparty
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/account-id-from-account-creation/VIEW_ID/counterparties
Body:
{ "name":"CounterpartyName", "description":"My landlord", "other_account_routing_scheme":"accountNumber", "other_account_routing_address":"7987987-2348987-234234", "other_account_secondary_routing_scheme":"IBAN", "other_account_secondary_routing_address":"DE89370400440532013000", "other_bank_routing_scheme":"bankCode", "other_bank_routing_address":"10", "other_branch_routing_scheme":"branchNumber", "other_branch_routing_address":"10010", "is_beneficiary":true, "bespoke":[{ "key":"englishName", "value":"english Name" }]} |
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
2) Make payment by SEPA
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/ACCOUNT_ID/VIEW_ID/transaction-request-types/SEPA/transaction-requests
Body:
{ "value":{ "currency":"EUR", "amount":"10" }, "to":{ "iban":"123" }, "description":"This is a SEPA Transaction Request", "charge_policy":"SHARED"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token" |
3) Make payment by COUNTERPARTY
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/ACCOUNT_ID/VIEW_ID/transaction-request-types/COUNTERPARTY/transaction-requests
Body:
{ "to":{ "counterparty_id":"counterparty-id-from-step-1" }, "value":{ "currency":"EUR", "amount":"10" }, "description":"A description for the transaction to the counterparty", "charge_policy":"SHARED"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
Scenario 4: Grant account access to another User
1) Create account
Create an account as described in Step 5 of section Onboarding a user
2) Create a view (private)
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/your-account-id-from-step-1/views
Body:
{ "name":"_test", "description":"good", "is_public":false, "which_alias_to_use":"accountant", "hide_metadata_if_alias_used":false, "allowed_actions": [can_see_transaction_this_bank_account,can_see_transaction_other_bank_account,can_see_transaction_metadata,,can_see_transaction_amount,can_see_transaction_type,can_see_transaction_currency,can_see_transaction_start_date,can_see_transaction_finish_date,can_see_transaction_balance,can_see_comments,can_see_tags,can_see_images,can_see_bank_account_owners,can_see_bank_account_type,can_see_bank_account_balance,can_see_bank_account_currency,can_see_bank_account_label,can_see_bank_account_national_identifier,can_see_bank_account_swift_bic,can_see_bank_account_iban,can_see_bank_account_number,can_see_bank_account_bank_name,can_see_other_account_national_identifier,can_see_other_account_swift_bic,can_see_other_account_iban,can_see_other_account_bank_name,can_see_other_account_number,can_see_other_account_metadata,can_see_other_account_kind,can_see_more_info,can_see_url,can_see_image_url,can_see_open_corporates_url,can_see_corporate_location,can_see_physical_location,can_see_public_alias,can_see_private_alias,can_add_more_info,can_add_url,can_add_image_url,can_add_open_corporates_url,can_add_corporate_location,can_add_physical_location,can_add_public_alias,can_add_private_alias,can_delete_corporate_location,can_delete_physical_location,can_add_comment,can_delete_comment,can_add_tag,can_delete_tag,can_add_image,can_delete_image,can_add_where_tag,can_see_where_tag,can_delete_where_tag,can_see_bank_routing_scheme,can_see_bank_routing_address,can_see_bank_account_routing_scheme,can_see_bank_account_routing_address,can_see_other_bank_routing_scheme,can_see_other_bank_routing_address,can_see_other_account_routing_scheme,can_see_other_account_routing_address,can_query_available_funds,can_add_transaction_request_to_own_account,can_add_transaction_request_to_any_account,can_see_bank_account_credit_limit,can_create_direct_debit,can_create_standing_order]}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
3) Get User (Current)
Action:
GET https://apisandbox.openbankproject.com/obp/v4.0.0/users/current
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
4) Grant user access to himself
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/your-account-id-from-step-1/account-access/grant
Body:
{ "user_id":"your-user-id-from-step3", "view":{ "view_id":"_test", "is_system":false }}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
5) Grant user access to view to another user
Action:
POST https://apisandbox.openbankproject.com/obp/v4.0.0/banks/BANK_ID/accounts/your-account-id-from-step-1/account-access/grant
Body:
{ "user_id":"another-user-id", "view":{ "view_id":"_test", "is_system":false }}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token"
Scenario 5: Onboarding a User using Auth Context
1) Create a user
Action:
POST https://apisandbox.openbankproject.com/obp/v3.0.0/users
Body:
{ "email":"ellie@example.com", "username":"ellie", "password":"P@55w0RD123", "first_name":"Ellie", "last_name":"Williams"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
Please note the user_id
2) Create User Auth Context
These key value pairs will be propagated over connector to adapter and to bank. So the bank can use these key value paris
to map obp user to real bank customer.
Action:
POST https://apisandbox.openbankproject.com/obp/obp/v4.0.0/users/USER_ID/auth-context
Body:
{ "key":"CUSTOMER_NUMBER", "value":"78987432"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
3) Create customer
Requires CanCreateCustomer or canCreateCustomerAtAnyBank roles
Action:
POST https://apisandbox.openbankproject.com/obp/v3.1.0/banks/BANK_ID/customers
Body:
{ "user_id":"user-id-from-step-1", "customer_number":"687687678", "legal_name":"NONE", "mobile_phone_number":"+44 07972 444 876", "email":"person@example.com", "face_image":{ "url":"www.openbankproject", "date":"2013-01-22T00:08:00Z" }, "date_of_birth":"2013-01-22T00:08:00Z", "relationship_status":"Single", "dependants":5, "dob_of_dependants":["2013-01-22T00:08:00Z"], "credit_rating":{ "rating":"OBP", "source":"OBP" }, "credit_limit":{ "currency":"EUR", "amount":"10" }, "highest_education_attained":"Bachelor’s Degree", "employment_status":"Employed", "kyc_status":true, "last_ok_date":"2013-01-22T00:08:00Z"}
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
4) Get Customers for Current User
Action:
GET https://apisandbox.openbankproject.com/obp/v3.0.0/users/current/customers
Body:
Leave empty!
Headers:
Content-Type: application/json
Authorization: DirectLogin token="your-token-from-direct-login"
Scenario 6: Update credit score based on transaction and device data.
1) Use Case
As an App developer you want to give a Credit Rating to a Customer based on their Transactions and also device data.
2) Solution Overview:
In general your application will need to:
1) Loop through Customers
2) For each Customer, get its related Users and associated device data
3) For each Customer or User get the related accounts
4) For each Account, get its Transaction data
5) Update the Credit Rating and Credit Rating Readiness score of the Customer.
3) Authentication and Authorisation
Depending on the configuration of this OBP instance, and the endpoints being called, the Consumer / Client may need Scopes and / or the User may need Entitlements and Account Access.
To get started, we suggest requesting Entitlements via the API Explorer.
4) Endpoints
- Get Customers (minimal). Click here for documentation.
The above endpoints return a list of bank_id and customer_id which can be used for getting correlated Users and their attributes:
- Get Correlated Users for a Customer. Click here for documentation.
Then get Accounts related to a Customer:
- GET Accounts Minimal for a Customer. Click here for documentation.
Once you have the list of bank_ids and account_ids, you can get their transactions which include tags for each transaction:
- GET Firehose Transactions. Click here for documentation.
After your processing of the data you can update the Credit Score:
- Update Credit Score. Click here for documentation.
You can create a CREDIT_SCORE_READINESS attribute using the following endpoint:
- Create Customer Attribute. Click here for documentation.
And update it here:
- Update Customer Attribute. Click here for documentation.
Scenario 7: Onboarding a User with multiple User Auth Context records
1) Assuming a User is registered.
The User can authenticate using OAuth, OIDC, Direct Login etc.
2) Create a first User Auth Context record e.g. ACCOUNT_NUMBER
The setting of the first User Auth Context record for a User, typically involves sending an SMS to the User.
The phone number used for the SMS is retrieved from the bank's Core Banking System via an Account Number to Phone Number lookup.
If this step succeeds we can be reasonably confident that the User who initiated it has access to a SIM card that can use the Phone Number linked to the Bank Account on the Core Banking System.
Action: Create User Auth Context Update Request
POST https://apisandbox.openbankproject.com/obp/obp/v5.0.0/banks/BANK_ID/users/current/auth-context-updates/SMS
Body:
{ "key":"ACCOUNT_NUMBER", "value":"78987432"}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"
When customer get the the challenge answer from SMS, then need to call Answer Auth Context Update Challenge to varify the challenge.
Then the customer create the 1st User Auth Context successfully.
Action: Answer Auth Context Update Challenge
POST https://apisandbox.openbankproject.com/obp/obp/v5.0.0/banks/BANK_ID/users/current/auth-context-updates/AUTH_CONTEXT_UPDATE_ID/challenge
Body:
{ "answer": "12345678"}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"
3) Create a second User Auth Context record e.g. SMALL_PAYMENT_VERIFIED
Once the first User Auth Context record is set, we can require the App to set a second record which builds on the information of the first.
Action: Create User Auth Context Update Request
POST https://apisandbox.openbankproject.com/obp/obp/v5.0.0/banks/BANK_ID/users/current/auth-context-updates/SMS
Body:
{ "key":"SMALL_PAYMENT_VERIFIED", "value":"78987432"}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"
Following Create User Auth Context Update Request request the API will send a small payment with a random code from the Users bank account specified in the SMALL_PAYMENT_VERIFIED key value.
In order to answer the challenge, the User must have access to the online banking statement (or some other App that already can read transactions in realtime) so they can read the code in the description of the payment.
Then Action:Answer Auth Context Update Challenge
POST https://apisandbox.openbankproject.com/obp/obp/v5.0.0/banks/BANK_ID/users/current/auth-context-updates/AUTH_CONTEXT_UPDATE_ID/challenge
Body:
{ "answer": "12345678"}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"
Note! The above logic must be encoded in a dynamic connector method for the OBP internal function validateUserAuthContextUpdateRequest which is used by the endpoint Create User Auth Context Update Request See the next step.
4) Create or Update Connector Method for validateUserAuthContextUpdateRequest
Using this endpoint you can modify the Scala logic
Action:
POST https://apisandbox.openbankproject.com/obp/obp/v4.0.0/management/connector-methods
Body:
{ "method_name":"validateUserAuthContextUpdateRequest", "method_body":"%20%20%20%20%20%20Future.successful%28%0A%20%20%20%20%20%20%20%20Full%28%28BankCommons%28%0A%20%20%20%20%20%20%20%20%20%20BankId%28%22Hello%20bank%20id%22%29%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%221%22%2C%0A%20%20%20%20%20%20%20%20%20%20%228%22%0A%20%20%20%20%20%20%20%20%29%2C%20None%29%29%0A%20%20%20%20%20%20%29"}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"
5) Allow automated access to the App with Create Consent (SMS)
Following the creation of User Auth Context records, OBP will create the relevant Account Access Views which allows the User to access their account(s).
The App can then request an OBP consent which can be used as a bearer token and have automated access to the accounts.
The Consent can be deleted at any time by the User.
The Consent can have access to everything the User has access to, or a subset of this.
Action:
POST https://apisandbox.openbankproject.com/obp/obp/v4.0.0/banks/BANK_ID/my/consents/SMS
Body:
{ "everything":false, "views":[{ "bank_id":"gh.29.uk", "account_id":"8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0", "view_id":owner], "entitlements":[{ "bank_id":"gh.29.uk", "role_name":"CanGetCustomersAtOneBank" }], "consumer_id":"7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh", "phone_number":"+44 07972 444 876", "valid_from":"2022-04-29T10:40:03Z", "time_to_live":3600}
Headers:
Content-Type: application/json
directlogin: token="your-token-from-direct-login"

Space
In OBP, if you have access to a "Space", you have access to a set of Dynamic Endpoints and Dynamic Entities that belong to that Space.
Internally, Spaces are defined as a "Banks" thus Spaces are synonymous with OBP Banks.
A user can have access to several spaces. The API Explorer shows these under the Spaces menu.
In order to see the documentation for the Dynamic Endpoints and Dynamic Entities, a user may need to have access to the CanReadDynamicResourceDocsAtOneBank Role.
You can create your own Space by creating an OBP Bank.
Static Endpoint
Static endpoints are served from static Scala source code which is contained in (public) Git repositories.
Static endpoints cover all the OBP API and User management functionality as well as the Open Bank Project banking APIs and other Open Banking standards such as UK Open Banking, Berlin Group and STET etc..
In short, Static (standard) endpoints are defined in Git as Scala source code, where as Dynamic (custom) endpoints are defined in the OBP database.
Modifications to Static endpoint core properties such as URLs and response bodies require source code changes and an instance restart. However, JSON Schema Validation and Dynamic Connector changes can be applied in real-time.
TPP
(TPP) Third Party Providers are authorised/registered organisations or natural persons that use APIs developed to Standards to access customer’s accounts, in order to provide account information services and/or to initiate payments.
Third Party Providers are either/both Payment Initiation Service Providers (PISPs) and/or Account Information Service Providers (AISPs).
TPP Certificate Verification
TPP Certificate Verification
The signing and verification flow of certificates for TPP requests is a follows:
Generation of the Request by TPP
Step 1: Calculating the Hash for the Digest Field
- TPP creates the body of the request (e.g., JSON containing transaction or consent data).
- TPP applies the SHA-256 algorithm to the body of the request to generate a unique hash.
- The resulting hash is encoded in Base64 and placed in the request header under the
Digestfield.
Step 2: Creating the Signing String
- TPP prepares a signing string based on specific fields from the request header.
- The signing string is a concatenation of the values of the signed fields in a specific format.
- The order of the fields is critical and follows the specifications.
Step 3: Signing the Signing String
- TPP uses its RSA private key associated with its certificate to generate a digital signature.
- The signature is applied to the signing string using the RSA-SHA256 algorithm.
- The resulting digital signature is Base64-encoded and placed in the
Signaturefield.
Step 4: Adding the Certificate to the TPP-Signature-Certificate Field
- TPP includes its public certificate in the request header under the
TPP-Signature-Certificatefield. - The certificate is issued by a trusted certification authority (CA) and contains the TPP's public key.
Step 5: Sending the Request to OBP
- TPP sends the complete request, including the
Digest,Signature, andTPP-Signature-Certificateheaders, to the OBP endpoint.
Verification of the Request by OBP
Step 1: Validating the TPP Certificate
- OBP verifies the TPP certificate included in the
TPP-Signature-Certificatefield.
Steps:
- Verify the certificate's trust chain up to a trusted certification authority.
- Ensure the certificate is valid (not expired or revoked).
- Confirm the certificate is issued for the appropriate usage (e.g., digital signatures for Open Banking), based on the information from the National Bank registry (e.g., certificate SN and CA found in the
Signaturefield).
- Result: If the certificate is valid, the TPP's identity is confirmed.
Step 2: Verifying the Signature in the Signature Field
- OBP extracts the fields included in the signing string based on the information in the
Signaturefield. - OBP recreates the signing string in the same format used by the TPP.
- OBP uses the public key from the certificate in the
TPP-Signature-Certificatefield to verify the signature in theSignaturefield. - Result: If the signature is valid, the authenticity of the request is confirmed.
Step 3: Verifying the Hash in the Digest Field
- OBP computes its own SHA-256 hash of the received request body.
- The computed hash is compared with the value in the
Digestheader. - Result: If the two hashes match, the integrity of the request body is confirmed.
Step 4: Authorizing the Request
- If all verifications (integrity, signature, and certificate) pass, OBP processes the request.
- Otherwise, the request is rejected with an error message (e.g.,
401 Unauthorizedor403 Forbidden).
Additional Details
How does OBP verify the signature in the Signature field?
- Extracts the public key from the
TPP-Signature-Certificate:
- OBP retrieves the certificate (
TPP-Signature-Certificate) from the request header. - From this certificate, OBP extracts the TPP's public key.
- Recreates the Signing String:
- OBP analyzes the
Signatureheader to identify the signed fields (e.g.,Digest,X-Request-ID,Date, etc.). - OBP recreates the signing string from the actual values of these fields in the specified order.
- Decodes the Signature:
- OBP decodes the value in the
Signature.signaturefield (the digital signature generated by TPP). - Decoding is done using the public key extracted from the
TPP-Signature-Certificateand the algorithm specified inSignature.algorithm(e.g., RSA-SHA256).
- Compares the Resulting Hash:
- During decoding, OBP obtains a hash calculated by TPP at the time of signing.
- OBP compares this hash with the hash generated internally from the recreated signing string.
- Possible Outcomes:
- If the hashes match, the signature is valid.
- If the hashes do not match, the signature is invalid, and the request is rejected.
Transaction
Transactions are records of successful movements of value into or out of an Account.
OBP Transactions don't contain any "draft" or "pending" Transactions; pending transactions see represented by Transaction Requests.
OBP Transactions are modelled on a Bank statement where everything is based on the perspective of my account.
That is, if I look at "my account", I see credits (positive numbers) and debits (negative numbers)
An OBP transaction stores information including the:
Bank ID
Account ID
Currency
Amount (positive for a credit, negative for a debit)
Date
Counterparty (information that describes the other party in the transaction)
- optionally description and new balance.
Note, OBP operates a Double-Entry Bookkeeping system which means that every transfer of value within OBP is represented by two transactions.
For instance, to represent 5 Euros going from Account A to Account B, we would have 2 transactions:
Transaction 1.
Account: A
Currency: EUR
Amount: -5
CounterpartyCounterpartyCounterparty: Account B
Transaction 2.
Account: B
Currency: EUR
Amount: +5
Counterparty: Account A
The sum of the two transactions must be zero.
What about representing value coming into or out of the system? Here we use "settlement accounts":
OBP-INCOMING-SETTLEMENT-ACCOUNT is typically the ID for a default incoming settlement account
OBP-OUTGOING-SETTLEMENT-ACCOUNT is typically the ID for a default outgoing settlement account
See the following diagram:

See the Get Double Entry Transaction endpoint
Transaction Requests
Transaction Requests are records of transaction / payment requests coming to the API. They may or may not result in Transactions (following authorisation, security challenges and sufficient funds etc.)
A successful Transaction Request results in a Transaction.
For more information see here
Transaction Requests.Transaction Request Refund Reason Code
Example value: CUST
Description: Defines the reason code of a transaction refund request (e.g. a SEPA Credit Transfer Scheme reason code).
Transaction Requests.Transaction Request Type
Example value: SEPA
Description: The Transaction Request Type defines the request body that is required - and the logic / flow of the Transaction Request. Allowed values include SEPA, COUNTERPARTY and SANDBOX_TAN.
Transaction Requests.attributeId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: Transaction Request attribute id
Transaction Requests.attributeName
Example value: HOUSE_RENT
Description: Transaction Request attribute name
Transaction Requests.attributeType
Example value: STRING
Description: Transaction Request attribute type.
Transaction Requests.attributeValue
Example value: 123456789
Description: Transaction Request attribute value.
Transaction Requests.id
Example value: 8138a7e4-6d02-40e3-a129-0b2bf89de9f1
Description: The Transaction Request Id
Transaction request challenge threshold
Is an example of "Adaptive authentication" where, in a dynamic way, we get challenge threshold via CBS depending on a user's risk profile.
It implies that in a case of risky transaction request, over a certain amount, a user is prompted to answer the challenge.
Transaction-Request-Introduction
In OBP we initiate a Payment by creating a Transaction Request.
An OBP transaction request may or may not result in a transaction. However, a transaction only has one possible state: completed.
A Transaction Request can have one of several states: INITIATED, NEXT_CHALLENGE_PENDING etc.
Transactions are modeled on items in a bank statement that represent the movement of money.
Transaction Requests are requests to move money which may or may not succeed and thus result in a Transaction.
A Transaction Request might create a security challenge that needs to be answered before the Transaction Request proceeds.
In case 1 person needs to answer security challenge we have next flow of state of an transaction request:
INITIATED => COMPLETED
In case n persons needs to answer security challenge we have next flow of state of an transaction request:
INITIATED => NEXT_CHALLENGE_PENDING => ... => NEXT_CHALLENGE_PENDING => COMPLETED
The security challenge is bound to a user i.e. in case of right answer and the user is different than expected one the challenge will fail.
Rule for calculating number of security challenges:
If product Account attribute REQUIRED_CHALLENGE_ANSWERS=N then create N challenges
(one for every user that has a View where permission can_add_transaction_request_to_any_account=true)
In case REQUIRED_CHALLENGE_ANSWERS is not defined as an account attribute default value is 1.
Transaction Requests contain charge information giving the client the opportunity to proceed or not (as long as the challenge level is appropriate).
Transaction Requests can have one of several Transaction Request Types which expect different bodies. The escaped body is returned in the details key of the GET response.
This provides some commonality and one URL for many different payment or transfer types with enough flexibility to validate them differently.
The payer is set in the URL. Money comes out of the BANK_ID and ACCOUNT_ID specified in the URL.
In sandbox mode, TRANSACTION_REQUEST_TYPE is commonly set to ACCOUNT. See getTransactionRequestTypesSupportedByBank for all supported types.
In sandbox mode, if the amount is less than 1000 EUR (any currency, unless it is set differently on this server), the transaction request will create a transaction without a challenge, else the Transaction Request will be set to INITIALISED and a challenge will need to be answered.
If a challenge is created you must answer it using Answer Transaction Request Challenge before the Transaction is created.
You can transfer between different currency accounts. (new in 2.0.0). The currency in body must match the sending account.
For exchange rates in this sandbox see here: here
Transaction Requests satisfy PSD2 requirements thus:
1) A transaction can be initiated by a third party application.
2) The customer is informed of the charge that will incurred.
3) The call supports delegated authentication (OAuth)
See this python code for a complete example of this flow.
There is further documentation here
Transaction.attributeId
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: Transaction attribute id
Transaction.charge_policy
Example value: SHARED
Description: The transaction fee charge policy, can be shared, debit account or credit account.
Transaction.transactionDescription
Example value: The piano lession-Invoice No:68
Description: A description or reference for the transaction
Transaction.transactionId
Example value: 2fg8a7e4-6d02-40e3-a129-0b2bf89de8ub
Description: The Transaction ID used in URLs. Used to store Metadata for the Transaction.
User
The entity that accesses the API with a login / authorisation token and has access to zero or more resources on the OBP API. The User is linked to the core banking user / customer at the South Side Adapter layer.
User Customer Links
Link Users and Customers in a many to many relationship. A User can represent many Customers (e.g. the bank may have several Customer records for the same individual or a dependant). In this way Customers can easily be attached / detached from Users.
User.provider_id
The id of the user given by the authentication provider. This is UNIQUE in combination with PROVIDER name.
User.userId
Example value: 9ca9a7e4-6d02-40e3-a129-0b2bf89de9b1
Description: A string that MUST uniquely identify the user on this OBP instance.
User.userNameExample
Example value: felixsmith
Description: The userName the user uses to authenticate.
User.user_id
An identifier that MUST NOT leak the user name or other identifier nomrally used by the customer or bank staff. It SHOULD be a UUID and MUST be unique on the OBP instance.
Example value: 9ca9a7e4-6d02-40e3-a129-0b2bf89de9b1
atm_id
Example value: atme-9a0f-4bfa-b30b-9003aa467f51
Description: A string that MUST uniquely identify the ATM on this OBP instance.
attributes
Example value: attribute value in form of (name, value)
Description: no-description-provided
balance_id
Example value: 7uy8a7e4-6d02-40e3-a129-0b2bf89de8uh
Description: A string that MUST uniquely identify the Account Balance on this OBP instance, can be used in all cache.
bank_routings
Example value: bank routing in form of (scheme, address)
Description: no-description-provided
can_add_transaction_request_to_own_account
Example value: false
Description: no-description-provided
certificate_authority_ca_owner_id
Example value: CY_CBC
Description: The certificate authority owner ID.
consent_request_id
Example value: 8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0
Description: A string that MUST uniquely identify the Consent Request on this OBP instance.
counterparty_limit_id
Example value: abc9a7e4-6d02-40e3-a129-0b2bf89de9b1
Description: A string that MUST uniquely identify the Counterparty Limit on this OBP instance.
description
Example value: Description of the object. Maximum length is 2000. It can be any characters here.
Description: The human readable description here.
duration
Example value: 5.123
Description: This is a decimal number in seconds, eg: 1 for 1 second, 0.001 for 1 ms
entity_address
Example value: EXAMPLE COMPANY LTD, 5 SOME STREET
Description: The address of the entity.
entity_certificate_public_key
Example value: MIICsjCCAZqgAwIBAgIGAYwQ62R0MA0GCSqGSIb3DQEBCwUAMBoxGDAWBgNVBAMMD2FwcC5leGFtcGxlLmNvbTAeFw0yMzExMjcxMzE1MTFaFw0yNTExMjYxMzE1MTFaMBoxGDAWBgNVBAMMD2FwcC5leGFtcGxlLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAK9WIodZHWzKyCcf9YfWEhPURbfO6zKuMqzHN27GdqHsVVEGxP4F/J4mso+0ENcRr6ur4u81iREaVdCc40rHDHVJNEtniD8Icbz7tcsqAewIVhc/q6WXGqImJpCq7hA0m247dDsaZT0lb/MVBiMoJxDEmAE/GYYnWTEn84R35WhJsMvuQ7QmLvNg6RkChY6POCT/YKe9NKwa1NqI1U+oA5RFzAaFtytvZCE3jtp+aR0brL7qaGfgxm6B7dEpGyhg0NcVCV7xMQNq2JxZTVdAr6lcsRGaAFulakmW3aNnmK+L35Wu8uW+OxNxwUuC6f3b4FVBa276FMuUTRfu7gc+k6kCAwEAATANBgkqhkiG9w0BAQsFAAOCAQEAAU5CjEyAoyTn7PgFpQD48ZNPuUsEQ19gzYgJvHMzFIoZ7jKBodjO5mCzWBcR7A4mpeAsdyiNBl2sTiZscSnNqxk61jVzP5Ba1D7XtOjjr7+3iqowrThj6BY40QqhYh/6BSY9fDzVZQiHnvlo6ZUM5kUK6OavZOovKlp5DIl5sGqoP0qAJnpQ4nhB2WVVsKfPlOXc+2KSsbJ23g9l8zaTMr+X0umlvfEKqyEl1Fa2L1dO0y/KFQ+ILmxcZLpRdq1hRAjd0quq9qGC8ucXhRWDg4hslVpau0da68g0aItWNez3mc5lB82b3dcZpFMzO41bgw7gvw10AvvTfQDqEYIuQ==
Description: The public key of the entity certificate.
entity_id
Example value: 0af807d7-3c39-43ef-9712-82bcfde1b9ca
Description: A unique identifier for the entity.
from_date
Example value: 1100-01-01T01:01:01.000Z
Description: The TimeStamp in the format: yyyy-MM-dd'T'HH:mm:ss.SSS'Z'
id
Example value: 5995d6a2-01b3-423c-a173-5481df49bdaf
Description: A string that, in combination with the bankId MUST uniquely identify the customer message on this OBP instance
jwt
Example value: eyJhbGciOiJIUzI1NiJ9.eyJlbnRpdGxlbWVudHMiOltdLCJjcmVhdGVkQnlVc2VySWQiOiJhYjY1MzlhOS1iMTA1LTQ0ODktYTg4My0wYWQ4ZDZjNjE2NTciLCJzdWIiOiIyMWUxYzhjYy1mOTE4LTRlYWMtYjhlMy01ZTVlZWM2YjNiNGIiLCJhdWQiOiJlanpuazUwNWQxMzJyeW9tbmhieDFxbXRvaHVyYnNiYjBraWphanNrIiwibmJmIjoxNTUzNTU0ODk5LCJpc3MiOiJodHRwczpcL1wvd3d3Lm9wZW5iYW5rcHJvamVjdC5jb20iLCJleHAiOjE1NTM1NTg0OTksImlhdCI6MTU1MzU1NDg5OSwianRpIjoiMDlmODhkNWYtZWNlNi00Mzk4LThlOTktNjYxMWZhMWNkYmQ1Iiwidmlld3MiOlt7ImFjY291bnRfaWQiOiJtYXJrb19wcml2aXRlXzAxIiwiYmFua19pZCI6ImdoLjI5LnVrLngiLCJ2aWV3X2lkIjoib3duZXIifSx7ImFjY291bnRfaWQiOiJtYXJrb19wcml2aXRlXzAyIiwiYmFua19pZCI6ImdoLjI5LnVrLngiLCJ2aWV3X2lkIjoib3duZXIifV19.8cc7cBEf2NyQvJoukBCmDLT7LXYcuzTcSYLqSpbxLp4
Description: JSON Web Token
logo_url
Example value: https://apisandbox.openbankproject.com/logo
Description: no-description-provided
other_account_routing_address
Example value: DE89370400440532013000
Description: OtherBankRoutingAddress string, eg IBAN value
other_account_routing_scheme
Example value: IBAN
Description: otherAccountRoutingScheme string, eg: IBAN
payload
Example value: {
"everything": false,
"account_access": [
{
"account_routing": {
"scheme": "OBP",
"address": "8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0"
},
"view_id": "owner"
}
],
"phone_number": "+44 07972 444 876",
"valid_from": "2022-06-14T12:42:00Z",
"time_to_live": 3600
}
Description: The whole create consent request json body.
paymentService
Example value: payments
Description: The berlin group payment services, eg: payments, periodic-payments and bulk-payments.
process
Example value: obp.getBank
Description: The format must be obp.xxxx, 'obp.' is the prefix, xxx will be the connector method name
redirect_url
Example value: https://apisandbox.openbankproject.com
Description: no-description-provided
roles
Example value: CanCreateMyUser
Description: Entitlements are used to grant System or Bank level roles to Users
services
Example value: [{"CY":["PS_010","PS_020","PS_03C","PS_04C"]}]
Description: The services provided by the entity.
tags
Example value: Create-My-User
Description: OBP uses the tags to group the endpoints, the relevant endpoints can share the same tag.
terms_and_conditions_url_example
Example value: www.example.com/xyz
Description: no-description-provided
to_date
Example value: 1100-01-01T01:01:01.000Z
Description: The TimeStamp in the format: yyyy-MM-dd'T'HH:mm:ss.SSS'Z'
view.description
Example value: This view is for the owner for the account.
Description: A description for this view.
vrp_consent_request.payload
Example value: {
"from_account": {
"bank_routing": {
"scheme": "OBP",
"address": "gh.29.uk"
},
"account_routing": {
"scheme": "OBP",
"address": "8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0"
},
"branch_routing": {
"scheme": "OBP",
"address": "DERBY6"
}
},
"to_account": {
"bank_routing": {
"scheme": "OBP",
"address": "gh.29.uk"
},
"account_routing": {
"scheme": "OBP",
"address": "8ca8a7e4-6d02-40e3-a129-0b2bf89de9f0"
},
"branch_routing": {
"scheme": "OBP",
"address": "DERBY6"
},
"limit": {
"currency": "EUR",
"max_single_amount": 1000,
"max_monthly_amount": 10000,
"max_number_of_monthly_transactions": 10,
"max_yearly_amount": 12000,
"max_number_of_yearly_transactions": 100
}
},
"valid_from": "2024-07-10T09:22:06Z",
"time_to_live": 3600
}
Description: The whole create consent request json body.
webui_props
Example value: webui_api_explorer_url
Description: WebUI Props are properties that configure the Web UI behavior and appearance. Properties with names starting with 'webui_' can be stored in the database and managed via API.
Data Sources:
1. Explicit WebUiProps (Database): Custom values created/updated via the POST /management/webui_props API endpoint and stored in the database. These take highest precedence.
2. Implicit WebUiProps (Configuration File): Default values defined in the sample.props.template configuration file located at obp-api/src/main/resources/props/sample.props.template.
To set config file defaults, edit sample.props.template and add or modify properties starting with 'webui_'. Both commented (#webui_) and uncommented (webui_) properties are parsed, with the # automatically stripped.
When calling GET /management/webui_props:
- Without 'active' parameter or active=false: Returns only explicit props from the database
- With active=true: Returns explicit props + implicit (default) props from configuration file. When both sources have the same property name, the database value takes precedence. Implicit props are marked with webUiPropsId = 'default'.
Precedence order (highest to lowest):
1. Database WebUI Props (set via POST /management/webui_props)
2. Props files (default.props, etc.) - standard application config
3. sample.props.template - returned as defaults when active=true
4. Environment variables can also override props
Examples of webui props include: webui_header_logo_left_url, webui_api_explorer_url, webui_api_manager_url, webui_sandbox_introduction, etc.